TSUBAME Report Overflow (Jul-Sep 2022)
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of April to June 2022. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here.
Observation trends of packets from scanners in Japan
TSUBAME observes packets from a variety of sources. It observes not only scans related to cyber attacks, but also those for security research and investigation purposes, as well as scan traces by network administrators to check firewalls and server logs. TSUBAME observed about 30 IP addresses that sent packets to more than 10 ports from a source in Japan on a single day (from 0:00 to 23:59). This article discusses the characteristics of such domestic scans for research and investigation purposes. Among such scans observed by TSUBAME, Table 1 lists the observation dates and source IP addresses of three major organizations ([1][2][3][4]), which mention their scan activities on their websites or other sources.
Table 1: Changes in the number of IP addresses in Japan used for scan activities
| Domestinc Organization A | Domestinc Organization B | Domestinc Organization C | Other | |
| 2022-07-01 | 1 | |||
| 2022-07-02 | ||||
| 2022-07-03 | ||||
| 2022-07-04 | 4 | 9 | 1 | |
| 2022-07-05 | 9 | |||
| 2022-07-06 | 8 | |||
| 2022-07-07 | ||||
| 2022-07-08 | ||||
| 2022-07-09 | ||||
| 2022-07-10 | 1 | |||
| 2022-07-11 | ||||
| 2022-07-12 | ||||
| 2022-07-13 | 9 | |||
| 2022-07-14 | 9 | |||
| 2022-07-15 | 9 | |||
| 2022-07-16 | 1 | |||
| 2022-07-17 | ||||
| 2022-07-18 | 1 | |||
| 2022-07-19 | 1 | |||
| 2022-07-20 | 1 | |||
| 2022-07-21 | 2 | |||
| 2022-07-22 | ||||
| 2022-07-23 | 10 | |||
| 2022-07-24 | 10 | 1 | ||
| 2022-07-25 | 9 | 1 | ||
