Further Updates in LODEINFO Malware
The functions and evolution of malware LODEINFO have been described in our past articles in February 2020 and June 2020. Yet in 2021, JPCERT/CC continues to observe activities related to this malware. Its functions have been expanding with some new commands implemented or actually used in attacks. This article introduces the details of the updated functions and recent attack trends.
LODEINFO versions
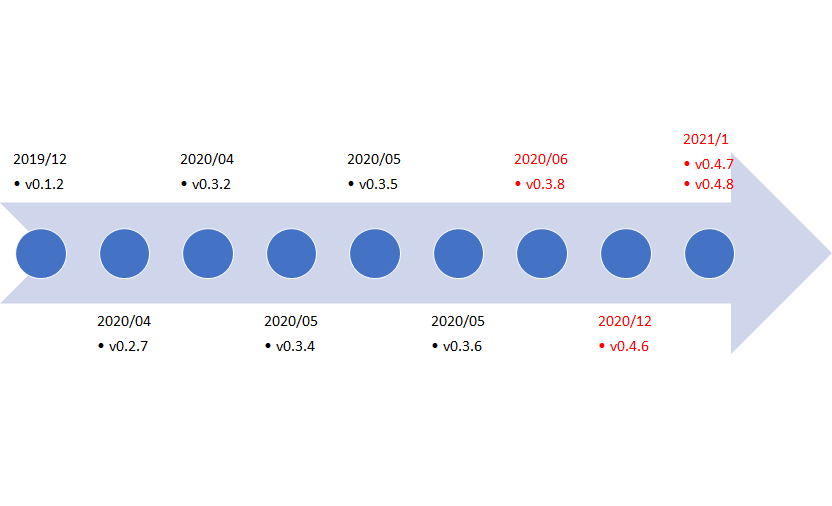
At the time of the last blog update, the latest version of LODEINFO was v.0.3.6, and currently v0.4.8 is being used. Figure 1 shows the transition of LODEINFO versions based on JPCERT/CC’s observation.
Decoy document
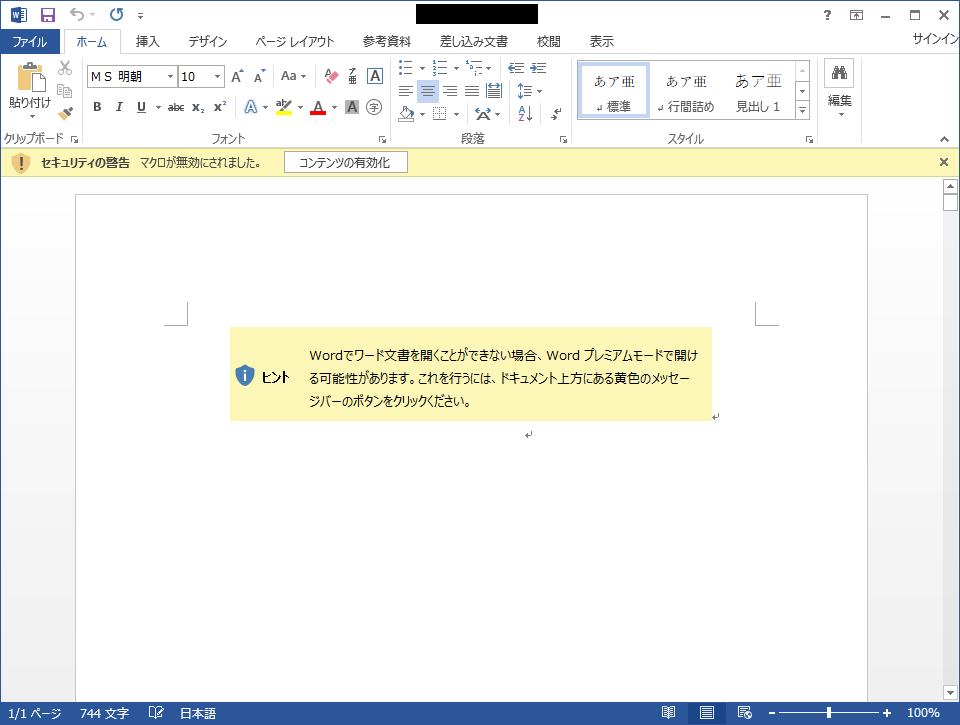
As we previously explained, LODEINFO infection spreads once a user enables the macro in a Word or Excel file attached to a spear phishing email. In some recent cases, these document files are protected with a password, which is specified in the email body. The Word document convinces the user to enable the macro as in Figure 2. (The statement in the yellow box is roughly translated as follows: In case Word application cannot open the document properly, you may be able to open it with Word premium mode. To proceed, please click the button in the yellow message bar above.)
