TSUBAME Report Overflow (Oct-Dec 2022)
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of October to December 2022. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here.
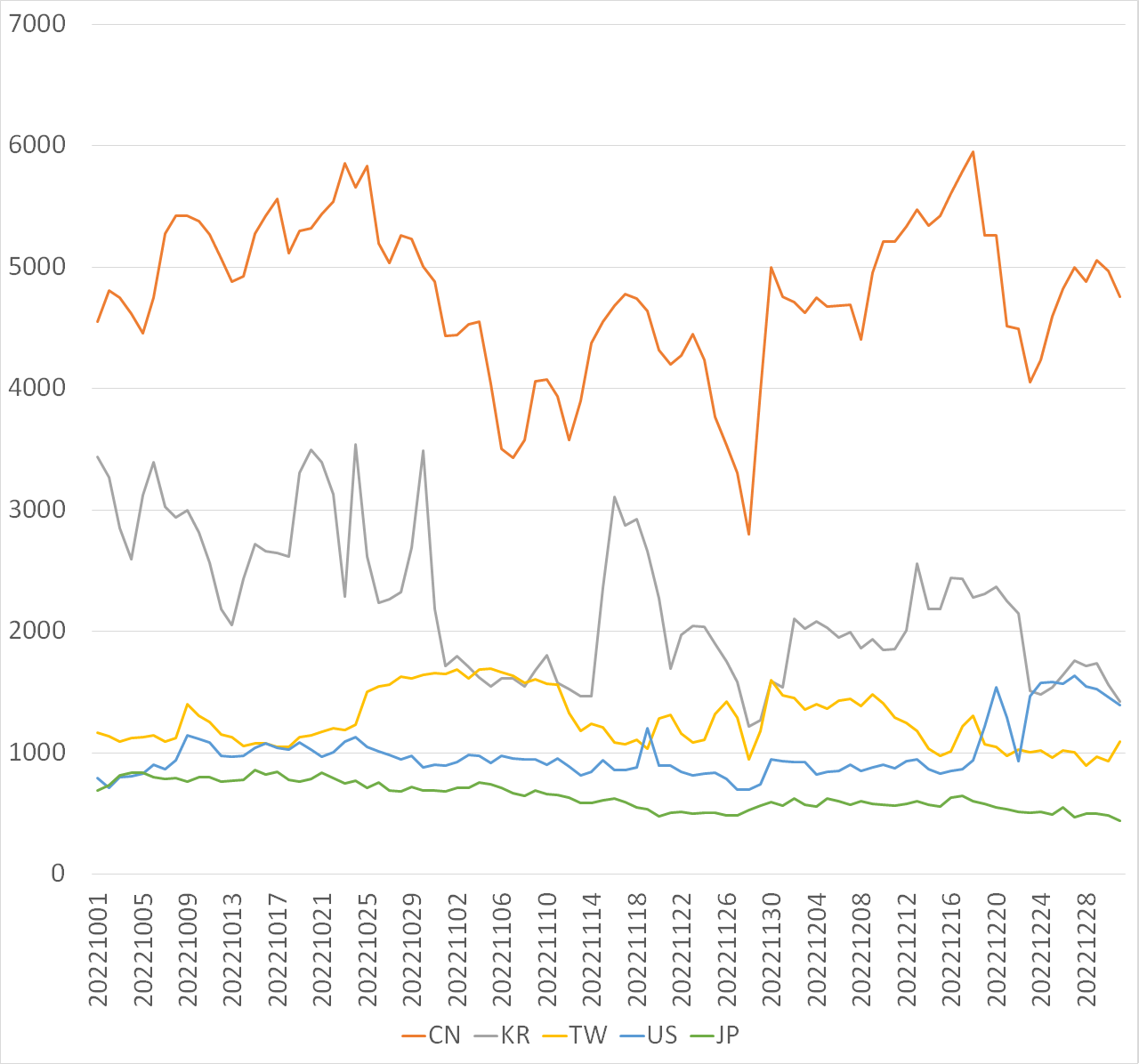
Changes in Mirai-type packets in Japan (Top 5 source regions)
Figure 1 shows a daily graph of the top 5 IP addresses by source region for packets with Mirai-type characteristics observed by TSUBAME, and Figure 2 shows a daily graph of the total number and that of the top 5 combined.
