Attack Activities by Quasar Family
Quasar [1] is an open source RAT (Remote Administration Tool) with a variety of functions. This is easy to use and therefore exploited by several APT actors. JPCERT/CC has confirmed that a group called APT10 used this tool in some targeted attacks against Japanese organisations.
As Quasar’s source code is publicly available, there are many variants of this RAT seen in the wild (referred to as “Quasar Family” hereafter). Some of them have been used in attacks against Japanese organisations, and they are seen as a threat as well as Quasar itself.
This article introduces the details of Quasar and Quasar Family.
Quasar overview
Quasar offers many functions which are intended for purposes such as device management, support operation and employee monitoring. Figure 1 describes Quasar’s functions and its supported environment as specified on GitHub.
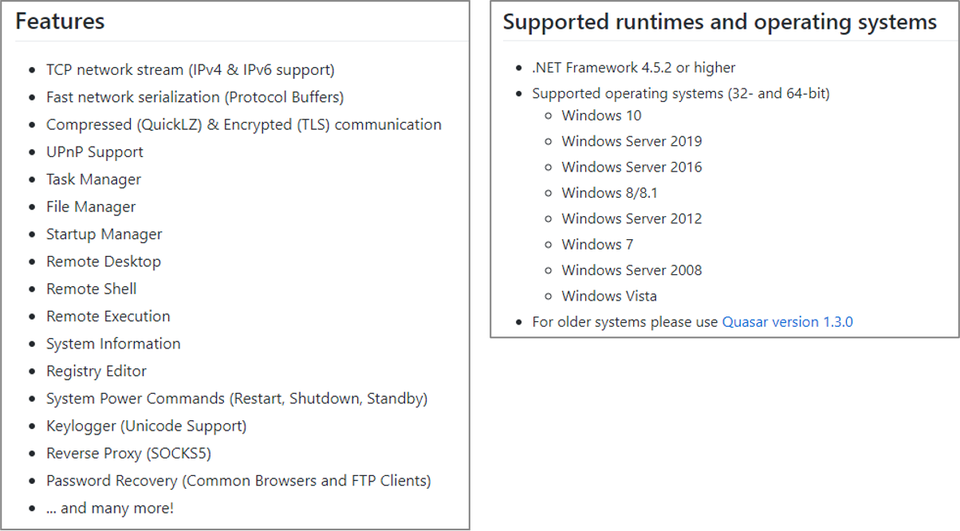
This tool was called “xRAT” at the time of its initial release, however, it was renamed as “Quasar” in August 2015. The latest version is v1.4, released in June 2020.
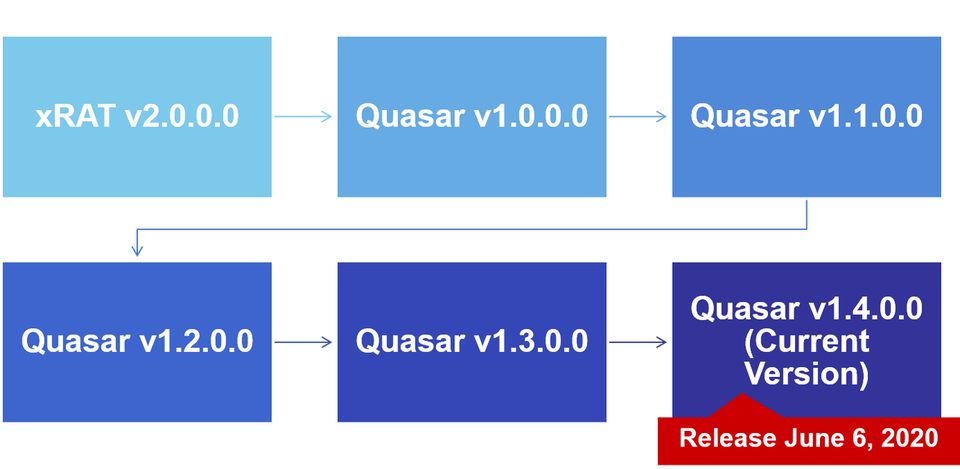
As v1.3 and the earlier are still used in recent attacks, this article explains the functions of both v1.3 and v1.4.