The document appears to be empty, however, there are hidden letters in small and white fonts, containing macro configuration values and BASE64-encoded strings of a zip file which stores LODEINFO.
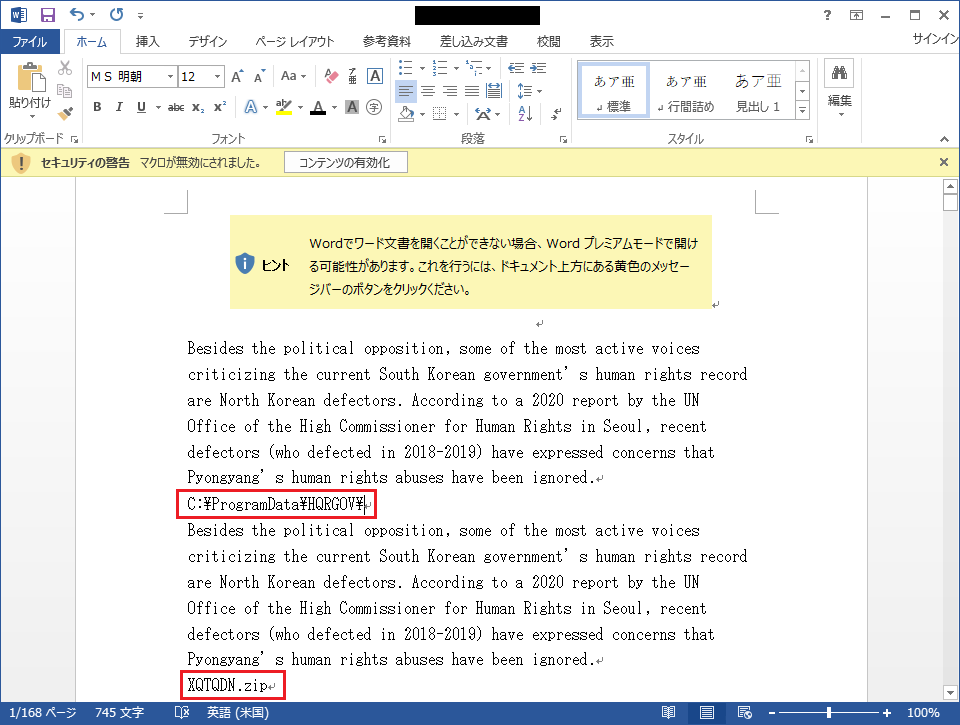
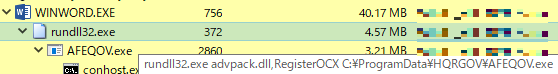
The macro uses a method called LOLBAS to execute LODEINFO. Below is the command for executing a file created.
rundll32.exe advpack.dll,RegisterOCX
The code of the macro contained in the documents shows sentences in public articles related to the diplomatic relations between South Korea and Japan or North Korea in the comments.
New commands
The latest LODEINFO v0.4.8 has the following additional commands compared to v.0.3.6. (See Appendix A for details.)
- ransom (implemented)
- keylog (implemented)
- mv
- cp
- mkdir
- ps
- pkill
The following sections describe some of the new features that are available in the newer versions.
Ransomware function
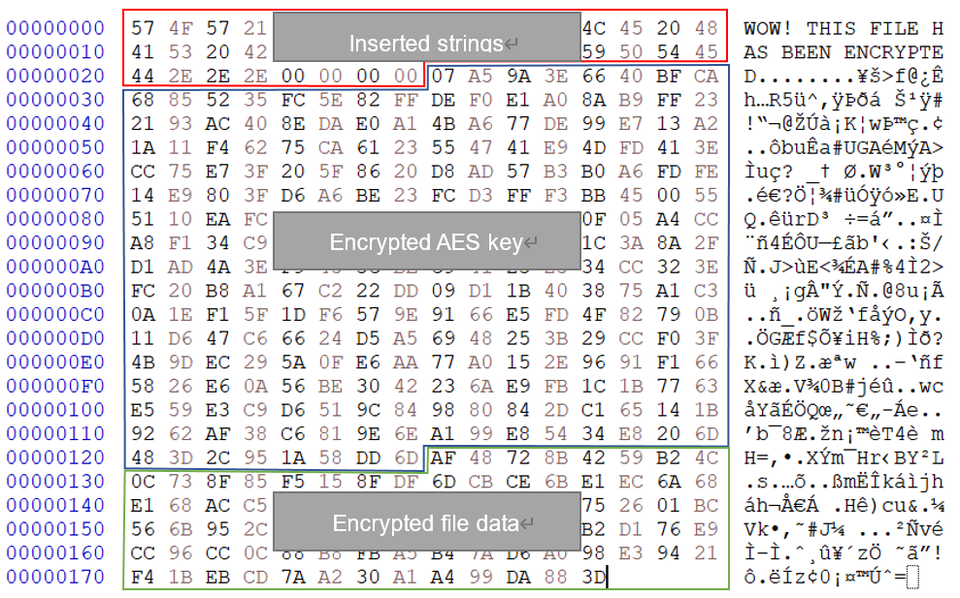
“ransom” command has been implemented in v.0.3.8 and after. The encryption algorithm is a combination of AES and RSA. The files are first encrypted with an AES key generated for each fille. The key is then encrypted with the RSA public key embedded in the malware. After that, the message “WOW! THIS FILE HAS BEEN ENCRYPTED...” is inserted in the beginning of the file.
