ICS SECURITY CONFERENCE 2014
Hello, I am Hidekazu Yamada at ICS Response Group of JPCERT/CC.
In this entry today, I would like to look back on “ICS Security Conference 2014” which was held early last month, along with some presentation highlights. My presentation summary on the result of the ICS Asset owners’ survey will also be covered.
Event Overview
The conference took place on Wednesday, 5 February 2014 at Kokuyo Hall in Shinagawa, Tokyo.

This event has been held annually since 2009 to raise awareness towards ICS security, and the specific objective for this year was to encourage each ICS sector to take practical actions to protect themselves against possible incidents caused via corporate network. We had 264 attendees, and most of them were engaged in ICS related field – 20% ICS Asset owners, 55% vendors and 37% researchers (multiple answers allowed).
Here below is the list of speakers and the presentation titles. Some of the conference materials are now available on our website. Feel free to download them by clicking the links.
“Major Topics on ICS Security in 2013 through 2014”
Dr. Toshio Miyachi, Board Member of JPCERT/CC
CSSC’s Test Beds (CSS-based 6) and EDSA Certification
Mr. Hideaki Kobayashi, Vice President of Control System Security Center (CSSC)
(Mostly in Japanese)
CSMS (Cyber Security Management System) Certification
Mr. Toshio Takatori, Vice President of Japan Information Processing Development Corporation (JIPDEC)
“Swelling Cyber Security Threats to Enterprises and Countermeasures against them”
Mr. Takashi Manabe, Director of JPCERT/CC
(Japanese only)
“ICS Security Enhancement in the National Control Centers of Taiwan Power Company”
Mr. Mu-Chun Chang, Deputy Director System Operation Department
Mr. Ralph Langner, The Langner Group Co-Founder and Managing Principal
“Control Systems Security – A CERT Australia Perspective –
Mr. Simeon Simes, CERT Australia Senior Technical Adviser
“Status Updates on Control System Security in Japan and JPCERT/CC’s Activities”
Hidekazu Yamada, JPCERT/CC
All these presentations from the experts were very informative. They showed some actual business cases with asset owners, security actions in relation to ICS system characteristics and activities from CSIRT’s perspectives. Among all the presentations, I would like to pick up and summarize a couple.
Mr. Takashi Manabe shared some actual incident examples to demonstrate how recent “targeted threats” work to damage the control systems. According to him, proactive preparation including the following elements is highly recommended to counteract the cyber threats – to gather/share information with relevant parties, conduct constant trainings and recognize/protect information asset.
Mr. Ralph Langner pointed out the importance of enhancing ICS security management by reducing risks from the 8 Domains (e.g. System inventory, network diagrams, training programs etc). He also suggested constant improvements (Kaizen) on these components to build stronger system against cyber risks.
Malware Infection Rate and Asset Owners’ Risk Perception of Security Incident in ICS Network
I myself talked about JPCERT/CC’s survey conducted in the second half of 2013 among 300 ICS asset owners in Japan. Let me introduce a few observations gained through this survey.
As you well know, many control network of the ICS is now often a protected extension of the corporate networks and potentially reachable from the Internet by malicious adversaries.
It was revealed from the survey that 7% of the respondents’ ICS have experienced malware infection (Figure 1).
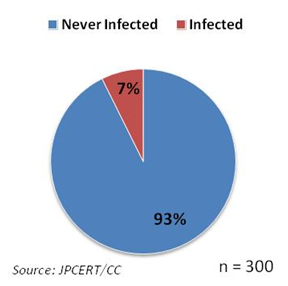
Figure 1 – Percentage of Japanese ICS asset owners who have ever detected malware infection on ICS
I do not know if I should say “only” or “as much as” 7%, but we must focus on the fact that it was not 0%. Wishful thinking says that only limited cases of malware infection have actually been taking place, but at the other extreme, it could also be that any existing infection has not yet been recognized by the asset owners.
Figure 2 below shows the ICS Asset owner’s perception on the possible critical incidents caused via corporate network. About 80% of the respondents (237 asset owners) see low chance of facing such incidents in the future.
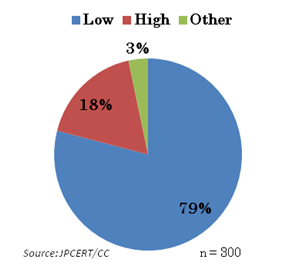
Figure 2 – Risk perception on the possible incident via corporate network
Do you think that they have a good foresight or lacking risk awareness? Anyhow, the important thing is that even just one ICS malfunction case, not limited to those arising from cyber attacks, can largely affect general public. Asset owners cannot be too prepared for this.
Taking Action as ICS Response Group
The survey result has made my group (ICS Response Group of JPCERT/CC) realize the necessity to take further actions for awareness-raising.
Our group was established in July, 2012 to conduct the following activities on ICS security to support our constituents:
• ICS Incident Handling Support
• Coordination of ICS Product Vulnerability
• Awareness Raising for ICS asset owners
We hope to have more constant communication with our constituents, particularly the asset owners, which could lead them to take practical actions and protect themselves against possible incidents.
Thank you!
-Hidekazu Yamada

