APCERT DAY at APRICOT and Open Resolver Check Site Launched by JPCERT/CC
Hello, I am Yukako (Yuka) Uchida from APCERT Secretariat. I am a new Liaison Officer of the Global Coordination Division since last December.
From 18th to 28th February, APRICOT 2014 (https://2014.apricot.net/) had been held in Petaling Jaya, Malaysia. APRICOT, which stands for Asia Pacific Regional Internet Conference on Operational Technologies, is an annual meeting for internet engineers in the region. They have kindly offered APCERT a one-day slot on 26 February to hold the “APCERT DAY”, where speakers from some APCERT Teams (CERT Australia, ID-SIRTII/CC, JPCERT/CC, KrCERT/CC and MyCERT) delivered presentations on their efforts to help create a safe, clean and reliable cyber space in the Asia Pacific region.
The following presentations were given at the workshop. All the filmed contents are currently available on APRICOT program page. (https://2014.apricot.net/program)
Keynote Presentation: “Regional Cyber Security Risk Reduction Approach and Network Operators Network Clean-up Collaboration”
– Yurie Ito (APCERT Chair, JPCERT)
“SCADA Security Assessment: The Malaysian Experience”
– Ruhama Mohammed Zain (CyberSecurity Malaysia)
“Open DNS Resolver Check Site – Towards a Robust Cyber Space”
– Takahiro Ishikawa (JPCERT/CC)
“Cleaning up the Internet – Case Study from Australia”
– Scott Brown (CERT Australia)
“Major Internet Incidents and Response – Example from Korea”
– Hongsoon Jung (KrCERT/CC)
“Network Metrics – Measuring Network Health”
– Yurie Ito (JPCERT/CC)
Plenary Session and Closing: “Collaboration between Network Operators, Registry Services and CERTs on Cyber Risk Reduction and Measurement.”
- Moderator: Yurie Ito (APCERT Chair)
- Panellist: David Conrad (Virtualized), John Crain (ICANN), Yoshinobu Matsuzaki (IIJ)
Facing Open DNS Resolver – JPCERT/CC’s Project
My colleague, Takahiro Ishikawa from Incident Response Team, delivered a presentation about the “Open DNS Resolver Check Site”. It is an online tool released by JPCERT/CC last year, which allows the visitors to check if a DNS server configured on their PC/network device connecting to the site is running as an open DNS resolver or not.
An open DNS resolver, as many of the readers may well know, is a publicly accessible name server that provides a recursive name resolution for unspecified IP addresses. It has been reported that a number of open DNS resolvers are being exploited to participate in massive distributed denial of service (DDoS) attacks – the so called “DNS amplification attack”.
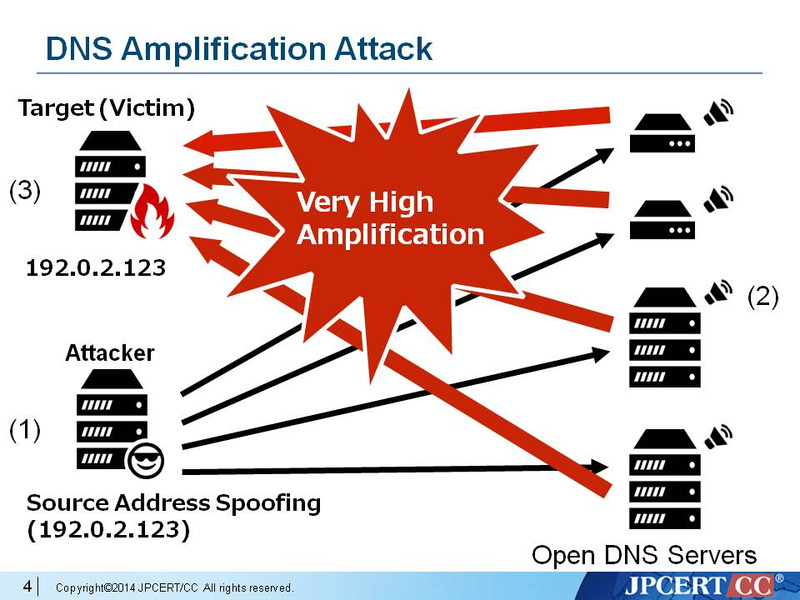
Diagram 1: DNS Amplification Attack Method
(Source: JPCERT/CC)
Here is the attack method. The attacker sends a DNS query - usually requests for as much zone information as possible to maximize the amplification effect - to DNS servers with open resolvers. The source address is spoofed to be the target’s (victim's) address - as in (1) in the diagram. When the DNS servers send the DNS responses (2), they are sent to the target (victim) system and make the victim overwhelmed by excessively large-sized packets in response to the small queries (3).
JPCERT/CC’s Motivation for the Check Site
Takahiro explains that the motivation for launching this tool was actually driven from the statistics published by a private company in early 2013 – that Japan had the largest number of open DNS resolver hosts in the Asia Pacific region at that time. His team was concerned that the open resolver issue is not widely recognised by many internet users and system administrators, and in many cases they are not even aware of running open DNS resolvers on their own. Sometimes it was difficult for the team to reach a contact person that can properly address the issue. They wish that this tool would be helpful in raising awareness towards the problem and in reducing the number of open DNS resolvers.
The Open DNS Resolver Check Site developed by JPCERT/CC offers an easy and simple method to check open DNS resolvers just by accessing the site and giving a few clicks. Please visit the following URL to give it a try:
http://www.openresolver.jp/en/
In addition, his team has also provided a command line tool for those who cannot check using a web browser (e.g. “wget” command). Try using command lines at the following URL:
http://www.openresolver.jp/cli/check.html
In case it turns out that you are running an open DNS resolver, you will be provided with some suggested solutions.
JPCERT/CC is willing to keep collaborating with any global partners to address this problem and make the cyber space cleaner and more secure.
Thank you!
-Yukako Uchida