Analysis on Compromised Websites in Japan
Hi. This is Misaki Kimura at Watch and Warning Group.
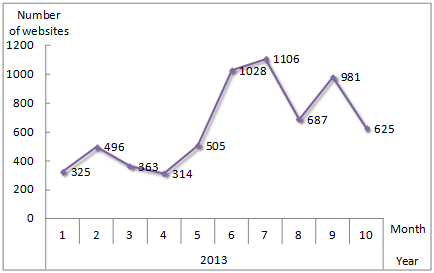
We have been tracking and compiling information on website compromises, impacting thousands of legitimate websites in Japan. The number of compromised websites increased significantly in the first half of JFY 2013: more than 5,200 sites have been compromised from April 1 to October 31, 2013. The following chart illustrates the number of compromised websites detected each month in Japan, counted by IP address.
Figure 1: Number of Compromised Websites Detected Each Month in Japan
Today, I would like to share with you several attack methods with different characteristics which JPCERT/CC observed throughout the year. Since researchers around the globe have spotted and written up on various attacks, some of you may already be acquainted with these methods.
Types of Attacks
1. iframe “counter.php” injection attack
We have been seeing websites containing an appended iframe at the end of the original html code as follows:
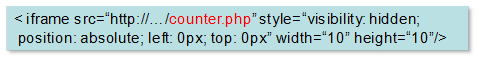
Once inserted, this iframe will be used to download contents from remote malware distributors (the so-called drive-by downloads), and to perform other types of browser-based attacks.
2. Apache module injection attack (aka “Darkleech”)
Known as “Darkleech,” we have also seen a rogue Apache module being installed on compromised servers and turning legitimate websites into attack sites. When visiting such an attack site with Internet Explorer, the following cookie will be set to the visitor’s PC:
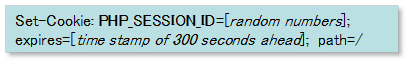
If the browser visits the attack site using the above cookie, a malicious iframe will be dynamically injected only at the point of the visit and redirects users to the infamous Blackhole Exploit Kit landing page. Because of the nature of this compromise – that iframe is not actually a part of their static page – it makes it particularly difficult for website owners/operators to detect or recover from the compromise.
3. Obfuscated JavaScript injection attack
We have been observing malicious iframe containing obfuscated JavaScript codes as below:
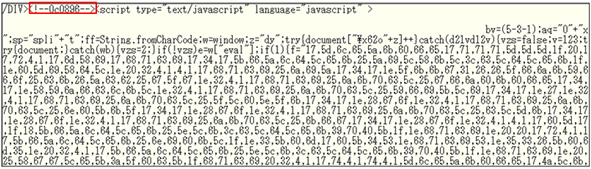
Like the string in the red frame above, we have been observing codes with similar comment tag patterns inserted in front of or after the scripts:
<!—ded509-->
<!—81a338-->
<!—0c0896-->
It remains unclear what these comment tags mean. We suppose it may be the attacker’s signature or calling card to mark its identification. The code in the iframe redirects visitors to the attack sites, which will attempt to install some info-stealing malware such as Kelihos and Pony to visitors’ PCs.
4. iframe “name=Twitter” injection attack
Another pattern we have been seeing is the iframe injection attack as follows:
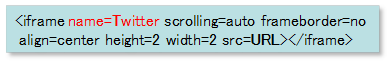
This iframe has nothing to do with Twitter, but visitors’ PCs with this iframe will be redirected to a malicious webpage which resembles the Redkit Exploit Kit.
Summary of Our Findings from these Attacks
We analyzed in our sandbox environment how PCs that visit the attack sites are exploited, and confirmed that similar vulnerabilities are exploited in all of these attacks. It attempts to target known vulnerabilities in software, particularly in third-party application such as Oracle Java, Adobe Acrobat/Reader and Flash Player installed on visitors’ PCs.
Yet, there is no hard evidence of how these attacks make the initial intrusion into the websites they infect, and speculation has surfaced that the web servers are compromised by 3 common methods.
- Attackers gain access to servers by exploiting software vulnerability that is published but not patched. It is said that vulnerabilities frequently remain in Content Management Systems (CMSs). CMS is used to optimize the content management or maintain other functionality of websites. However, websites based on vulnerable CMSs can easily be identified on the Internet. It is also said that vulnerabilities often exist in add-on modules.
Another software vulnerability we have been frequently observing is Parallell’s Plesk Panel, which is not a CMS but a Web Administration Panel. Leaving these software vulnerabilities unpatched, it often becomes a focus point for attackers who attempt to gain access to the web server.
- Even if the website itself is not vulnerable, attackers can gain access to web administrators’ local PCs by exploiting vulnerabilities of OS and other software installed. Attackers intrude into PCs in order to steal web server login credentials such as SSH/FTP accounts saved in local PCs, and attempt to gain access to the web server.
- Another way observed is the so-called “Dictionary Attack.” Attackers target weak, easily-guessable passwords and try to enter usernames and passwords over and over again, until it defeats the authentication of the target.
Efforts to Mitigate the Risk
To mitigate the risk of being hacked, JPCERT/CC is working to raise awareness of the public to its fullest extent. We have issued not only the initial alert in June but also a joint announcement for public awareness raising in September this year, in cooperation with the Information-technology Promotion Agency (IPA) . We have also been delivering presentations on this issue and providing advices directly to ISPs, web hosting companies as well as individual system administrators. Furthermore, in order to expand our outreach to the public, we have utilized the media to draw people’s attention on cyber threats including website hacking. The topic has been covered in some TV news and national newspapers.
Any inquiries on this post are welcome, or if you happen to stumble upon a website with a suspicious look or behavior, most likely to be compromised, please contact us at info(at)jpcert.or.jp or ww-info(at)jpcert.or.jp.
- Misaki Kimura