 |
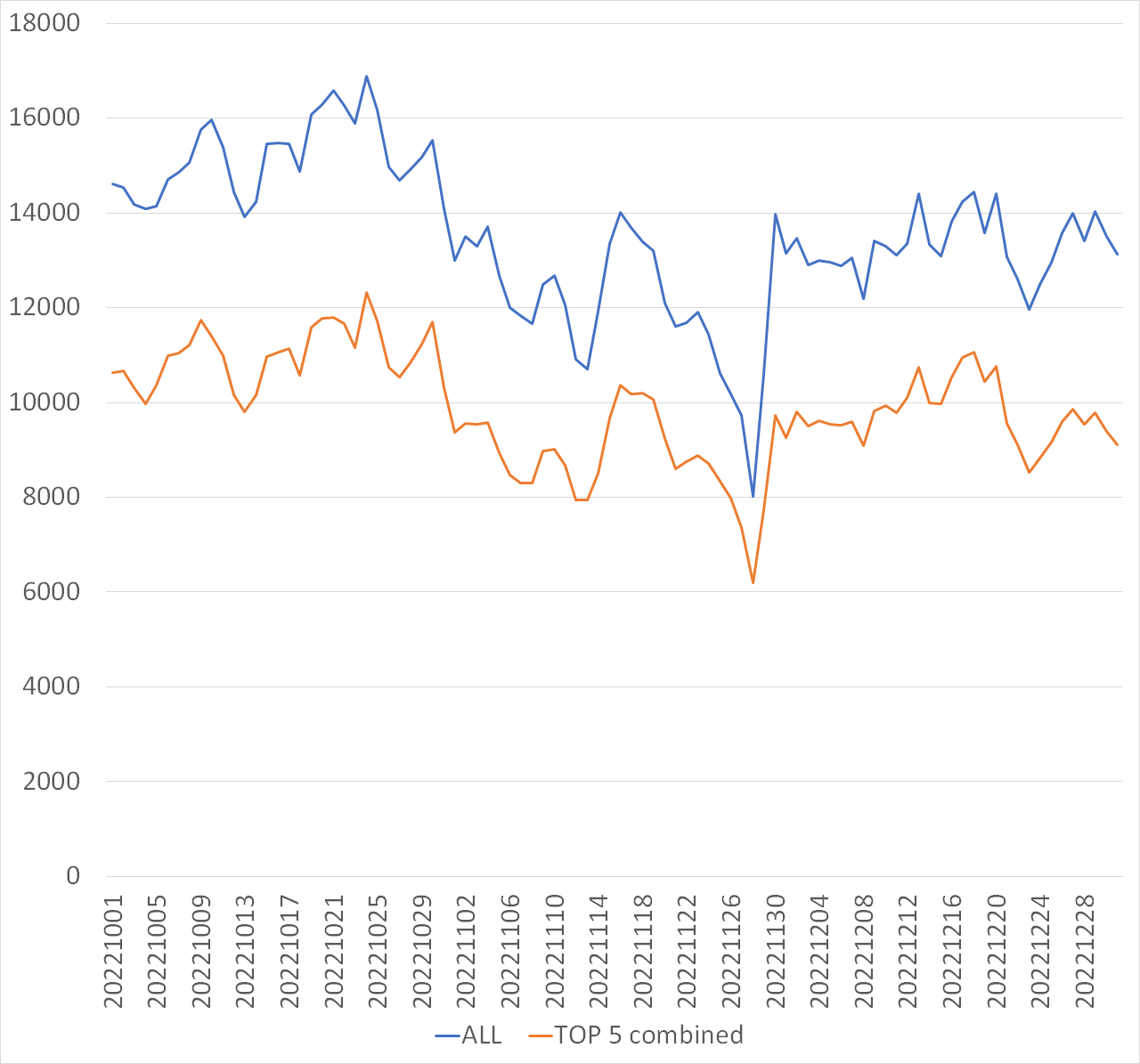 |
| Figure 1: Number of Mirai-type hosts for each source region | Figure 2: Total number of Mirai-type hosts and that of the top 5 combined |
Comparison of the observation trends in Japan and overseas
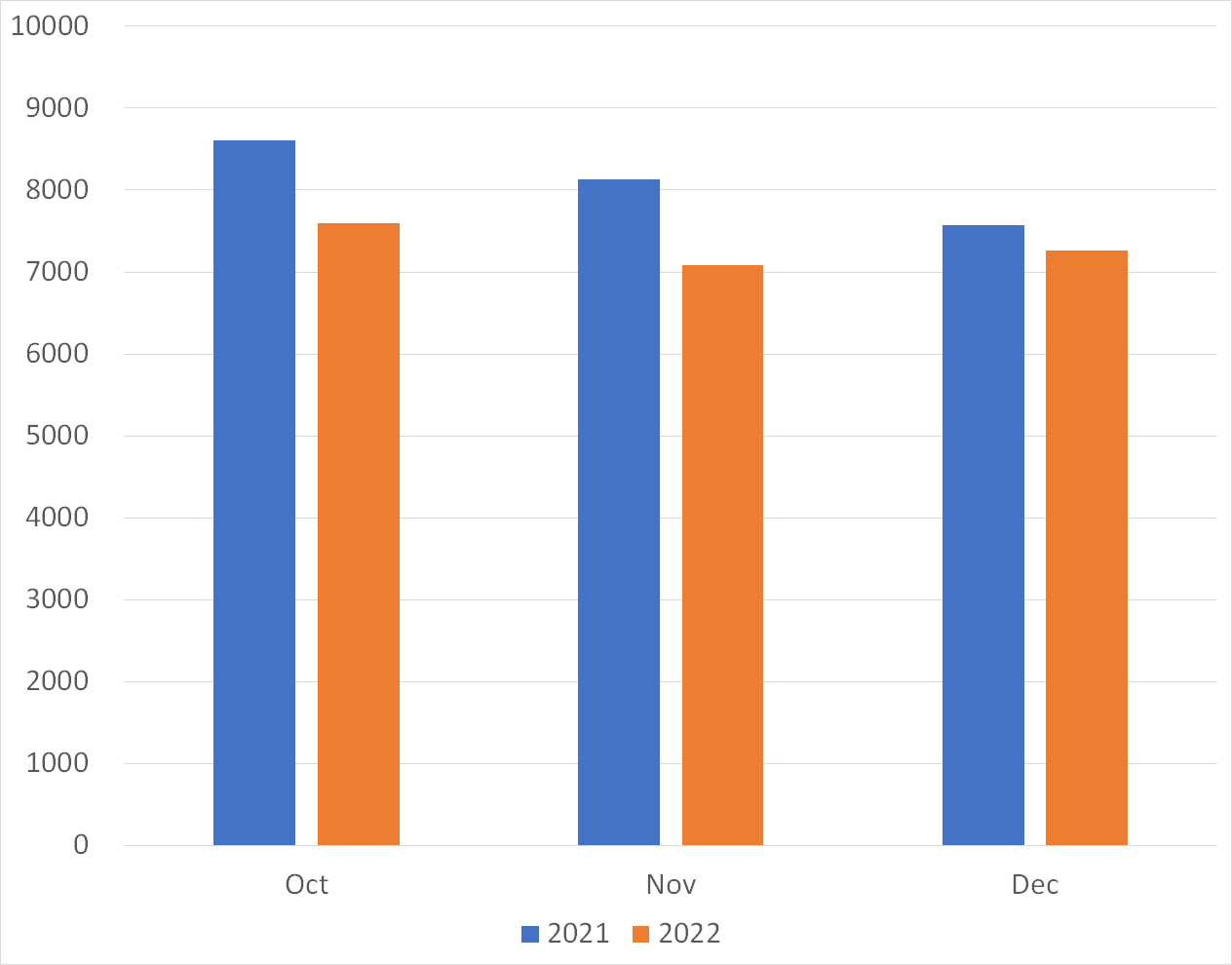
Figures 3 and 4 show a monthly comparison of the average number of packets received per day by each sensor in Japan and overseas. More packets were observed by overseas sensors than those in Japan.
 |
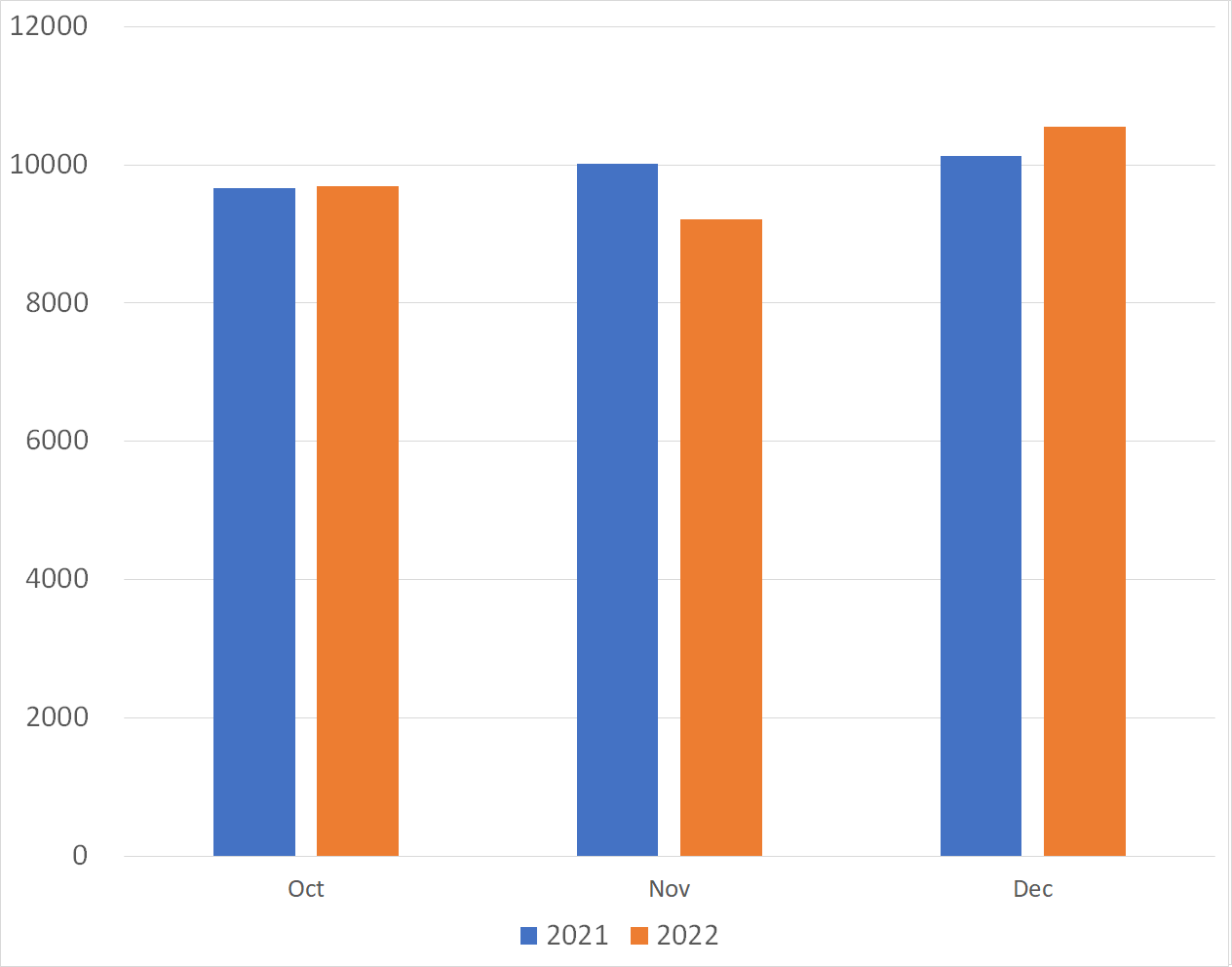 |
| Figure 3: Average number of packets to domestic sensors | Figure 4: Average number of packets to overseas sensors |
Comparison of monitoring trends by sensor
A global IP address is assigned to each TSUBAME sensor. Table 2 shows the top 10 ports of each sensor which received packets the most. The top 6 ports