Activity Targeting Crypto Asset Exchangers for Parallax RAT Infection
Around February 2023, JPCERT/CC identified an attack that attempted to infect a crypto asset exchanger with the Parallax RAT malware. This attack attempted to infect employees of the crypto asset exchanger with malware by sending spam emails. This article presents the details of this attack.
Flow of events leading to Parallax RAT infection
Figure 1 shows the flow of this attack. The identified attack starts with a spam email, which urges the user to download a file from a Google Drive link on it. Once the user accesses Google Drive, a ZIP file containing a OneNote file is downloaded. When it is opened, a document appears prompting the user to click the VBS files embedded inside. If the target runs one of the VBS files, it downloads and runs several files including Parallax RAT.
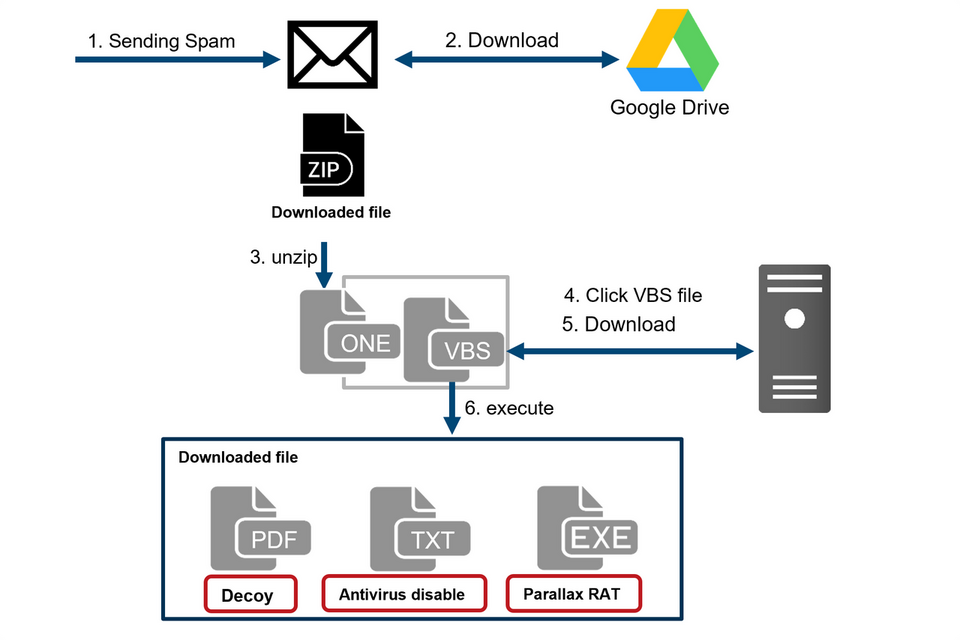
Figure 1: Flow of events leading to Parallax RAT infection
The unique aspects of this attack are described below.- Contents of the OneNote file
- Analysis of Parallax RAT
- Other samples possibly related to this attack
Contents of the OneNote file
The OneNote file identified in this case had VBS files embedded inside, and they were hidden behind an image that prompts the target to click them, as shown in Figure 2.
