Hi all, this is Yuka from Global Coordination Division and also serving as APCERT Secretariat. We are happy to announce that we have just finished one of the big tasks for this year – the host of APCERT Annual General Meeting Conference 2016, which was held on 24-27 October at Royal Park Hotel in Tokyo. After the official establishment of APCERT in 2003, its annual conference had never been held...
-
-
Selamat pagi!! This is Mariko and Wataru from Watch and Warning Group. We were in Indonesia for APT (Advanced Persistent Threat) workshop and log analysis training from October 4th to 6th. This was part of JICA’s (Japan International Cooperation Agency) project on “Capacity building for Information security”, which aims to provide practical trainings for information security staff in the ASEAN region. At first we were a little nervous since we...
-
In most of the targeted attack cases, often multiple computers get infected by malware, rather than just a single computer, and attackers continue compromising other computers across the network, including important servers. For this “lateral movement” purpose, password hash is often targeted. In order to enhance protection against such information theft, LSA Protection Mode for Windows 8.1 etc. and Credential Guard for Windows 10 Enterprise have been introduced. In this...
-
Our previous article “Enhanced Protected Mode in Internet Explorer” (published in August 2015) introduced that running the browser with Enhanced Protected Mode in 64-bit mode is effective in the protection against attacks exploiting vulnerabilities. This entry will verify the effect of “AppContainer” against attacks, which is another function related to Enhanced Protected Mode for Windows 8 and later. AppContainer and Web Browser AppContainer is a sandbox which runs applications in...
-
Dumela! This is hello in Tswana, a widely spoken language in Botswana. I’m Moris, Katsuhiro Mori, working at Global Coordination Division of JPCERT/CC. Recently I visited Gaborone, Botswana with Sparky, my colleague and an expert of cyber security training in Africa, for joining Africa Internet Summit (AIS) 2016 held from May 29 through June 10. AIS is an annual, regional, multi-stakeholder ICT conference since 2013, which aims to bring the...
-
Hello, Taki here. This is more of an update to my previous entry: Some coordinated vulnerability disclosures in April 2016 https://blogs.jpcert.or.jp/en/2016/05/some-coordinated-vulnerability-disclosures-in-april-2016.html Towards the end of the entry, I had mentioned that we were working on upgrading our systems to get more advisories out on our JVN English site. As of May 16th, the JVN site has been updated so that we can release advisories for vulnerability reports that are directly...
-
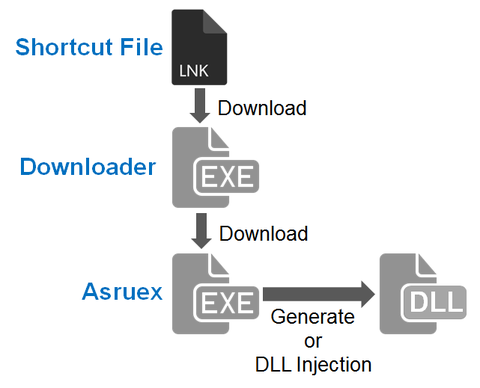
JPCERT/CC has been observing malicious shortcut files that are sent as email attachments to a limited range of organisations since around October 2015. When this shortcut file is opened, the host will be infected with malware called “Asruex”. The malware has a remote controlling function, and attackers sending these emails seem to attempt intruding into the targets’ network using the malware. According to a blog article by Microsoft, the malware...
-
Hello all, this is Shusei Tomonaga again. Generally speaking, malware analysis begins with classifying whether it is known malware or not. In order to make comparison with the enormous number of known malware samples in the database in a speedy manner, hash values are used, derived by performing hash functions to the malware sample. Among the different hash functions, traditional ones such as MD5 and SHA1 derive totally different hash...
-
From the latter half of 2015 to 2016, there have been an increasing number of cyber attacks worldwide using Adwind, a Remote Access Tool [1]. JPCERT/CC also received incident reports about emails with this malware in its attachment. Adwind is malware written in Java language, and it operates in Windows and other OS as well. It has a variety of functions: to download and execute arbitrary files, send infected machine...
-
Nice to see you! My name is Jimmy, Hajime Komaba, working at Enterprise Support Group of JPCERT/CC, a department which takes care of Nippon CSIRT Association (NCA), a community of various enterprise and organizational CSIRTs in Japan) and Council of Anti-Phishing Japan (APC). It’s been quite a while ago, but last November, I was given an opportunity to travel to the Republic of Congo with my colleague, Koichiro (Sparky) Komiyama....