Source Port Randomization for Caching DNS Servers Requested, yet again.
Hello, this is Moto Kawasaki, a new member of Global Coordination Division.
Alerts from JPRS and JPCERT/CC
On April 14th 2014, JPRS (Japan Registry Services Co., Ltd.) and JPCERT/CC concurrently published the alerts on DNS cache poisoning attack.
Alert from JPRS
http://jprs.jp/tech/security/2014-04-15-portrandomization.html (Japanese version)
Alert from JPCERT/CC
https://www.jpcert.or.jp/english/at/2014/at140016.html (English version)
https://www.jpcert.or.jp/at/2014/at140016.html (Japanese version)
Now I'd like to elaborate on the key points and share my views on the case by reading between the lines of these alerts.
The effect of Source port randomization against cache poisoning
According to the alert issued by JPRS, they made a request for DNS server administrators to randomize the UDP source port number from which caching DNS servers send out query packets as a mitigation against cache poisoning attacks.
Cache poisoning attack is a long-lasting threat on caching DNS servers, injecting arbitrary entry and diverting users to malicious web sites, mail servers, and so forth.
Dan Kaminsky disclosed, in 2008, his method to attack disabled TTL (Time-To-Live) protection by using "not cached data" as query name. This news astonished people because it enabled continuous attack, in fact, from “once in several hours” to “almost anytime”.
On the other hand, source port randomization is considered as the first-choice and mandatory mitigation. Because it increases difficulty for attackers to predict to which port in the range of randomized source port they should send malicious packets, source port randomization reduces the probability of successful attack by one over a few ten-thousands. This is the reason why JPRS recommends source port randomization.
But why did we re-emphasize the risk of cache poisoning attack and importance of source port randomization? JPRS described in their alert by referring to the two recent findings.
One is that JPRS had been informed by large ISPs in Japan that they are observing the increase of cache poisoning attacks with Kaminsky's method.
The other is that JPRS found that approximately 10% of source IP addresses, among the senders of DNS query to JP DNS Servers, did NOT randomize their source port yet.
JPRS kindly supplied a graph (Figure 1) which describes the proportion of the source port randomization observed. We can find several cliffs, swells and overall decline tendency. One of the cliffs might be the aftereffects of Kaminsky’s presentation or from the release of DNS software with randomized source port by default. And at last, 10% of the IP addresses still send queries from static (fixed) or limited (predictable) source ports.
Figure 1 Transition of source port randomization status (Apr-2006 to Apr-2014) by JPRS.
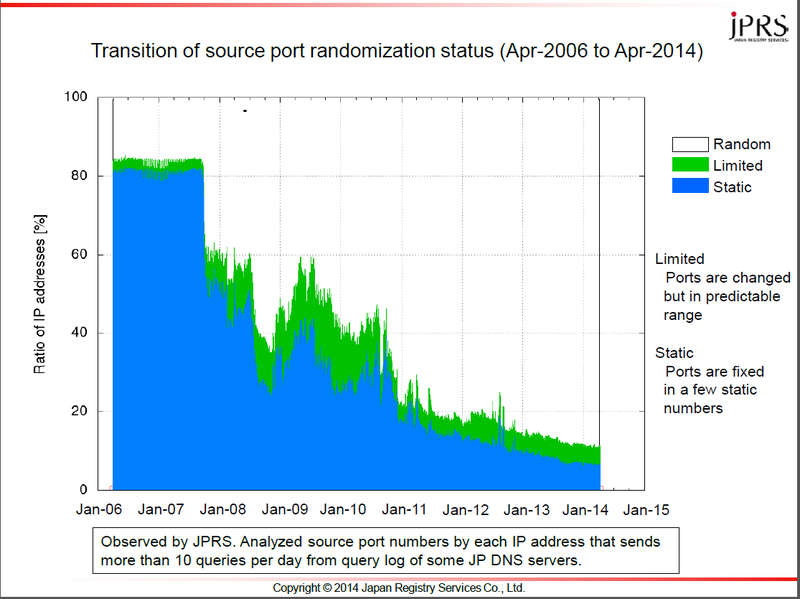 Source: JPRS (http://jprs.jp/tech/security/2014-04-15-portrandomization-status-e.pdf))
Source: JPRS (http://jprs.jp/tech/security/2014-04-15-portrandomization-status-e.pdf))
These findings imply, I think, a large number of caching DNS servers are still vulnerable to cache poisoning. This can escalate into domain name hijacking, etc. for the users of such caching DNS servers.
Our gratitude and action in the near future
Based on the list of vulnerable caching DNS servers provided by JPRS, JPCERT/CC is going to notify administrators to fix their setting. And it is our great pleasure to cooperate with other parties, just like we did with JPRS for handling this case.
Finally, I hope this blog entry will help address the issue and make the world of randomized source port :-)
Thank you.
Moto Kawasaki

