Japan Security Analyst Conference 2021 -2nd Track-
This blog post focuses on the 2nd track of JSAC2021, following the previous report on the 3rd track.
Workshop: Malware Analysis at Scale - Defeating EMOTET by Ghidra -
Speaker: Shota Nakajima (Cyber Defense Institute), Hiroaki Hara (Trend Micro)
Slides (Japanese)
Video
Shota and Hiroaki presented how malware analysis can be easily done using Ghidra, an open source reverse engineering tool, and the participants tried automating the analysis of Emotet during the hands-on training.
Ghidra provides its API (Ghidra API), and the users access Ghidra’s features from their script to automate and optimize various operations:
- Manual operations such as searching byte strings and commenting
- Repeated operations such as importing and analyzing a large amount of file
- Analysis like decrypting encrypted data and strings
- Execution on emulator
Using Ghidra API, the participants tried creating some scripts for operations such as decrypting obfuscated codes, identifying malware configuration from the decryption result, and extracting the C&C server information.
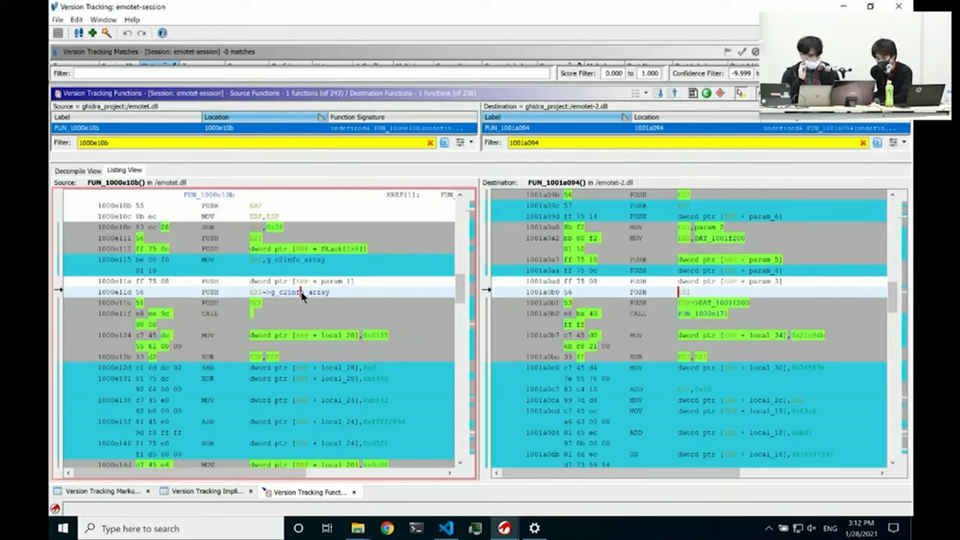
At the end of the hands-on training, the speakers introduced Ghidra’s Version Tracking feature so that the participants can use their script for other types of malware. The users can compare binaries of multiple samples and spot the differences with this feature.
The participants tried comparing two different samples of Emotet and updated the scripts so that they can identify the configuration from the same command strings and extract the C&C server information.
The Ghidra scripts used in the workshop are available at GitHub.
GitHub AllsafeCyberSecurity
https://github.com/AllsafeCyberSecurity/malware-analysis-at-scale-defeating-emotet-by-ghidra
Knock, knock, Neo. - Active C2 Discovery Using Protocol Emulation -
Speaker: Takahiro Haruyama (VMware)
Slides (Japanese)
Video
Takahiro introduced the method to find Cobalt Strike’s working team servers directly on the Internet.
First, he described the details of the following protocols:
- Client authentication protocol
- Stager protocol
- Beacon protocol
- External C2 protocol
In this method, analysts download Beacon using Stager protocol, which Cobalt Strike uses, and extract configuration from the Beacon. Threat intelligence can be collected without false detection by implementing the scanner with the configuration parser. He also detailed how to implement these scanner, configuration, and parser.
He next introduced the method to find Cobalt Strike’s team servers on the Internet, with points to note when creating a list of open hosts.
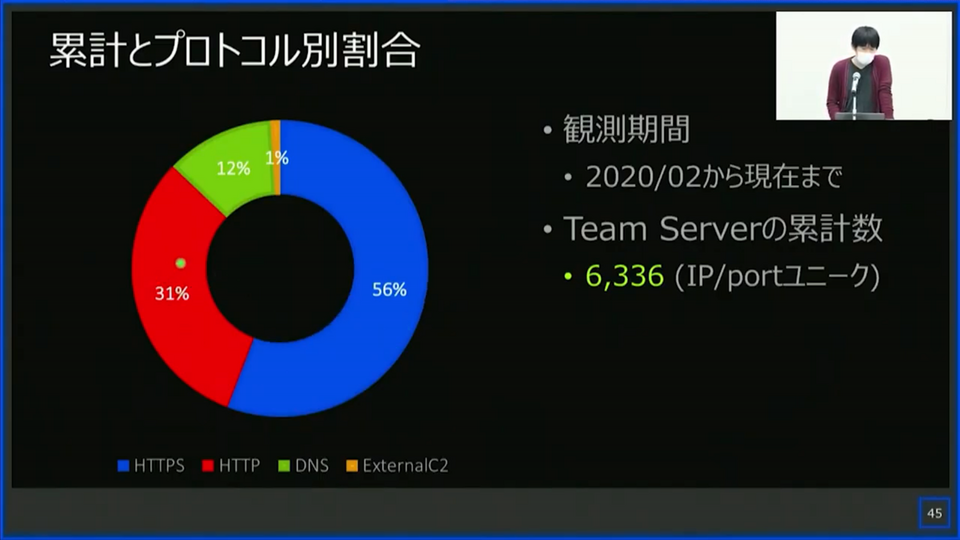
At the end of the presentation, he showed the analysis result based on the threat intelligence he had collected since February 2020. He said HTTP and HTTPS account for 80% of the protocols the attackers used and that the leak/crack version takes up 50%. He also shared his categorization of attackers based on unique values extracted from configuration, together with the IoC of their C&C servers.