| 2022-07-26 | 1 | |||
| 2022-07-27 | ||||
| 2022-07-28 | 1 | |||
| 2022-07-29 | 2 | |||
| 2022-07-30 | 1 | |||
| 2022-07-31 | 1 | |||
| 2022-08-01 | 1 | |||
| 2022-08-02 | ||||
| 2022-08-02 | ||||
| 2022-08-03 | 1 | |||
| 2022-08-04 | 1 | |||
| 2022-08-05 | ||||
| 2022-08-06 | 10 | |||
| 2022-08-07 | 10 | |||
| 2022-08-08 | 4 | 9 | ||
| 2022-08-09 | 1 | |||
| 2022-08-10 | ||||
| 2022-08-11 | ||||
| 2022-08-12 | 1 | |||
| 2022-08-13 | 2 | |||
| 2022-08-14 | 1 | |||
| 2022-08-15 | 1 | |||
| 2022-08-16 | 2 | |||
| 2022-08-17 | 2 | |||
| 2022-08-18 | 1 | |||
| 2022-08-19 | 2 | |||
| 2022-08-20 | ||||
| 2022-08-21 | 10 | |||
| 2022-08-22 | 10 | 1 | 1 | |
| 2022-08-23 | 9 | 1 | ||
| 2022-08-24 | 1 | 2 | ||
| 2022-08-25 | 1 | 2 | ||
| 2022-08-26 | 2 | |||
| 2022-08-27 | 1 | |||
| 2022-08-28 | 7 | |||
| 2022-08-29 | 10 | 1 | ||
| 2022-08-30 | 1 | 1 | ||
| 2022-08-31 | 1 | 1 | ||
| 2022-09-01 | 1 | 3 | ||
| 2022-09-02 | 1 | 2 | ||
| 2022-09-03 | 1 | 1 | ||
| 2022-09-04 | 1 | |||
| 2022-09-05 | 4 | 1 | 1 | |
| 2022-09-06 | 1 | |||
| 2022-09-07 | 1 | 2 | ||
| 2022-09-08 | 1 | |||
| 2022-09-09 | 1 | |||
| 2022-09-10 | 10 | 1 | ||
| 2022-09-11 | 10 | 1 | ||
| 2022-09-12 | 2 | 1 | ||
| 2022-09-13 | 1 | 1 | ||
| 2022-09-14 | 1 | 1 | ||
| 2022-09-15 | 1 | 1 | ||
| 2022-09-16 | 1 | |||
| 2022-09-17 | 1 | |||
| 2022-09-18 | 9 | 1 | ||
| 2022-09-19 | 9 | 1 | 1 | |
| 2022-09-20 | 1 | 1 | ||
| 2022-09-21 | 1 | |||
| 2022-09-22 | 1 | 1 | ||
| 2022-09-23 | 1 | 1 | ||
| 2022-09-24 | 1 | 1 | ||
| 2022-09-25 | ||||
| 2022-09-26 | 4 | 1 | ||
| 2022-09-27 | 8 | 1 | ||
| 2022-09-28 | 8 | 1 | 1 | |
| 2022-09-29 | 8 | 1 | 1 | |
| 2022-09-30 | 1 |
