Phishing in Japan
For anyone doing incident response in the mid-2000s, you'd no doubt be familiar with the massive upswing in phishing attacks around then. Working in the AusCERT incident response team at the time, we were swamped with scams chiefly targeting Australian banks and financial institutions. Handling a large volume of phishing attacks quickly became a part of our daily routine, and they continue to be part of the landscape.
In early 2007, I moved to Japan to join JPCERT/CC. Much to my surprise, phishing activity was much lower here. Reports of phishing sites hosted in Japan and targeting foreign organisations were a daily event, but attacks against Japanese organisations themselves were rare. It seemed a little optimistic to think that Japan would be spared from such attacks - and naturally, this proved to be correct in time.
In May 2009, the number of attacks targeting Japanese institutions showed a sharp spike. The targets at that stage were chiefly non-bank financial institutions and auction sites, but attacks against banks, online gaming and social networking sites followed.
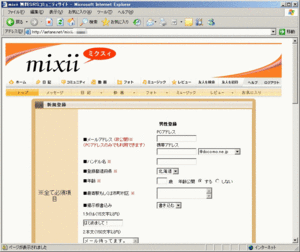
A phishing site for the popular Japanese social networking site mixi.
So, why did Japan enjoy this initial reprieve from phishing attacks compared to Western countries? Why does phishing in Japan not approach the levels seen elsewhere? Likely this will make a good research project one day, but here are some possible factors to think about.
The Japanese language
I can personally attest that Japanese deserves its notorious reputation as a difficult language to learn. The number of Japanese speakers worldwide who can claim some level of fluency is an order of magnitude less than English, and the vast majority of those are native speakers. It's also important to understand that in Japan, communications from a company to its customers are carried out using honorific, formal language, which isn't usually known to novice learners or machine translation programs.
As you might also know, Japanese contains thousands of characters. To make things even more complex, these characters can be encoded using multiple character sets - all of which are widely used in Japan. So, one theory could be that the Japanese language provides a sufficiently high complexity barrier for non-native Japanese attackers to look elsewhere for quick cash.
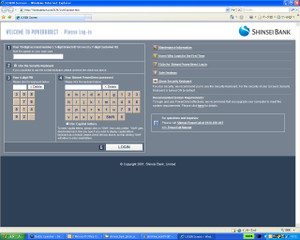
However, that hasn't stopped the odd attacker from spoofing some Japanese banks' English language websites:
Rare English-language phish targeting the Japanese Shinsei Bank.
Of course, that would leave domestic attackers as a possibility. As we'll learn later, domestic groups have already developed their own local scam techniques. Additionally, the perceived lower risk of cross-border phishing attacks is likely one of its attractive elements to many criminals. If the attacker, victim and targeted organisation all reside in the same country, this benefit evaporates and the risk increases.
Japanese e-banking vs ATMs
Japan has a reputation for being a highly technological society, but you might be surprised to know that while electronic banking is mainstream here, it is not as popular as you might expect.
There are possibly a couple of reasons for this. The first reason is that Japan is still largely a cash society. People carry around wads of notes and rarely use credit cards. Many people here have never even seen a cheque. Physical currency is regarded as safe, and so electronic banking takes somewhat of a back seat. It's worth noting, though, that electronic cash in the form of IC cards is making inroads here.
A second theory: widely-available ATMs already do what customers need, 24 hours a day. Touchscreen-equipped ATMs in Japan are far more sophisticated than the standard hole in the wall that just spits out cash. You are able to things like transfer between your accounts, make deposits, and send direct transfers to other accounts: an automated teller which comes very close to replicating its human equivalent.

Japanese ATM machine. Source: Wikipedia.
If I can briefly get on my soapbox, many banks here charge a USD $1 fee for using ATMs outside of business hours. I've always felt that automatic machines of any kind don't need to be paid overtime.
ATMs and bank transfer fraud
Speaking of ATMs: the fact that you can easily transfer money between domestic accounts opens the possibility for other types of fraud. A type that's become somewhat of a local speciality in Japan is known as "furikome sagi" (bank transfer fraud).
The attacker contacts the victim by telephone, and urges them to transfer money to a specified account. The ruse might be a fabricated emergency from a family member, or a demand for penalty fees for an imaginary unpaid bill. Posters warning bank customers of this fraud are a common sight in Japan, more so than awareness campaigns about phishing.
Given that domestic attackers already have a proven technique for extracting funds from their victims, this may also explain the lower uptake of phishing among domestic groups here.
Japanese e-banking two-factor authentication
Upon opening my Japanese bank account over three years ago, I was impressed to receive a simple means of two-factor authentication. Using a 10x10 matrix printed on a PVC card, you read off a four digit response to a transaction-based challenge. It was a very simple, cheap way of providing extra protection to customers at a time when many banks I was familiar with offered little in this way to their retail customers.
Of course, such authentication mechanisms don't offer perfect security. As well as being susceptible to man-in-the-middle attacks and keylogging trojans, a phishing site was once observed by JPCERT/CC that asked the user to enter the entire 10x10 matrix of secret numbers into the site for the attacker's future reference.
At any rate, the wide usage of two-factor authentication in Japan might have added enough cost to attackers to encourage them to find softer targets.
Difficulty getting funds offshore
Often when phishers are looking to move their loot offshore, they'll recruit the services of a "mule". The mule receives the stolen funds from the phisher, then moves the funds overseas using an international money transfer service. Though an apparently easy way to earn money, mules are liable to be prosecuted in many countries.
Some mule recruiters advertising "part-time work in the financial services industry" often request that you live in a particular country, or use a particular bank. This requires understanding of the targeted country's financial system. For example, which are the major banks? How do you transfer money offshore? Is there a tracking system looking for suspicious transactions? What's the maximum amount of money you can move around without it getting flagged for inspection?
I can say that even having lived here for several years, the banking system is still something of a mystery to me, and likely to a foreign attacker too. Additionally, international money transfers here are regulated and monitored.
In summary
I should point out again that these are only theories, and have not been exhaustively researched by any means. However, I know it's been interesting for me to observe the environmental, cultural and organisational differences between countries that may impact online crime.
Chris