Japan Security Analyst Conference 2021 -3rd Track-
JPCERT/CC held Japan Security Analyst Conference 2021 (JSAC2021) on 28 January 2021. It was the first JSAC held online in consideration of the participants’ health and safety in the current COVID-19 pandemic.
The conference is aimed at providing opportunities for them to get together and exchange their technical knowledge on incident response and analysis. This is JPCERT/CC’s 4th time holding this annual conference, and 11 presenters were selected from 22 candidates.
To adjust the event for the virtual setup, we opened 3 parallel tracks for the first time, and the participants were free to move between the tracks. Not only presentations but also workshops were held in the 2nd and 3rd track. The event’s Slack channel was open for questions and answers, and the presenters and participants exchanged their ideas and opinions very actively.
The slides and other information of each presentation are available on JPCERT/CC Website either partially or entirely.
This blog post reports on the 3rd track of the conference, and 2 more posts will follow to cover the rest.
LuoYu, the eavesdropper sneaking in multiple platforms
Speaker: TeamT5 Shui Lee,Leon Chang
TeamT5 reported on a new Chinese APT group Luoyu, whose activity has been observed since 2014.
Based on Luoyu’s attack features, TeamT5 considers it is a Chinese attack group which targets tech companies, media, educational institutions, and other industries in China, Hong Kong, Japan, South Korea, and Taiwan. Its activity has been observed in China since 2014.
Luoyu targets various platforms such as Mac, Linux, Windows, and Android, using malware ReverseWindow, WinDealer, and SpyDealer.
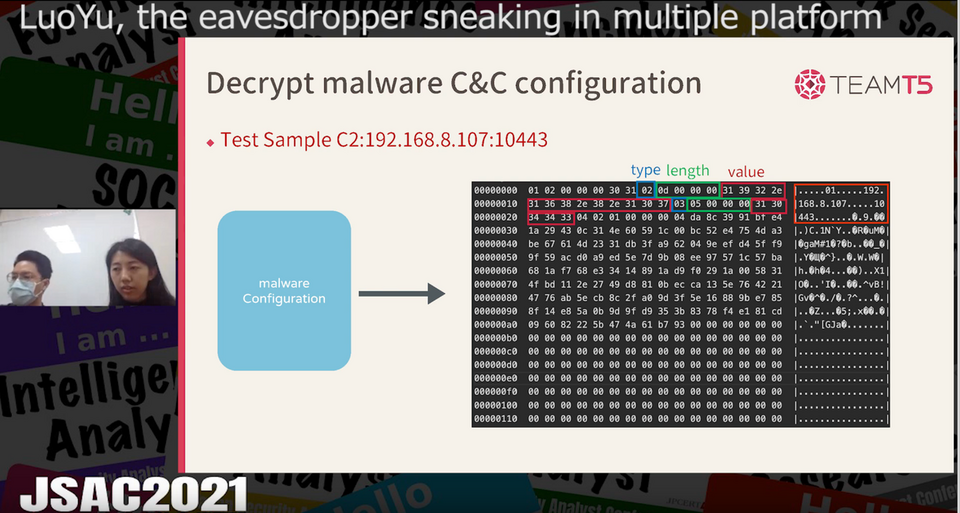
The presentation focused on a detailed description on ReverseWindow. The victims’ information is arranged in TLV (type-length-value) format and then encoded in DES algorithm with a hard-corded key before the malware sends it to the C&C server. The commands used are basically identical across different platforms except some unique ones developed for a specific platform.
The speakers also showed the historical transition of ReverseWindow. In 2017, attackers started to use the malware to attack IT companies in Japan, South Korea, and Taiwan and researchers at university in Hong Kong. In 2019, a new type of ReverseWindow that targets Android devices was developed, and there is a case in which the malware was used to keep political dissidents under surveillance.
In the Q&A session, TeamT5 was asked how it reached the conclusion that these different types of malware are under the same family. Shui answered that they identified the malware family because all the malware samples were connected to the same C&C servers.