Communication protocol
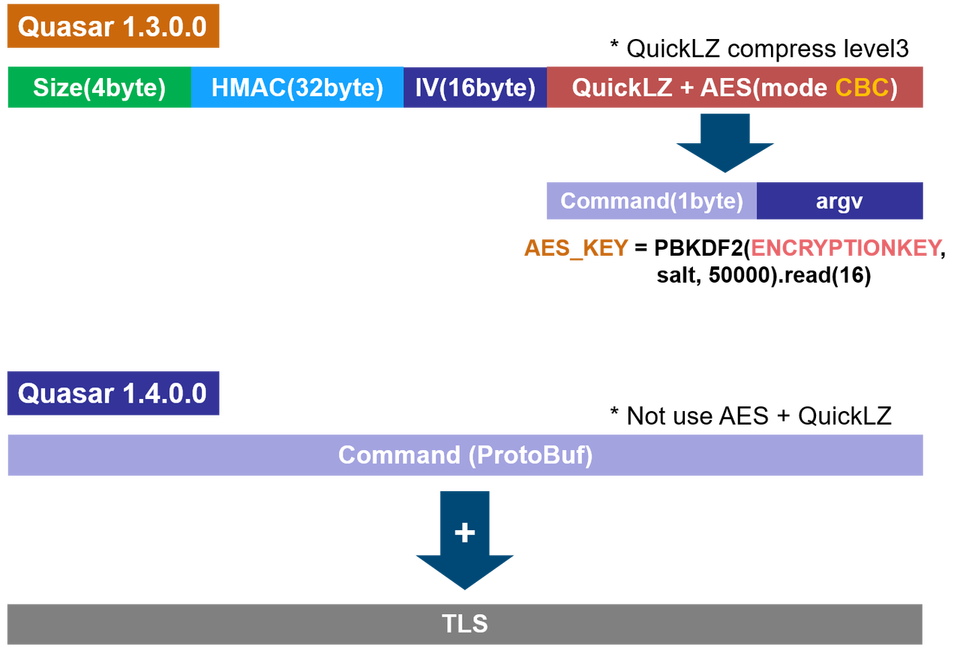
Quasar v1.3 uses its custom protocol which combines AES and QuickLZ. In v1.4, however, Protocol Buffer (developed by Google) is used for data serialisation instead. In addition, the entire communication is encrypted with TLS1.2.
Figure 3 shows the comparison of the communication format in v1.3 and v1.4.
Communication flow
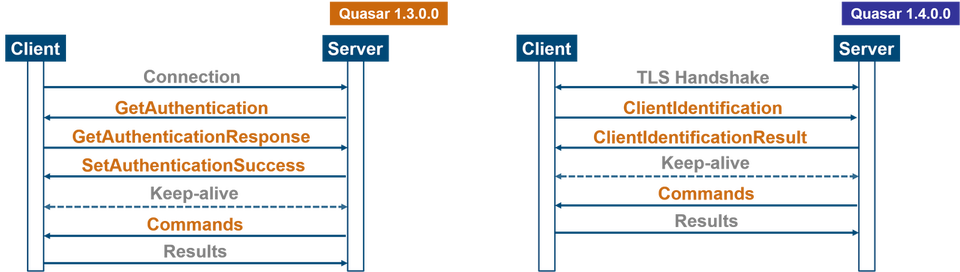
In v1.3, once a client connects to a server, authentication is performed. After that, the main body of data including the commands are exchanged. On the other hand, the authentication is replaced by a TLS handshake in v1.4, and the data exchange begins after that.
Figure 4 illustrates Quasar’s communication flow between a client and a server.
Configuration
Quasar possesses its configuration in itself. It is encrypted by the combination of AES and BASE64 encoding. It is decrypted with the value specified in “ENCRYPTIONKEY” in the configuration when executed.
