ICS Security Conference 2024
JPCERT/CC held the annual ICS Security Conference 2024 on 7 February 2024. The conference aims to share the current status of threats to ICS both in Japan and overseas and the efforts of stakeholders in the field, as well as to help participants improve their ICS security measures and establish best practices. The conference started in 2009 and is now in its 16th year.
This was the 4th time the event was held online, and 419 people from all over Japan attended the conference. This article describes the opening and closing speeches and the 7 presentations.
Opening Remarks
Masahiro Kamimura, Deputy Director-General for Cyber Security and Information Technology, Ministry of Economy, Trade and Industry (METI), gave opening remarks.
He said, in recent years, the cyber and physical spaces have become more integrated, and ICS is no exception. ICS have become more sophisticated and convenient thanks to digital and network technologies. At the same time, risks arising from cyber attacks are increasing. He noted that the scope of security targets that should be risk-managed from the perspective of BC (business continuity) and SQDC (safety, quality, delivery, and cost) and management has expanded beyond the traditional CIA (confidentiality, integrity, and availability) assurance.
He then introduced METI’s Cyber Security Management Guidelines Ver 3.0 Collection of Practices, 4th Edition, and the Guidelines for Cyber and Physical Security Measures in Factory Systems, which are currently being adapted for smart factories.
As recent international trends, he introduced the European Cyber Resilience Act (CRA), the Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) in the U.S., and the concept of “Secure by Design” and “Secure by Default” by like-minded countries such as the U.S., Europe, and Japan. He said that they are different from traditional measures that have relied heavily on the user side, and that there is a growing emphasis on the idea that the manufacturer and supplier side should also take responsibility for more secure and safe product development and vulnerability management. He also introduced various initiatives in Japan, such as the establishment of a security compliance assessment system for IoT devices and a policy to help vulnerability management following the guidance on introducing Software Bill of Material (SBOM) for software management.
He mentioned the importance of proper information sharing to understand the whole picture of attacks and prevent damage from spreading as cyber incidents become increasingly sophisticated and complex. He then introduced guidelines and guidance for facilitating information sharing between security professional organizations supporting victim organizations, based on guidelines issued by the government that can be used as a practical reference for sharing damage information.
ICS Security Today and Tomorrow - A Review of the Past Year
Speaker: Toshio Miyachi, Expert Adviser, JPCERT/CC
<Slides (Japanese)>
Toshio reviewed overall trends in ICS security in 2023 and discussed the major changes surrounding ICS security.
He first mentioned that in 2023, the amount of ransomware damage had increased by 50 percent compared to the previous year. Overseas subsidiaries of Japanese companies also became victims, and the manufacturing industry was most targeted. He also mentioned changes in attack methods and the fact that ransomware is increasingly becoming a hot political issue.
He also described a situation where cyber attacks have intensified along with Russia’s invasion of Ukraine and the war between Hamas and Israel in the Middle East. As examples of related incidents, he discussed GPS signal disruption attacks, several cyber attacks in the Middle East region, and a cyber attack on a water supply facility in the U.S.
Regarding trends in vulnerabilities in ICS-related products, the number of vulnerability advisories published by CISA (ICS-CERT)[yu3] in the U.S. has reached a ceiling in recent years, probably due to the processing capacity of vulnerability handlers, and there are many cases of vulnerabilities inherited through the product development supply chain that remain unaddressed. He also introduced the movement centered on the U.S. to promote SBOM as a countermeasure to address this problem.
He then moved on to trends in standardization and certification, as well as developments in regulation and public guidance. The National Cyber Security Strategy published in the U.S. shows a shift in policy from traditional measures focused on product users to making product providers responsible as well. Regarding IEC 62443 standard, two documents were published, and one of them, IEC 62443-2-4:2023, defines security program requirements for service providers.