Packets that can be identified from these IP addresses account for about 30% of the packets sent from Japan. Therefore, network administrators need to take this into account when analyzing logs. Similarly, scanning for research and investigation purposes is also conducted overseas. If you do not wish to have your information obtained unnecessarily, you are recommended to have appropriate settings or access restrictions to avoid responding on unnecessary ports when installing network equipment or constructing a system.
Comparison of the observation trends in Japan and overseas
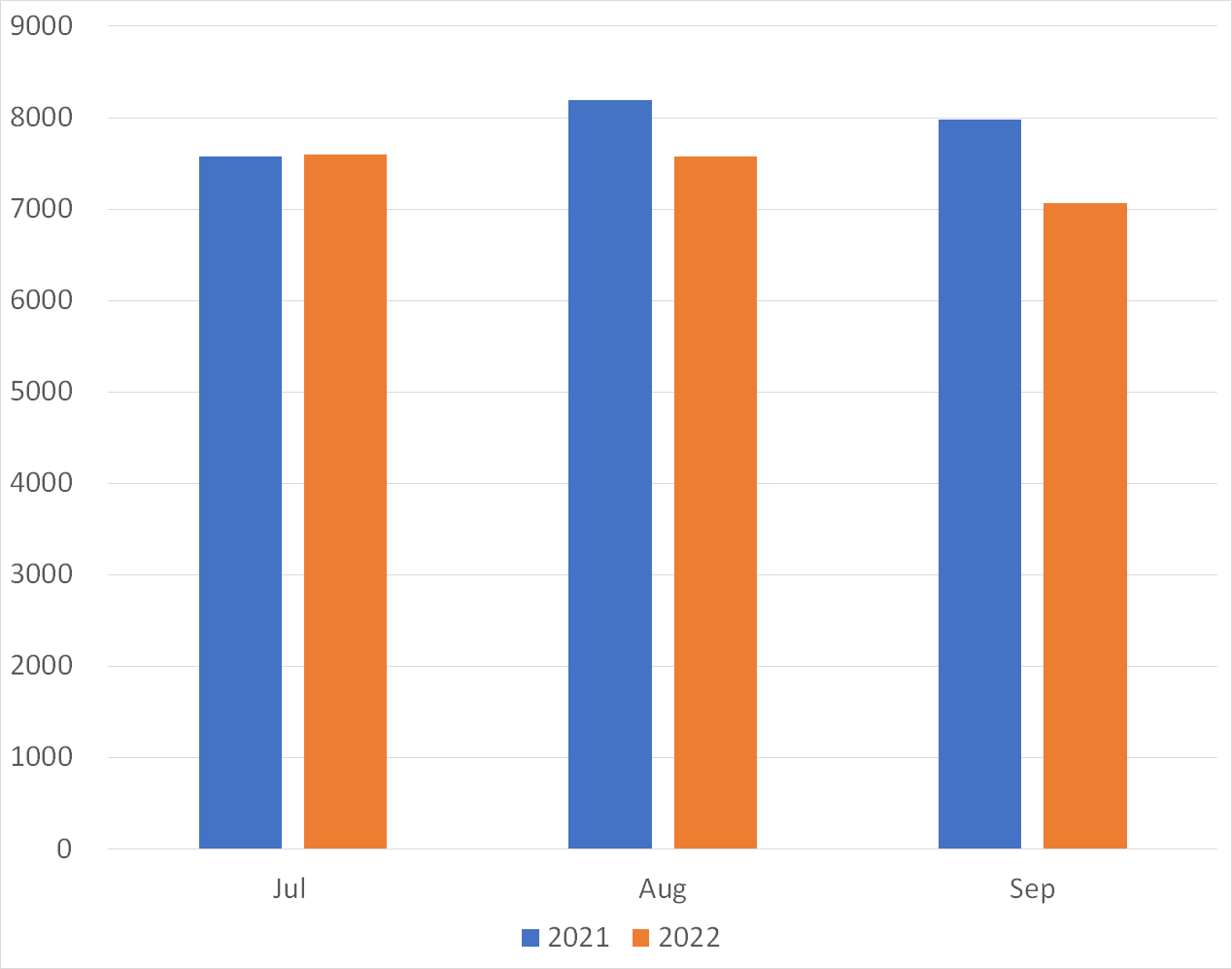
Figures 1 and 2 show a monthly comparison of the average number of packets received per day by each sensor in Japan and overseas. More packets were observed by overseas sensors than those in Japan.
 |
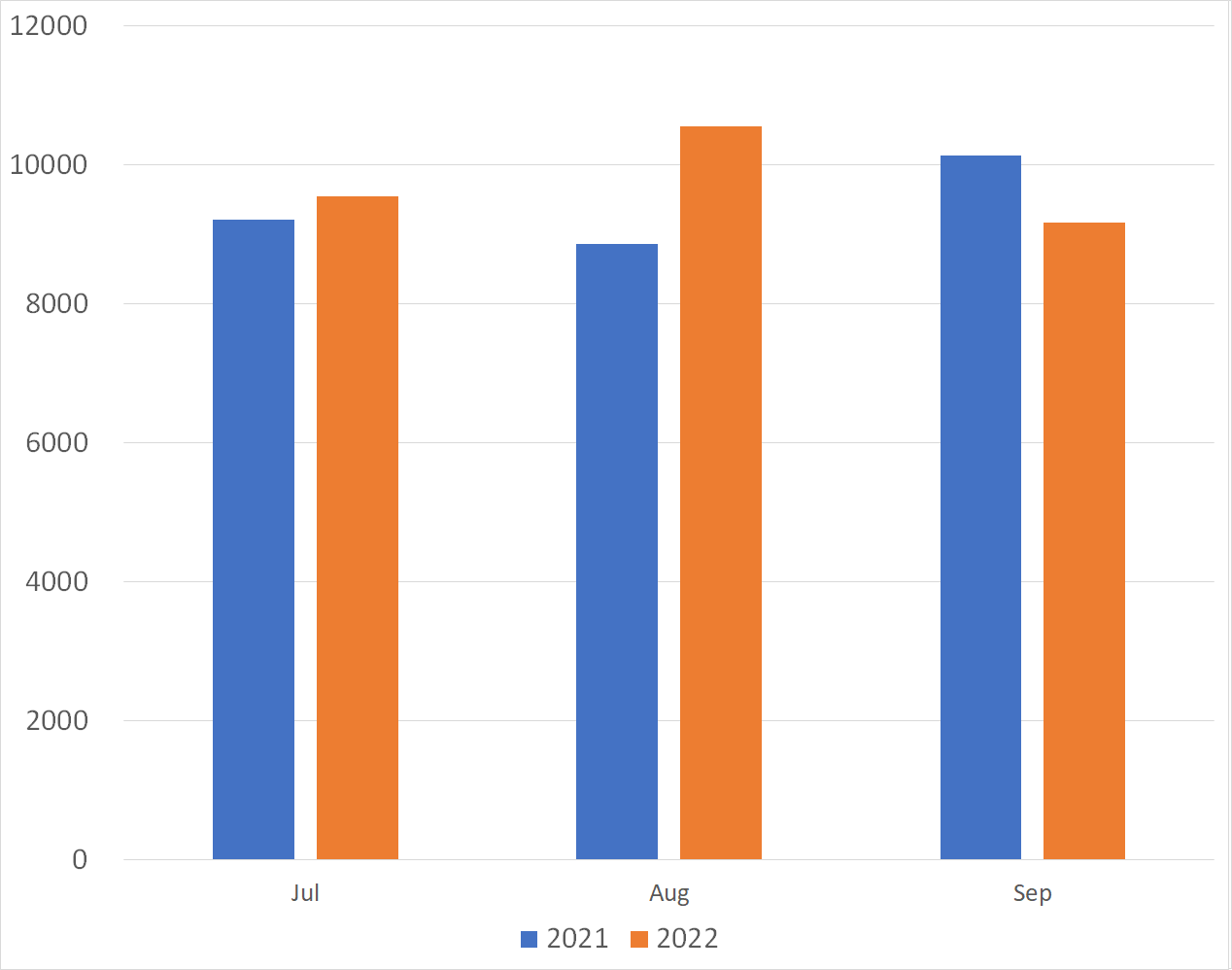 |
| Figure 1: Average number of packets to domestic sensors | Figure 2: Average number of packets to overseas sensors |
Comparison of monitoring trends by sensor
A global IP address is assigned to each TSUBAME sensor. Table 2 shows the top 10 ports of each sensor which received packets the most. In Japan, unlike the sensors overseas, the top 6 ports are almost same on all sensors. 23/TCP was the top on many sensors, and 6379/TCP was also in the top 10 on many sensors. These protocols suggest scan activities in a wide range of networks.
Table 2: Comparison of top 10 packets by domestic and overseas sensors
| #1 | #2 | #3 | #4 | #5 | #6 | #7 | #8 | #9 | #10 | |
| Domestic sensor1 | 23/TCP | 6379/TCP | 22/TCP | 80/TCP | 445/TCP | 5555/TCP | 443/TCP | 1433/TCP | 81/TCP | 8080/TCP |