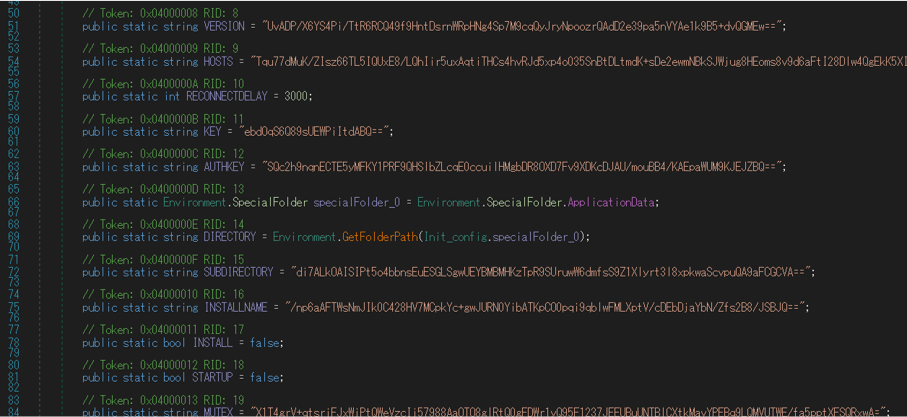
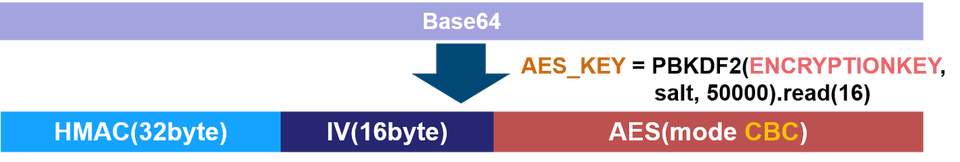
Table 1 details the configuration for Quasar.
| VERSION | INSTALL | LOGDIRECTORY (1.3) |
| HOSTS | STARTUP | SERVERSIGNATURE (1.4) |
| PORT (xRAT only) | MUTEX | SERVERCERTIFICATESTR (1.4) |
| RECONNECTDELY | STARTUPKEY | SERVERCERTIFICATE (1.4) |
| KEY | HIDEFILE | HIDELOGDIRECTORY (1.3) |
| AUTHKEY | ENABLEUACESCALATION (xRAT only) | HIDELOGSUBDIRECTORY (1.3) |
| DIRECTORY | ENABLELOGGER | INSTALLPATH (1.4) |
| SUBDIRECTORY | ENCRYPTIONKEY | LOGSPATH (1.4) |
| INSTALLNAME | TAG (1.3) | UNATTENDEDMODE (1.4) |
Commands
In v1.3, command sets are defined for “typeof” calls. Figure 7 shows some examples of commands defined in Quasar.

Quasar Family
Table 2 is the list of Quasar Family derived from Quasar which JPCERT/CC confirmed.
Name |
Category |
Configuration |
Communication protocol |
Use in attacks in the wild |
|---|---|---|---|---|
| Golden Edition | Clone | Identical | Identical | Confirmed |
| XPCTRA | Clone | Custom | Identical | Confirmed |
| CinaRAT [2] | Clone | Identical | Identical | Confirmed |
| Xtremis 2.0 [3] | Clone | Identical | Identical | Not confirmed |
| QuasarStrike [4] | Clone | Identical | Identical | Not confirmed |
| VenomRAT | Clone | Identical | Identical | Not confirmed |
| RSMaster [5] | Partially copied | Custom | Identical | Not confirmed |
| Void-RAT | Partially copied | Custom | Identical | Confirmed |
| AsyncRAT [6] | Partially copied | Custom | Identical | Confirmed |
* “Clone” in the category refers to variants which uses the entire source code of Quasar with some functions added or modified. “Partially copied” refers to variants created as a new RAT using parts of the original source code.
Figure 8 shows the comparison of commands embedded in XPCTRA and Quasar.