Shuffle the SOC - automating anything, anytime, anywhere
Speaker: Fredrik Oedegaardstuen
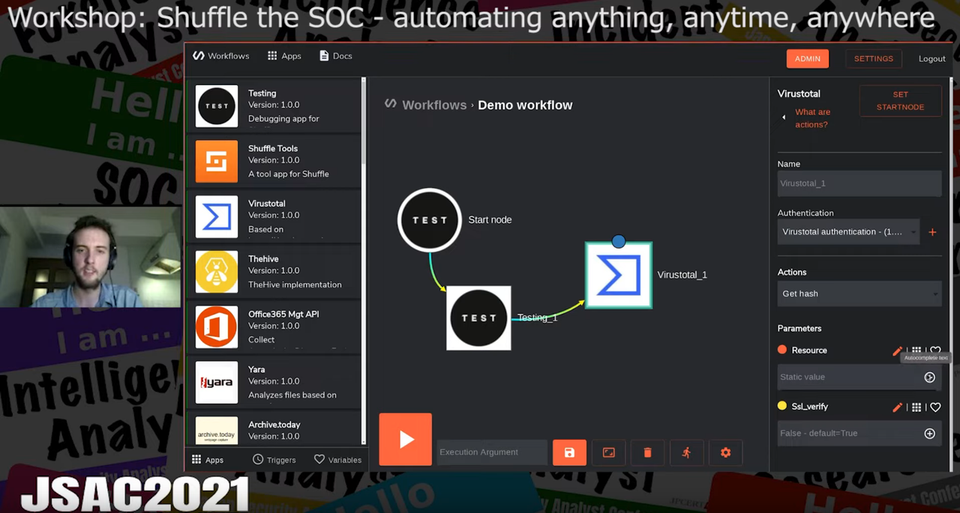
Fredrik introduced Shuffle, an open source automation platform for security tasks. It is called SOAR (Security Orchestration, Automation, and Response) tool, and users can perform service linkage, migrate Python codes, and do other tasks without having to program to automate their services. Shuffle’s GUI helps the users create a workflow that involves APIs of various security Web services.
Fredrik first gave a brief description of how Shuffle works. Its workflow consists of event nodes, which the users can configure with parameters and variables in JSON format. Each node supports a variety of actions such as “save,” “view,” and “send feeds to another app,” and the users can even build a flexible flow by giving event nodes conditions to have them act differently depending on the situation. Shuffle also can be operated on Docker as a Web service, and thus multiple users can easily access and use it with their Web browser.
The participants of the workshop learned how to create an account, build a workflow, and relate and configure event nodes. They also tried sending their file’s hash value to VirusTotal event node in JSON format to receive the detection result.
Fredrik said Shuffle can automate some of the tasks in general SOC operations. He said, for example, the tools can automatically detect malware attached to emails using VirusTotal and email the detection result to the operator. He also added that the users can create an application and upload it to a Web server with Shuffle. I think we should pay attention to the future updates of Shuffle.
Hunting Threat Information on Attack Campaign targeting Cryptocurrency Operators
Speaker: Tateki Kodera (Internet Initiative Japan Inc.)
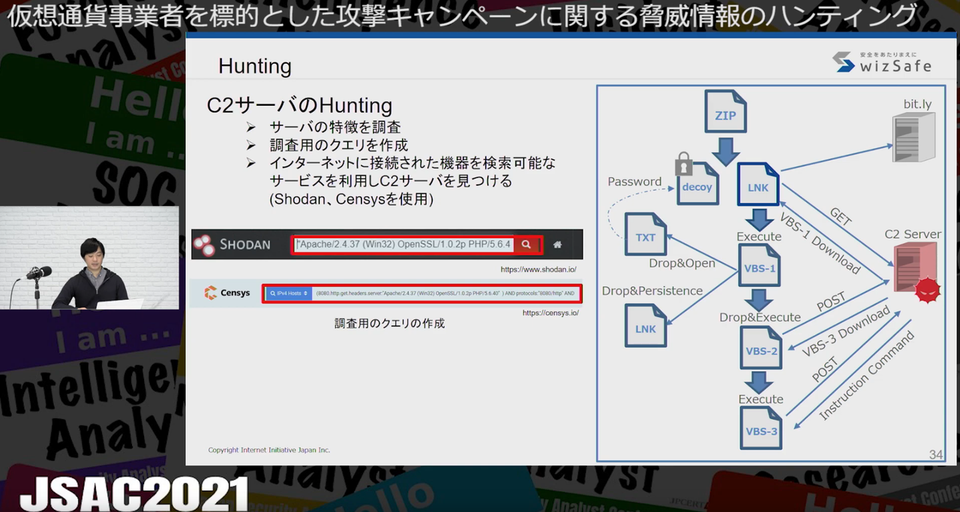
In the presentation, he described the method to hunt threat information on attack campaign, in which a LNK file is leveraged, against cryptocurrency operators. He showed how to find the uploaded file using Yara rules on VirusTotal and then how to use the file to hunt the C&C server.
In the past case, he investigated using the information on command lines and executed parameters (shortened URL of the communication destination). He detected 29 malware samples and found the domains of a new C&C server. In some cases, LNK files were uploaded just several hours after the shortened URL had been generated, and thus he said this method is useful in getting fresh information. In another research, he used Shodan and Censys focusing on the distinctive information of known C&C servers such as server header, status code, title, and favicon. He eventually found12 new C&C servers during the 9 months from April to December 2020.
In this way, he demonstrated his hunting method is useful in finding malware and servers that attackers used as well as the changes made to them.
In Closing
This report covered the 2 presentations and a workshop in the 3rd track of JSAC2021.
We will report on the 2nd track in the next blog post.
Yuma Masubuchi
(Translated by Takumi Nakano)

