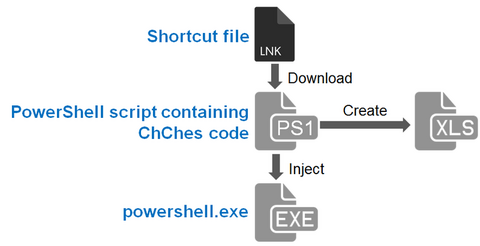
Hi again, this is Shusei Tomonaga from the Analysis Center. In this article, I’d like to share some of our findings about ChChes (which we introduced in a previous article) that it leverages PowerSploit [1] – an open source tool – for infection. Flow of ChChes Infection The samples that JPCERT/CC confirmed this time infect machines by leveraging shortcut files. The flow of events from a victim opening the shortcut...
List of “ChChes”
-
-
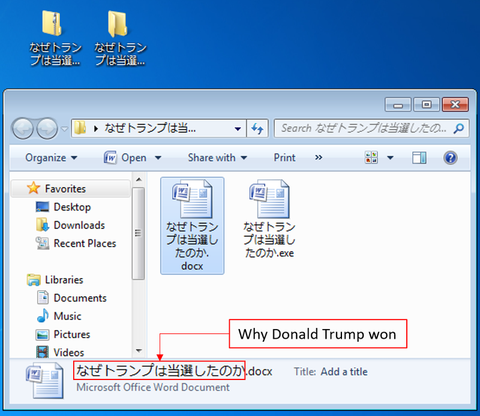
Since around October 2016, JPCERT/CC has been confirming emails that are sent to Japanese organisations with a ZIP file attachment containing executable files. The targeted emails, which impersonate existing persons, are sent from free email address services available in Japan. Also, the executable files’ icons are disguised as Word documents. When the recipient executes the file, the machine is infected with malware called ChChes. This blog article will introduce characteristics...