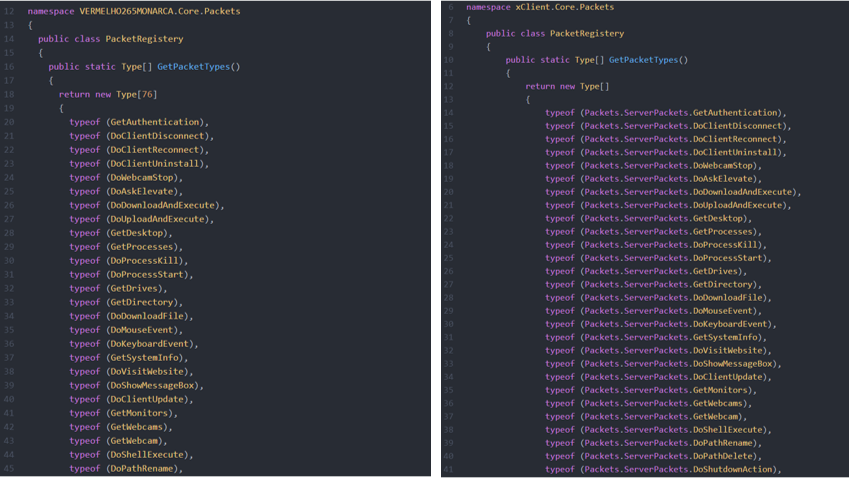
(Left: XPCTRA / Right: Quasar)
In the comparison above, it is clear that commands in XPCTRA are mostly identical to those in Quasar.
Figure 9 shows the comparison of the salt value in AsyncRAT and Quasar.
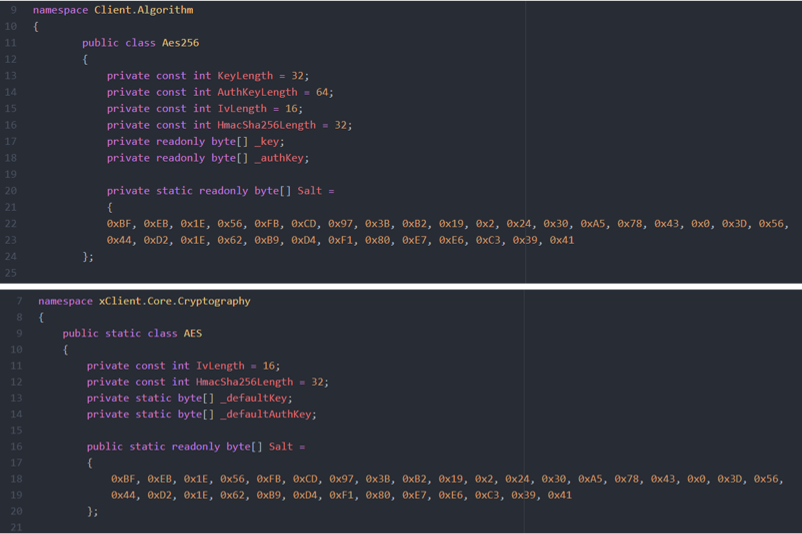
(Above: AsyncRAT / Below: Quasar)
The salt value in AsyncRAT is identical to that in Quasar.
As Quasar Family applies some parts of the source code of Quasar, its configuration and communication protocol are also identical. In some cases, some functions are customised, and as a result, some new configuration and commands are added.
Attack campaigns using Quasar
Quasar has been used in many attack campaigns. Table 3 lists the differences of Quasar used by each attack group.
| Attack group | Quasar version | Customisation | Obfuscation |
|---|---|---|---|
| APT33 | 1.3.0.0 | No | ConfuserEx v1.0.0 |
| Gorgon Group | - | No | |
| APT-C-09 | 2.0.0.0 RELEASE3 | No | |
| DustySky | 1.1.0.0 | No | |
| APT10 | 2.0.0.0(Custom Version) | Yes | ConfuserEx v1.0.0 |
The original Quasar with the default configuration value was used in most cases. Figure 10 shows an example configuration of Quasar used by APT 33.