The IoC shared in the presentation are available at GitHub.
GitHub Carbon Black
https://github.com/carbonblack/active_c2_ioc_public/tree/main/cobaltstrike
A41APT case - Analysis of the Stealth APT Campaign Threatening Japan
Speaker: Yusuke Niwa, Motohiko Sato, (Itochu), Hajime Yanagishita (Macnica Networks), Charles Li (TeamT5), Suguru Ishimaru (Kaspersky Labs Japan)
Slides
Video
In this presentation, the speakers shared their findings on A41APT, an APT campaign that has been observed since March 2019.
A41APT has the following characteristics:
- Active since March 2019 to the present (January 2021)
- Targets Japanese companies and their overseas branches
- Exploits SSL-VPN in the initial intrusion, unlike traditional spear-phishing
- Uses new types of malware which exploits DLL such as SodaMaster, P8RAT, DESLoader, and FYAntiLoader
- Very little information is publicly available
- Very stealthy and hard to find
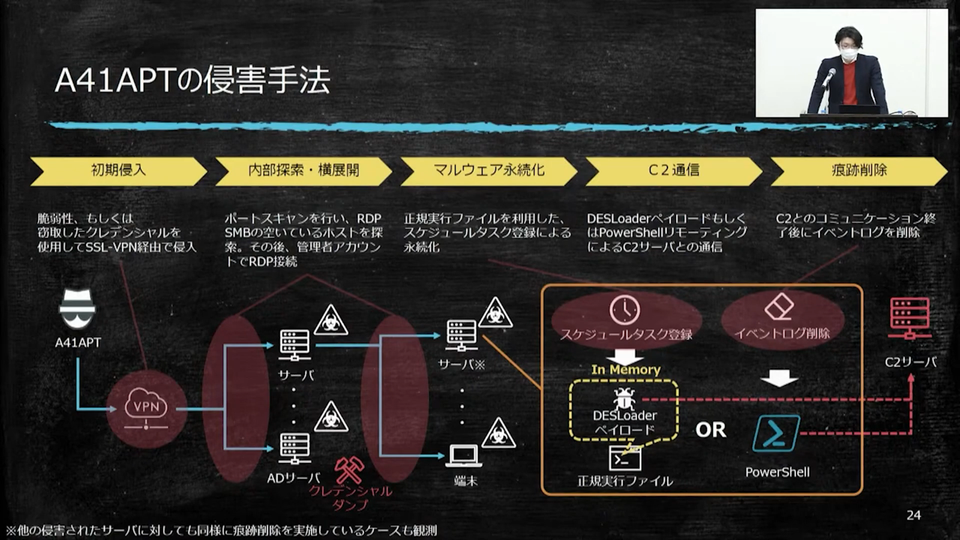
A41APT makes its initial intrusion through SSL-VPN, leveraging vulnerabilities or stolen credentials. Then DESLoader’s payload or PowerShell remoting is used to communicate with the C&C servers. The speakers named this campaign after the host name observed in this initial intrusion with SSL-VPN products, “DESKTOP-A41UVJV.”
Next, the speakers gave a detailed description of DESLoader and its payload used in the attacks. Using DLL side-loading, DESLoader decrypts multiple encrypted PE and shellcodes on memory in phases and runs the payload once it is ready. The characteristics of the payload (SodaMaster/P8RAT/FYAntiLoader/xRAT/Stager Shellcode) and other new findings were also shared.
The speakers also shared attackers’ infrastructure such as their C&C servers and host names.
It was confirmed that the following host names were used in intrusions in the past:
- DESKTOP-A41UVJV
- Dellemc_N1548P
Finally, the speakers discussed the attribution of this APT group, relating it to APT10 and BlackTech.
They consider that A41APT is possibly related to APT10 because the initial version of SodaMaster was used in the APT10’s attack campaign against Turkey. The public information also shows that these two APT groups share the unique strings in their TTPs. Meanwhile, the speakers also consider that A41APT is possibly related to BlackTech, which uses TSCookie and SodaMaster, because these types of malware collect the same kind of information as A41APT does. Furthermore, the malware was also found on multiple devices that A41APT had compromised, and also these groups had same targets in the past.
In Closing
This report covered the 2 presentations and a workshop in the 2nd track of JSAC2021.
See you in the next blog post on the 1st track.
Yuta Fuchikami
(Translated by Takumi Nakano)

