APCERT Annual General Meeting and TSUBAME Workshop by JPCERT/CC
Hello everyone! This is Yuka from the Global Coordination Division and APCERT Secretariat.
Today I would like to tell you about the biggest event of APCERT, the 11th Annual General Meeting (AGM) and Conference - 2014 which was held from 18th to 21st March in Taipei. 21 Operational Member teams participated in this reunion as well as some delegates from invited parties. TWNCERT was a host of this event, and JPCERT/CC assisted them as Chair and Secretariat team.
ABOUT APCERT AGM & CONFERENCE 2014
<Event Schedule>
18 March: Steering Committee Meeting and Working Group Meetings/Workshop
19 March: Closed Conference and Team Building Event
20 March: AGM & Closed Conference
21 March: Public Conference

At the Conference (photo by Yuka)
The event consists of three main different parts: meetings, conference and workshop. In the Steering Committee Meeting and the Annual General Meeting (Members only), APCERT members’ activities (e.g. participation in international conferences) in 2013 were reviewed, and also various topics about APCERT business and policies were presented for discussion. At the AGM, JPCERT/CC was elected as Chair team of APCERT for the 4th consecutive year – we feel honoured to keep our contribution to this community for another term. At the conference, speakers from different expertise areas – not only from CSIRT teams but also security vendors and other organisations - were invited to deliver a presentation.
TSUBAME WORKSHOP HOSTED BY JPCERT/CC
Among all the agenda of the event, I would like to highlight on the TSUBAME workshop on the 2nd day, which was hosted by JPCERT/CC. TSUBAME is a network monitoring system developed by JPCERT/CC. 15 people from TSUBAME member teams and also from potential member teams participated in this workshop. JPCERT/CC have organised TSUBAME Workshop at the APCERT AGM every year since 2010 – so this was the 5th workshop. Kaori from the Global Coordination Division and Shikapon from Watch and Warning Group presented the latest trends observed through the system and gave a hands-on session on the TSUBAME portal site. In addition, 2 participating teams gave a presentation sharing their activities and outcomes gained through TSUBAME project.

At TSUBAME Workshop (photo by Yuka)
SCANNING ACTIVITIES ON NTP, PORT 123/UDP
One of the topics covered in the workshop was DDoS attacks exploiting an NTP (Network Time Protocol) feature. Since the end of 2013, we have been observing lots of probes to Port 123/UDP, which is used for NTP through TSUBAME system.
We confirmed that some of the packets received by TSUBAME actually involved “monlist” command. The NTP service supports a monitoring tool that allows administrators to query the server for traffic counts of connected clients. This information is provided via the “monlist” command.
This feature has a potentiality to be abused in conducting a “Distributed Reflection Denial-of-Service (DRDoS) attack”. The basic attack technique consists of an attacker sending a "monlist" request to a vulnerable NTP server with the source address spoofed to be the victim’s address. By executing this command, a large-sized data including the traffic counts of recently connected clients is sent to the victim, which could delay its response or even suspend its system.
As it has been already announced by CSIRTs (including JPCERT/CC) and various security vendors, servers running the NTP based on implementations of ntpd (prior to version 4.2.7p26) that use the default unrestricted query configuration are vulnerable to this type of attack. Users of these versions are recommended to update it to a greater version to prevent the issue.
JPCERT/CC - Alert regarding DDoS attacks leveraging the monlist function in ntpd
https://www.jpcert.or.jp/english/at/2014/at140001.html
CERT/CC - NTP can be abused to amplify denial-of-service attack traffic http://www.kb.cert.org/vuls/id/348126
We have been constantly seeing the packet flow addressed at Port 123/UDP, and it has been even increasing lately as the graph indicates. It can be interpreted that the recommended measures have not been widely taken yet. (Please note that the trends described in the graph include exploring activities by security organisations. The peaks are not necessarily associated with serious attacks.)
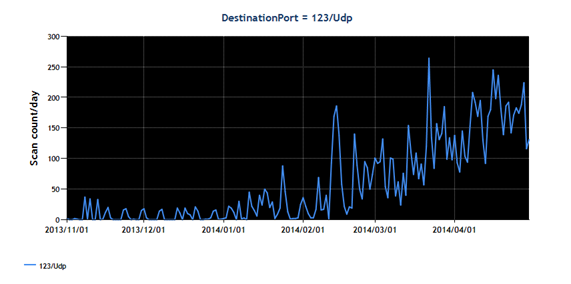
Graph: Scan count per day observed at 123/UDP from November 2013 to April 2014
Source: JPCERT/CC
Through TSUBAME system, JPCERT/CC will keep a very big eye on such suspicious packet traffic and share indications of cyber incidents with relevant parties. We sincerely hope to be of help in early discovery and prevention of potential incidents.
Cheers!
-Yukako Uchida