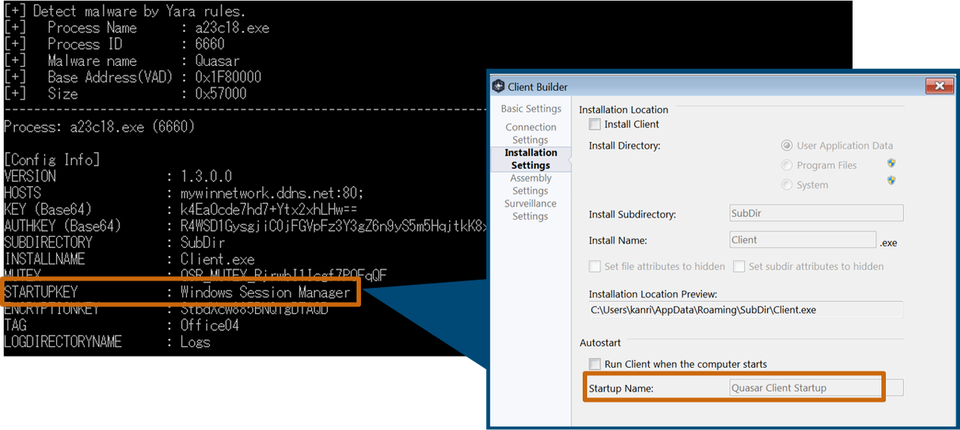
In most parts, the default values of the builder generating Quasar are used as is, except for STARTUPKEY. This way, attacker groups use the default values as per the original to avoid leaving any distinctive evidence.
In some cases, attackers customise Quasar. For example, APT 10 updated some features and used it in some attacks. The following sections will cover the details of this custom Quasar.
Configuration
Quasar used by APT 10 (hereafter “custom Quasar”) has the following additional values in the configuration.
- DOWNLOAD_URL
- PROXY
Figure 11 shows the comparison of configuration in the custom Quasar and the original Quasar.
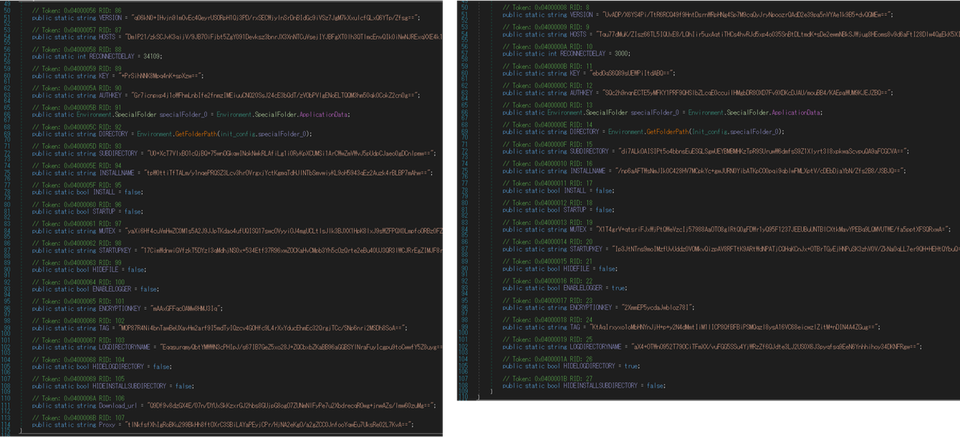
(Left: custom Quasar / Right: original Quasar)
In “PROXY”, a proxy server URL can be configured. This ensures that the custom Quasar is able to communicate with a C2 server even if the target’s environment uses proxy servers.
While the original Quasar uses CBC mode when encrypting configuration with AES, the custom Quasar uses CFB mode.
