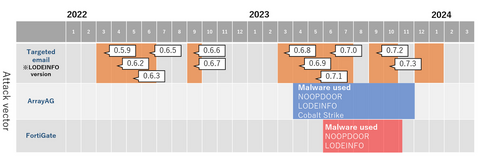
JPCERT/CC has been observing attack activities by MirrorFace LODEINFO ...
List of “Python”
-
-
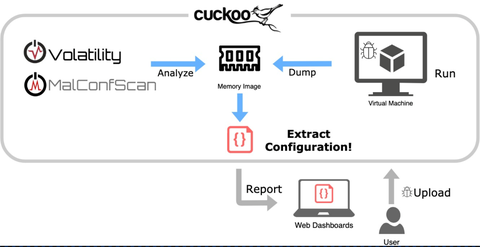
In malware analysis, extracting the configuration is an important step. Malware configuration contains various types of information which provides a lot of clues in incident handling, for example communication details with other hosts and techniques to perpetuates itself. This time, we will introduce a plugin “MalConfScan with Cuckoo” that automatically extracts malware configuration using MalConfScan (See the previous article) and Cuckoo Sandbox (hereafter “Cuckoo”). This plugin is available on GitHub....
-
JPCERT/CC has observed some Japanese organisations being affected by cyber attacks leveraging “Cobalt Strike” since around July 2017. It is a commercial product that simulates targeted attacks [1], often used for incident handling exercises, and likewise it is an easy-to-use tool for attackers. Reports from LAC [2] and FireEye [3] describe details on Cobalt Strike and actors who conduct attacks using this tool. Cobalt Strike is delivered via a decoy...
-
The last article introduced some features of Datper malware and a Python script for detecting its distinctive communication. Based on that, we are presenting how to search proxy logs for Datper’s communication using log management tools – Splunk and Elastic Stack (Elasticsearch, Logstash and Kibana). For Splunk To extract Datper’s communication log using Splunk, the first thing you need to do is to create a custom search command as follows....