In the concluding section, he discussed security at a time when ICS began transforming with the adoption of recent technologies. In recent years, more ICS have been operated remotely or outsourced to supplement the shortage of skilled operators, and more ICS are being operated in combination with AI and other advanced information processing, making connections to cloud environments and other systems indispensable. Various research activities are being conducted to develop security measures that match such changes in ICS. For example, “BES Operations in the Cloud” by North American Electricity Utilities Council (NERC) attempts to conceptually organize the challenges associated with controlling electricity transmission systems on the cloud. Finally, the main ICS security-related research reports published in 2023 and their overviews were also presented.

Cyber security risks in CNC machines in the industry 4.0 era
Speaker: Katsuyuki Okamoto, Security Evangelist, Trend Micro Inc.
<Slides (Japanese)>
Katsuyuki presented the results of actual demonstration tests on cyber security risks in CNC machines (computer numerically controlled machine tools) in the Industry 4.0 era, and suggested security perspectives that end-users and other stakeholders should consider and the direction to take in the future.
First, he described CNC machine tools. He said that CNC machine tools are mainly divided into the machine itself and the controller that performs the computer numerical control, and that in the CNC machine tool supply chain, there are NC manufacturers who create the controllers, machine manufacturers who create the machines themselves, machine promotion businesses, integrators and end-users. He also mentioned that some organisations have multiple roles, such as manufacturing and sales. In addition, he noted that in this demonstration, 4 products from global, large-scale vendors were evaluated using the same criteria, including ‘Industry 4.0-ready’ technology, remote security assessment using automated vulnerability scanners, and verification of each vendor’s unique technologies. A set of experimental items had been created to simulate the intentions of actual attackers: compromise, damage, DoS, hijacking and information theft.
He said remote attacks had been successful on controllers from all four companies, achieving almost all of the attack objectives, indicating that authentication and past vulnerabilities were the cause of the successful breaches. He pointed out that security has not yet caught up with ‘Industry 4.0,’ as the targeted devices do not have authentication or access control to resources and used previous versions of the operating system.
He concluded the presentation by saying that end-users and integrators should consider CNC machine tool security by understanding that these can also be breached, correctly identifying attack surfaces and implementing appropriate countermeasures. He also suggested improving the visibility of the ICS/OT environment as the direction to take in the future.
Monitoring communications in OT environments from an attacker’s perspective - Let’s start from a small start -
Speaker: Koji Yasui, Principal Consultant, OT Security Group, Technology Management Department, Cyber Defence Institute, Inc.
<Slides (Japanese)>
Koji presented a communication monitoring method for OT environments using OSS as a small start for those who want to know whether there are any signs of penetration in the OT environment they are involved in.
He first mentioned the reasons why communications monitoring is a good match for the OT environment: the effectiveness of security measures is visible; there is no impact on availability; and monitoring can be performed as an extension of daily inspections. He then suggested a small start for the initial introduction of network monitoring, in order to resolve issues such as the excessive cost and the selection of the necessary functions.
Next, he explained how to use the OSS tool Arkime for monitoring as a small start, and introduced the kind of penetration signs that can be detected using actual communication monitoring with a simulated control system as an example, as well as providing hints on how to operate monitoring in an OT environment.
Finally, he said that the examples presented are basic content for a small start, and he hoped that by trying them out, the participants can better understand their organization’s system assets and communications, which would help them gain a basic knowledge for selecting communication monitoring products.
Challenges and global examples of vulnerability management in ICS
Speaker: Shunsuke Kato, Solution Engineer, Claroty Ltd.
<Slides (Japanese)>
Shunsuke explained the challenges of managing vulnerabilities in ICS and presented examples of global responses.
First, as to the situation and importance surrounding vulnerability management, he explained that attacks that exploit vulnerabilities in ICS have environmental, economic and safety impacts, and that although there had been successful attacks, such as Stuxnet in 2010, which exploited ICS vulnerabilities at controller level, the attacks were backed by nation states and requires a lot of financial resources. However, he noted that the introduction of Pipedream, the attack tool targeting vulnerabilities in ICS, reported by CISA and others in April 2022, has made it easier to conduct attacks that exploit ICS vulnerabilities. In response to this situation, vendors are actively disclosing vulnerability information, and regulations and guidelines increasingly require vulnerability management.