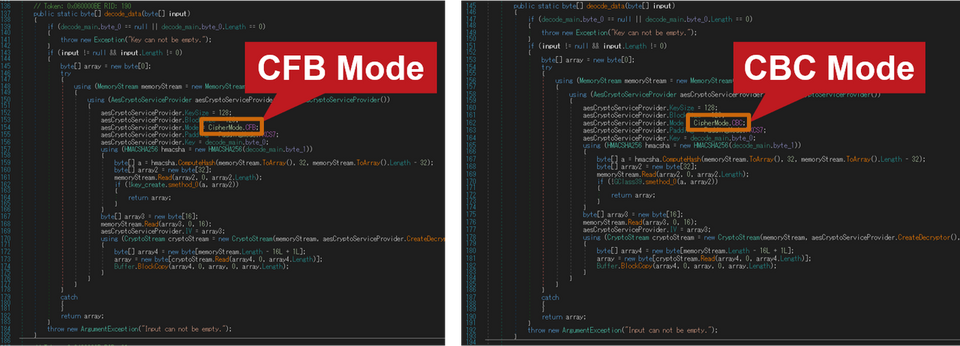
(Left: custom Quasar / Right: original Quasar)
Added/deleted commands
There are some changes to the commands in the custom Quasar. Figure 13 shows the comparison of commands in the custom Quasar and the original Quasar.
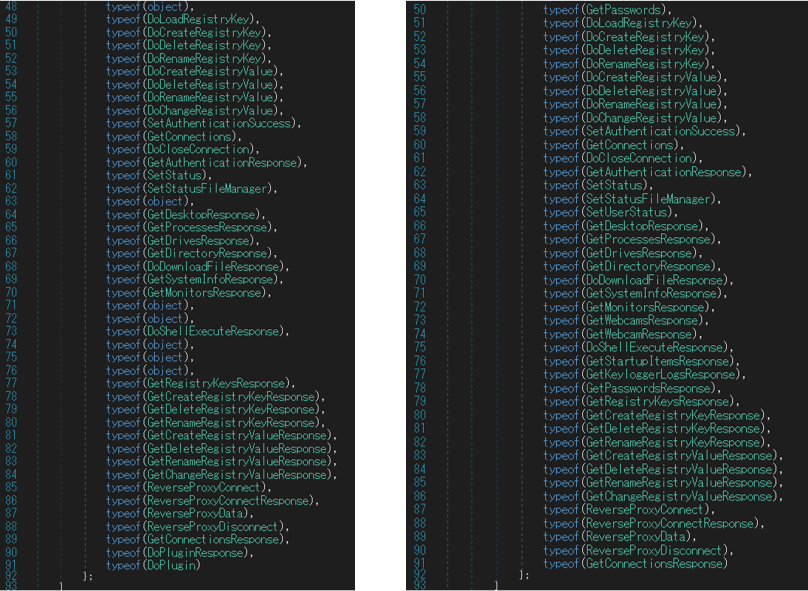
(Left: custom Quasar / Right: original Quasar)
In the custom Quasar, new commands DoPlugin and DoPluginResponse are added while some including keylogger are deleted.
With DoPlugin, new functions can be added by loading additional plugin modules. These new modules can be deleted with DoPluginResponse.
This change enables Quasar to dynamically extend its functions with commands while maintaining Quasar itself as simple as it can be. This suggests the attacker’s intention to avoid detection by anti-virus software.
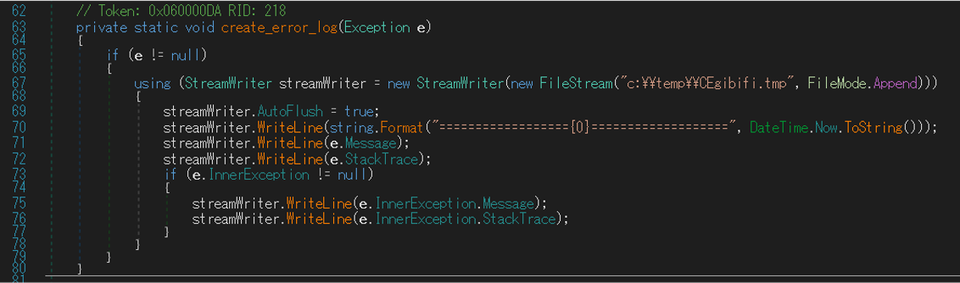
Error log creation
The custom Quasar has a function to create error logs. The file path of the error logs is hardcoded in itself.