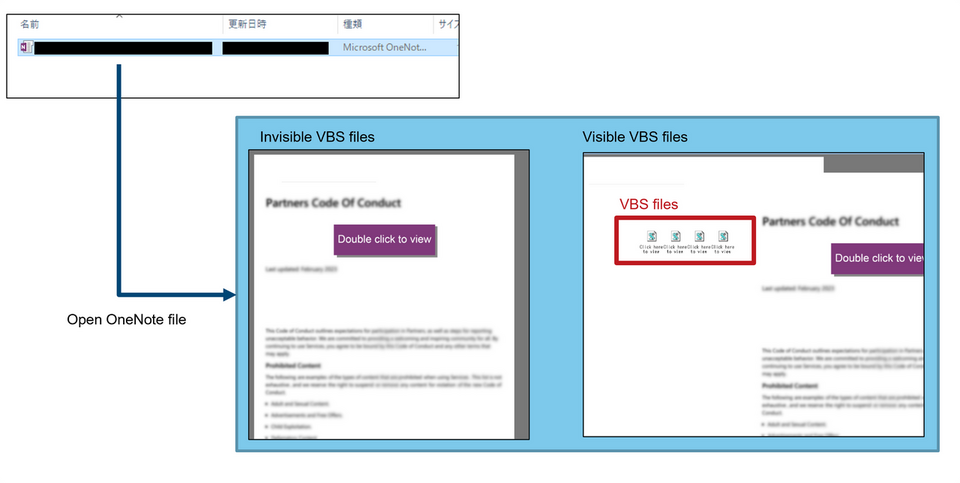
Figure 2: Contents of the OneNote
The embedded VBS files are obfuscated. By decoding one of them multiple times, the PowerShell script in Figure 3, which will eventually be executed in the attack, can be retrieved.
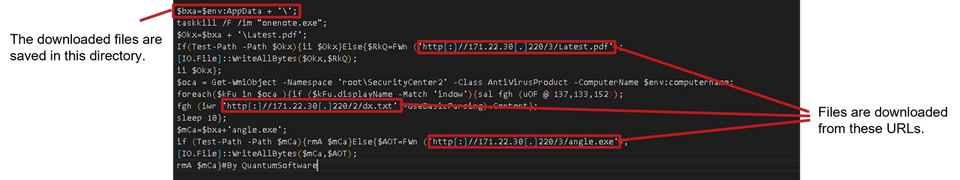
Figure 3: An excerpt from the PowerShell script to be executed eventually
The files that the PowerShell script downloads are as follows.
- Latest.pdf
- Decoy PDF file
- dx.txt
- Configure WindowsDefender exclusions, stop UAC
- angle.exe
- ParallaxRAT
The dx.txt file contains the PowerShell script as shown in Figure 4. It stops UAC and sets the folders where the script is saved to be excluded from inspections by WindowsDefender.
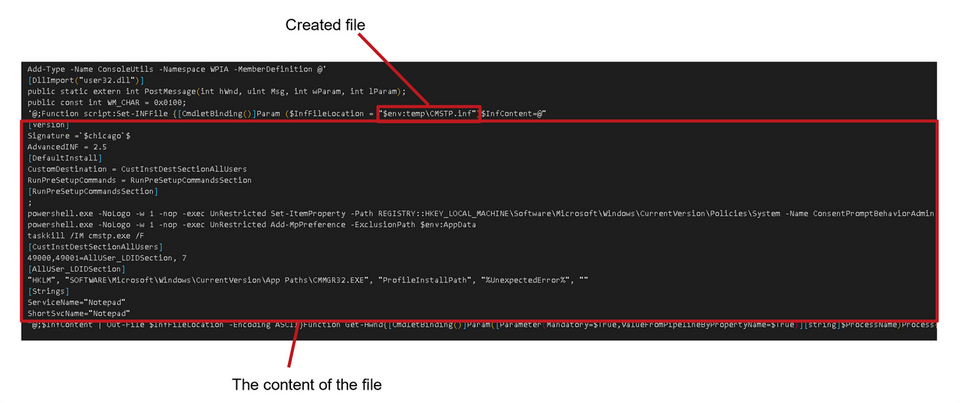
Figure 4: Contents of dx.txt
Analysis of Parallax RAT
Parallax RAT operates in the flow shown in Figure 5.