Next, using actual vulnerability information as an example, he listed some challenges in vulnerability management. First, he stated that a detailed asset register needs to be prepared in order to link vulnerability information to the assets owned. Following up on information that has been added or modified after the linking of vulnerability information is difficult to perform manually, and thus it is reasonable to introduce a tool. He also mentioned that policies and guidelines are needed to prioritize the response to vulnerability information.
He concluded by introducing an example of a global response to the aforementioned issue, in which an asset visualization tool can be used to automatically link and track vulnerabilities with asset inventories based on actual data. As a guideline for prioritizing vulnerability responses, he introduced a method of prioritizing vulnerability information that can actually be exploited, such as the EPSS published by FIRST and KEV published by CISA. As examples of actual vulnerability responses, in addition to essential countermeasures such as patching and firmware updates, he introduced a response called virtual patching, in which attack commands that exploit vulnerabilities are registered as signatures and implemented into IPS. In addition, he discussed a countermeasure called “micro-segmentation,” in which communication policies between segments are configured. He said that it is more realistic to use correction control as part of network security than to deal with it on the main unit side.
Assistance in implementing ICS security policy in the field
Speakers: Fumitou Masaki, Global Cybersecurity Manager, Digital & IT Division, Santen Pharmaceutical Co., Mitsutaka Hori, Industrial Control System Security Response Group, JPCERT/CC
<Slides (Japanese)>
Fumitou and Mitsutaka presented the background and overview of how they created a document that would serve as a reference for implementing security measures while considering the unique circumstances of ICS, in order to address the issue that it takes a great amount of effort to implement ICS security policy in the field after it has been established.
They first described the challenges seen from both JPCERT/CC and Santen regarding the ICS security policy. In order to have ICS operators implement security measures, they indicated the following 3 challenges: “making sure that people in charge at the manufacturing site understand the importance of the ICS security policy,” “incorporating rules based on the ICS security policy into daily operations,” and “clarifying who and how to be involved in order to comply with the ICS security policy.” Since solving these issues is very labor-intensive, they considered creating a document that would be specific to the reality of the manufacturing site and summarize what ICS operators need to do to comply with the policy. They also said that they will first prepare a version for the pharmaceutical industry, and then adjust the content for the general manufacturing industry.
Next, an overview of the document was presented. He stated that the intended audience for the document was security personnel in ICS user organizations that have already established ICS security policies, and that the document was intended to help solve the above-mentioned issues by “promoting understanding of ICS security among various manufacturing site personnel,” “creating rules necessary for ICS operators to comply with the policies,” and “organizing actions to be taken by other plant personnel for ICS operators to comply with the policies.” The scope of the document and the systems envisioned were set as follows: “a guide to the embodiment of the policy in the field,” which covers seven control items involving ICS operators, such as external storage media and brought-in PCs, and explains the use cases, risks, etc. for each item; “action list for each character” in Excel format that describes what each person in charge, classified into six characters such as ICS operators and plant equipment personnel, does and also allows status management, as a reference for building an operational flow when ICS operators comply with the rules; “Awareness Tests” for use in e-Learning. For each of these documents, he stated that each ICS user organization can select and discard the documents so that they can start where they can.
Finally, a roundtable discussion was held on the theme of this year’s activities, and the participants discussed the points they focused on during the creation of the document, the key points of its utilization, new issues found during its creation, and future developments. They said that the final document for the general manufacturing industry is scheduled to be released by the end of the fiscal year 2023, and that the addition of appendices and the creation of an English version will be considered in the next fiscal year.