Communication protocol
The encryption algorithms for communication with a C2 server also differs in the custom Quasar. While the original Quasar uses AES and QuickLZ, the custom Quasar also uses XOR encoding. Figure 15 shows the XOR encoding process added to the custom Quasar.
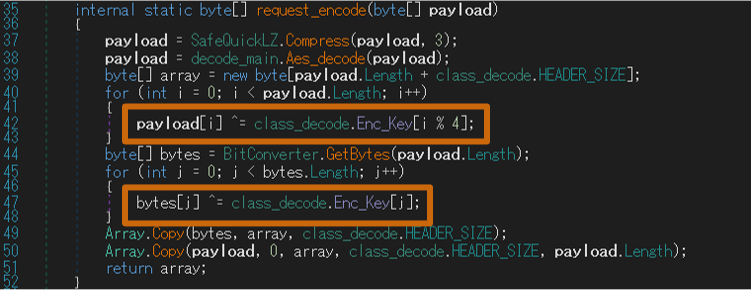
For AES encryption, the custom Quasar uses CFB mode instead of CBC mode, as seen in the configuration. The encryption methods are as follows:
- Original Quasar: QuickLZ + AES (mode CBC)
- Custom Quasar: QuickLZ + AES (mode CFB) + XOR
C2 server activities
JPCERT/CC investigated the activities of Quasar Family C2 servers based on the characteristics discussed above. As of November 2020, 76 IP addresses running as C2 servers have been identified. Figure 16 shows the distribution of Quasar Family C2 servers which were revealed in this investigation.
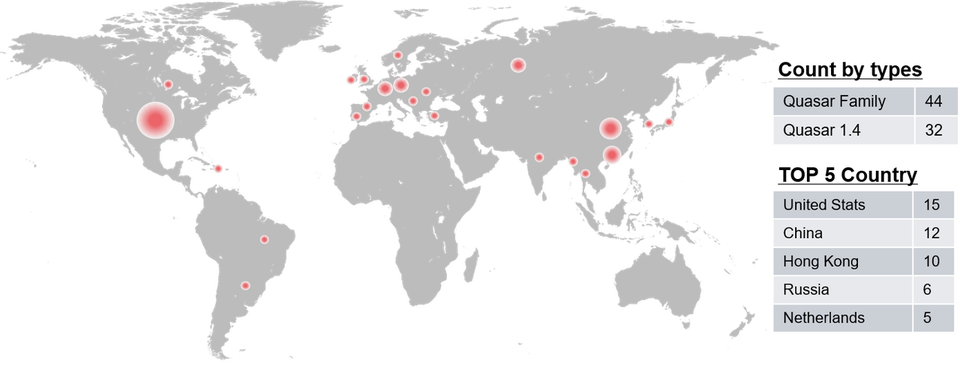
Multiple C2 servers are still running in different countries, which indicates its activeness.
In closing
Besides Quasar, other open source RATs are being used in ongoing attack cases [7]. Attackers are taking advantage of these tools to make attribution difficult and reduce the cost for developing attack infrastructure. It is estimated that this attack trends may continue.
A tool to support Quasar analysis (compatible with Quasar v1.3 only) is available on GitHub. We hope you find it useful.
- Kota Kino, Shusei Tomonaga
- In cooperation with Tomoaki Tani
(Translated by Yukako Uchida)
Reference
[1] GitHub: Quasar
https://github.com/quasar/Quasar
[2] GitHub: CinaRAT
https://github.com/wearelegal/CinaRAT
[3] GitHub: Xtremis 2.0
https://github.com/pavitra14/Xtremis-V2.0
[4] GitHub: QuasarStrike
https://github.com/Q-Strike/QuasarStrike
[5] GitHub: RSMaster
https://github.com/Netskyes/rsmaster
[6] GitHub: AsyncRAT
https://github.com/NYAN-x-CAT/AsyncRAT-C-Sharp
[7] Japan Security Analyst Conference 2020 (Opening Talk): Looking back on the incidents in 2019
https://jsac.jpcert.or.jp/archive/2020/pdf/JSAC2020_0_JPCERT_en.pdf