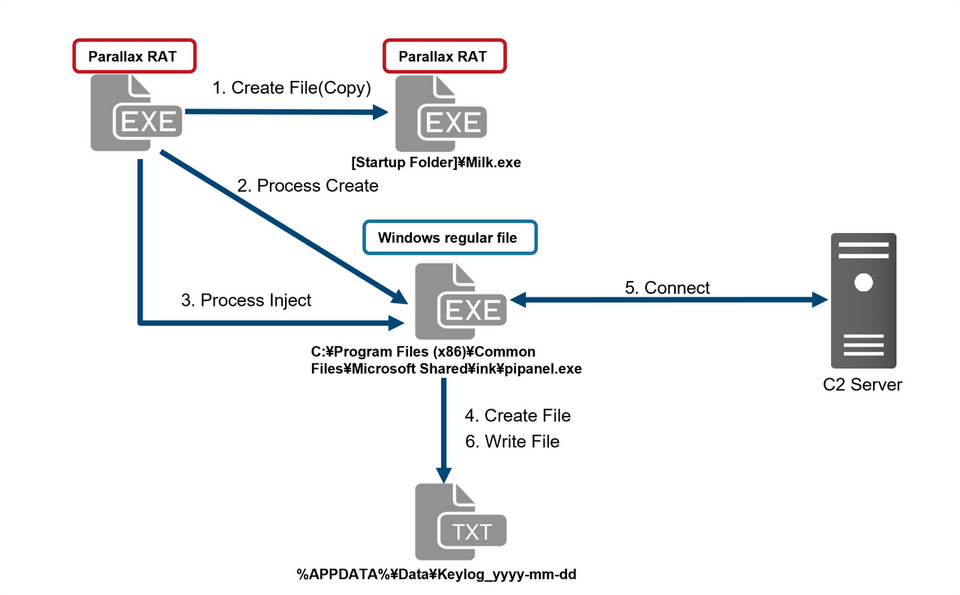
Figure 5: Behavior of ParallaxRAT
1. Create the same file below for automatic execution at device startup
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Milk.exe
2. Execute the below Windows legitimate process
C:\Program Files (x86)\Common Files\Microsoft Shared\ink\pipanel.exe
3. Inject malicious code into the above process
4. Save the key log file in the below file
%APPDATA%\Data\Keylog_yyyy-mm-dd
5. Communicate with the below C2
144.202.9.245:80
Below is a part of the code for the keylogging and stealing clipboard information function
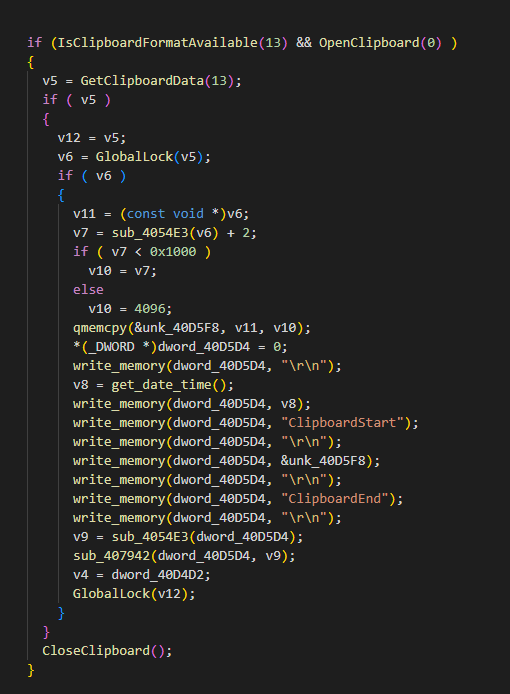
Figure 6: Function to steal clipboard information
Other samples possibly related to this attack
In addition to the Parallax RAT, the following malware and tools were identified on the server used in this attack. These tools and malware may also have been used in the attack. See Appendix B for details.
- NetSupport Manager
- GuLoader
- IRC bot
Not only the OneNote file presented in this article, but also another OneNote file that appears to have been used in other attacks has also been identified. In this file, commands and passwords that the attacker probably used when uploading the file to the server were also found.