Preparing for ICS-related Security Incident Response - Challenges in developing a response system and the first steps, based on the examples from manufacturing industry -
Speaker: Kazuyuki Kono, Manager, Industrial Control System Security Response Group, JPCERT/CC
<Slides (Japanese)>
Kazuyuki introduced the challenges in preparing for ICS-related security incident response and the first steps to take, using the manufacturing industry as an example.
First, he described the changes in cyber threat landscape surrounding ICS based on the damages in recent years. In the past, cyber threats to ICS were attacks that directly affected ICS/OT by ICS-specific malware. However, while it has been thought that this is not so easy to happen, many of the recent cases in which ICS was considered to be affected were caused by ransomware. He said that it is now possible to conduct cyber attacks that indirectly affect ICS, such as production shutdowns, without having in-depth knowledge of ICS.
Next, he discussed the results of the questionnaires at the past two ICS security conferences held by JPCERT/CC and the recent consultations with the organization and introduced the possibility that interest in SIRTs (Security Incident Response Teams) in ICS is increasing more than ever. The common theme of the consultations was “preparation for ICS-related incident response,” and he said that the aforementioned cyber threats to ICS may be a factor in the increased interest in establishing SIRTs for ICS. With this increased interest, SIRTs targeting ICS need to be aware of cyber threats that not only indirectly affect ICS, such as the aforementioned ransomware, but also direct cyber threats to ICS, such as the recent Sandworm cyber attack on a power substation in Ukraine and the cyber attack on a substation in Denmark.
Based on these points, he next introduced key points for ICS security personnel to properly build a SIRT targeting ICS. In general, building a SIRT requires major organizational and functional requirements, but most of the published references are on CSIRTs that seem to assume incident response in information systems, and only a few of them include points that consider ICS. Therefore, ICS security personnel are in a state of exploration when considering the establishment and operation of SIRTs that consider ICS. He introduced JPCERT/CC’s new community activities in response to the need for a community to address various common issues among ICS security personnel. The community is hosted by JPCERT/CC, and more than 20 organizations from multiple industries in the manufacturing sector are participating, and practical considerations in ICS security measures are made by the practitioners responsible for ICS security. As an example, he introduced the study of ICS-specific events that should be assumed cyber-related and efforts for early detection of these events within organizations. He also invited the audience to join the community. In addition, there was a call for ICS vendors/engineers who are struggling to address ICS-related vulnerabilities in their product delivery or with the asset owners to exchange opinions and promote ICS security measures in collaboration with JPCERT/CC.

Incident response training that ICS-related SIRTs want to engage in on a daily basis, discussed by practitioners from 10 manufacturing companies
Speaker: Tokinori Obayashi, Information Security Department, Shiseido Company, Limited
Panel Discussion: Takuya Shibata, Sekisui Chemical Co., Naoki Ochi, Panasonic Automotive Systems Co.
<Slides (Japanese)>
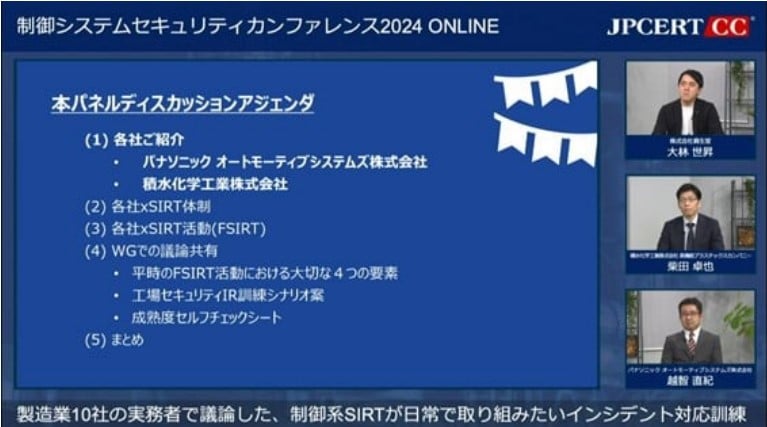
Tokinori introduced the activities and deliverables of the working group dedicated to incident response training, which was established within the “Community of ICS Security Professionals in the Manufacturing Industry” organized by JPCERT/CC, with a panel discussion.