| Domestic sensor2 | 23/TCP | 6379/TCP | 22/TCP | 80/TCP | 5555/TCP | 445/TCP | ICMP | 443/TCP | 81/TCP | 3389/TCP |
| Domestic sensor3 | 23/TCP | 6379/TCP | 22/TCP | 80/TCP | 445/TCP | 5555/TCP | 443/TCP | ICMP | 1433/TCP | 19/TCP |
| Overseas sensor1 | 37215/TCP | 23/TCP | 22/TCP | ICMP | 52869/TCP | 5060/UDP | 445/TCP | 5555/TCP | 80/UDP | 443/TCP |
| Overseas sensor2 | 23/TCP | 445/TCP | 6379/TCP | 22/TCP | ICMP | 111/TCP | 21/TCP | 80/TCP | 5555/TCP | 139/TCP |
| Overseas sensor3 | 23/TCP | 445/TCP | 139/TCP | 6379/TCP | 22/TCP | ICMP | 5555/TCP | 80/TCP | 443/TCP | 5060/UDP |
In Closing
Observations at multiple locations enables us to determine if fluctuations occurred only in a particular network. Although there was no special issue of security alerts this quarter, scanners continue to be monitored with caution. We will continue to publish blog articles as the Internet Threat Monitoring Quarterly Report becomes available every quarter. We will also publish an extra issue when we observe any unusual change. Your feedback on this series is much appreciated. Please use the below comment form to let us know which topic you would like us to introduce or discuss further. Thank you for reading.
Keisuke Shikano (Translated by Takumi Nakano)
References
[1] NOTICE
ABOUT NOTICE
https://notice.go.jp/en
[2] NICT
The “NOTICE” Project to Survey IoT Devices and to Alert Users
https://www.nict.go.jp/press/2019/02/01-1.html
[3]ICT-ISAC Japan
Investigation of Vulnerable IoT Devices (Japanese)
https://www.ict-isac.jp/news/news20180927.html
[4]Yokohama National University, Japan
Port scanning related to cyber security research
http://119.243.76.25/
http://133.34.169.31/