This process makes it difficult to decrypt the files. Files and folders to encrypt can be specified with the ransom command, however, those with file extensions and paths in Figure 7 are excluded.
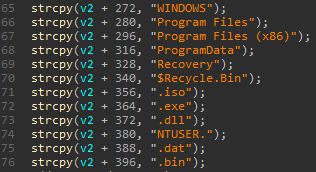
In case a folder is selected, its path name is checked against the list, but not the individual files inside the folder. Therefore, files including these names listed above are encrypted in this case. Unlike other types of common ransomware, alteration of file extension, creation of ransom notes and/or change of background image do not occur. JPCERT/CC has not yet observed these features in actual attack cases, but they may be used for the purpose of deleting evidence or exfiltrating data.
Keylog function
“keylog” command has been implemented in v.0.4.6 and after. This command checks the following registry value to see if the option is enabled.
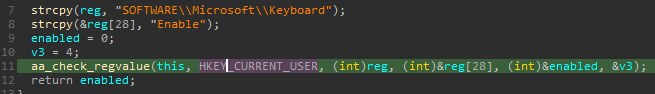
If it is enabled, a file named “<NetBIOS name>.tmp” is created in %TEMP% folder, and stolen key strings are encoded and stored there. An XOR key is used for encoding, which contains the first 1 byte of the SHA512 value of the device’s NetBIOS name. The following is an example of code to decode the keylog file.
import os
import hashlib
name = os.getenv("COMPUTERNAME")
keylog_file = os.getenv("TEMP") + "//" + name + ".tmp"
hash_of_name = hashlib.sha512(name.encode("UTF-8")).hexdigest()
xor_key = int(hash_of_name[0:2], 16)
decode_data = bytes()
with open(keylog_file, "rb") as f:
for ch in f.read():
decode_data += (ch ^ xor_key).to_bytes(1, byteorder="big", signed=False)
print(decode_data.decode('shift_jis'))
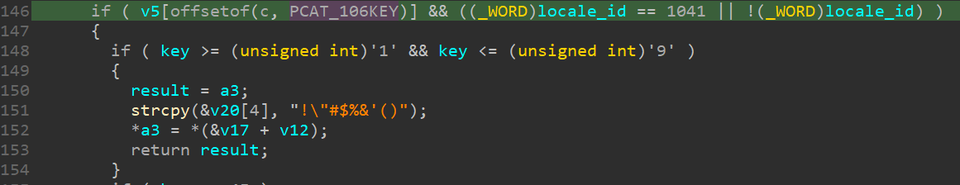
One of the distinctive features of this function is that it checks if the device’s keyboard layout is set to Japanese according to the following criteria:
- “OverrideKeyboardIdentifier” value in HKLM\SYSTEM\CurrentControlSet\Service\i8042prt\Parameters is set to “PCAT_106KEY”
- “GetKeyboardLayout” function returns “1041”
If the device uses the Japanese keyboard layout, the key strings are converted accordingly. This fact implies that the attackers using LODEINFO malware target Japanese language users.
In closing
Attacks using LODEINFO has been continuously observed, and it is considered as a severe threat. We will keep an eye on this activity as it is yet likely to continue.
The hash value of the sample described in the article is listed in Appendix B, together with some newly confirmed C&C servers in Appendix C. Please make sure that none of your devices is communicating with such hosts.
- Kota Kino
(Translated by Yukako Uchida)
Reference
Appendix A New commands
Value |
Contents |
|---|---|
| ransom | Encrypt files |
| keylog | Control keylogger |
| mv | Move files |
| cp | Copy files |
| mkdir | Create directory |
| ps | List process |
| pkill | Kill process |
Appendix B SHA-256 has value of a sample
- 3fda6fd600b4892bda1d28c1835811a139615db41c99a37747954dcccaebff6e (v0.4.6)
Appendix C C&C servers
- www.evonzae.com
- 45.76.216.40
- 103.140.45.71
- 139.180.192.19
- 167.179.84.162
- 167.179.65.11