He first explained the background behind the launch of the WG as an introduction.
Shiseido has been conducting IR training for factory security, which has been very well received, with many comments in the post-training questionnaire requesting to take different scenarios on a regular basis. On the other hand, it is difficult to prepare IR training from scratch. He thought that although some organizations may want to try IR training, they may not be able to implement it due to the difficulty of preparation. Therefore, they brought together the experiences and threat information of the companies concerned and then invited participants for a WG on the theme of IR training at the “ICS Security Community for Manufacturing Industry” hosted by JPCERT/CC. As a result, 10 companies participated and the “FSIRT Training Group” was established. He said that the main focus of the activity was to propose IR training that can be easily implemented in the daily operations, incorporating opinions from operating companies with manufacturing sites. He also mentioned that they had held several meetings to discuss various security issues, including the main topic, and created as deliverables: (1) draft scenario materials for factory security IR training and (2) a proficiency level self-check sheet after factory security IR training exercises.
Next, in the panel discussion, the SIRT system and its activities were first discussed as each company’s factory security efforts, showing that the day-to-day activities of FSIRTs have various features and characteristics different from those of CSIRTs. The panel then discussed the four elements, (1) regulations, (2) structure, (3) training, and (4) assessment, as perspectives on responding to incidents at factories, and addressed issues related to incidents and training.
Next, as one of the deliverables of the WG, the draft scenario material for factory security IR training was reviewed and its use was discussed. The created draft scenario material emphasizes the importance of daily incident training, and the scenario is approximately 90 minute long so that it can be easily incorporated into daily activities. In addition, an explanatory chapter was also prepared, providing an overview of the incident and points to consider, which should be utilized for review after the exercise. He also said that the second deliverable of the WG, the proficiency level self-check sheet, will make it easier to set goals and maintain motivation by conducting training on a daily basis and evaluating proficiency, and that he hopes the results will be used as feedback for other activities. In addition, it was also mentioned that ICS security continues to be one of the most important themes and that he would like to see training incorporated as a daily activity. He also said he would like to receive feedback from the participants.
Closing Remarks
Takayoshi Shiigi, Director, JPCERT/CC
Takayoshi Shiigi, Director of JPCERT/CC, made closing remarks.
He noted that the 16th conference was held online so that people from all over Japan could participate more easily, taking advantage of the recent experience of holding the conference under the influence of the COVID-19 pandemic. He thanked the participants, saying that the conference is only possible with the cooperation of the speakers and the audience.
He also mentioned that the situation surrounding ICS is changing drastically, both internationally and domestically, with the amendment of laws and regulations, and that solving problems related to ICS is, in other words, solving social problems. He stated that difficult issues that cannot be solved by a single organization require mutual collaboration and cooperation, and that it is necessary to have an open-minded and bilateral communication. Mentioning that he saw such aspects in sessions by speakers from different organizations, he said he hopes the conference will be useful for the security of the participants’ own organizations in the future. He also expressed his gratitude to all the speakers and participants, saying that he hoped the conference would be useful not only within organizations but also across organizations, and that he would not consider the conference a unilateral event but would like to receive feedback.
In Closing
This year’s ICS Security Conference featured presentations on the situation surrounding ICS security from a variety of perspectives, including international standards, ICS vendors, security vendors, and user companies. We hope that this conference will serve as a reference for future activities for all attendees involved in this field. We will continue to improve the content of the conference and will strive to disseminate information and share knowledge that contributes to the improvement of ICS security in Japan.
Thank you for reading, and I hope to see you at the ICS Security Conference next year!
Takashi Koshiishi
(Translated by Takumi Nakano)