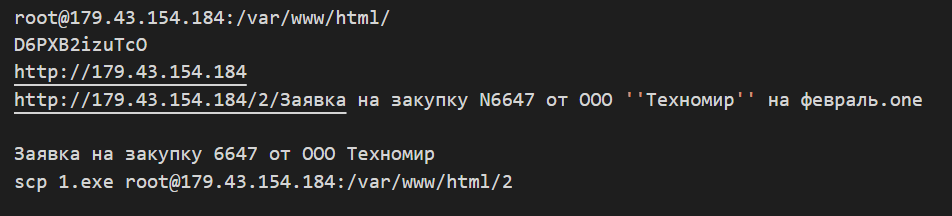
Figure 7: Commands included in the OneNote file
In closing
In recent years, a technique using OneNote files to infect users with malware has been confirmed. The ParallaxRAT identified in this case uses a legitimate Windows file’s process to perform malicious behavior. This is considered a behavior to make detection harder for security products. The malware and C2 servers used in this attack are listed in the Appendix.
Kengo Teramoto
(Translated by Takumi Nakano)
Appendix A: C2 servers
Samples related to Parallax RAT
- http://171.22.30.220/3/Latest.pdf
- http://171.22.30.220/2/dx.txt
- http://171.22.30.220/3/angle.exe
- 144.202.9.245:80
Samples possibly related to this attack
- http://171.22.30.220/1/NtG.hta
- http://171.22.30.220/1/NetGearRuntime.exe
- http://171.22.30.220/7/Com.exe
- http://171.22.30.220/4/irs_notice.vbs
- Dcejartints16.com:4421
- Dcejartints17.com:4421
- https://drive.google.com/uc?export=download&id=1eloFak0vOXvFW9xZ-izVVe8nMc3o2DqI
- https://drive.google.com/uc?export=download&id=1L59KffPvHITYF7rhR_HJapcrL0OYsO98
- http://179.43.154.184/1/report_details.exe
- http://179.43.154.184/1/report_details.jpg
Appendix B: Hash values of the malware
Samples related to Parallax RAT
- c4ab129da3f8d2d101456bdac19d0b9e8a015a87a4117cb88a606b64b36c0e9a
- e5f5c900477a46f5db36ce3bfb67481386fb8576bf9da501a3f380bb6bda5f8f
- 09d04064dc3f4e816ac8004a95c617b9ab481bf4118a6a6e7de177565ffbd843
- c3a3c6015ffc1bc98b5a21f89e78049900e5796e67e098bead011a20a99e7b0d
Samples possibly related to this attack
- ddf17d2e001e4c3d3a80fbf7791ad5d2059b31405658c6fb2121f758e5764a1d
- d1e6ad52f08bb9ecefea9c6d13af964d3fba9130d3b70efa3f236d64c2c25ed3
- dc450bf333dd5533e9f3a919a5412529ba0477e6eee69caf23c9c881814a5bb6
- 2ac200765014f0d994a988d830c6732c9dec5f8546e6f3abb981c38e6a9aa1be
- 08a0519dcc85dd524279c7faab604130e6fd508f504719bb1a29f3f0e4d8b34b
- 5afd6903da4938ea58384e01e7ad4d13b64a6c546712dfd159837b9295465283
- f92f57d8574d1ba2e5b8d8380d7d57aa1035d3adbdb318deec15223c335019b1
- 795d1fba51a3f57c0fb1b3fb72e5507b149a9ab98f6a66f6e94c44a1c74b7f69
- 036022c9229ad7514f473332b8df6e1f538b7d670b5da29fd6401a0f7b8df1b7
- c7dfd72455daffe73a0fa03fd2fa486f4632c1fb8e1cde0c6614efe098409964
- 0b28b325b14dd5b34ce6d232e1b1c210e98fb65725f103df2d9796be24a2a125
- 81b85d5cd1ec4a116e04ff56d509f9bbd3cac0dd9fb695346340a6ccd3dde43d