are the same in every sensor in Japan, while they were different from overseas sensors. Many sensors observe the packets for 23/TCP the most, and 6379/TCP is also in the top 10 on many sensors. This suggests that these protocols are being scanned in a wide range of networks.
Table 1: Comparison of top 10 packets by domestic and overseas sensors
| #1 | #2 | #3 | #4 | #5 | #6 | #7 | #8 | #9 | #10 | |
| Domestic sensor 1 | 23/TCP | 6379/TCP | 80/TCP | 22/TCP | 445/TCP | 443/TCP | 81/TCP | 8088/TCP | 8080/TCP | 5555/TCP |
| Domestic sensor 2 | 23/TCP | 6379/TCP | 80/TCP | 22/TCP | 445/TCP | 443/TCP | 5555/TCP | 81/TCP | 8080/TCP | 1433/TCP |
| Domestic sensor 3 | 23/TCP | 6379/TCP | 80/TCP | 22/TCP | 445/TCP | 443/TCP | 5555/TCP | 81/TCP | 8080/TCP | 1433/TCP |
| Overseas sensor 1 | 6379/TCP | 80/TCP | ICMP | 5555/TCP | 443/TCP | 81/TCP | 2375/TCP | 5060/UDP | 2323/TCP | 2376/TCP |
| Overseas sensor 2 | 23/TCP | 6379/TCP | ICMP | 80/TCP | 22/TCP | 5555/TCP | 443/TCP | 5060/UDP | 1433/TCP | 8080/TCP |
| Overseas sensor 3 | 23/TCP | 6379/TCP | 22/TCP | 5555/TCP | 3389/TCP | 80/TCP | ICMP | 443/TCP | 81/TCP | 1433/TCP |
In Closing
Monitoring at multiple points makes it possible to see whether some trends are unique to a particular network. Although we have not published any special alerts as an extra issue or other information this quarter, it is important to pay attention to scanners. We will continue to publish blog articles as the Internet Threat Monitoring Quarterly Report becomes available every quarter. We will also publish an extra issue when we observe any unusual change. Your feedback on this series is much appreciated. Please use the below comment form to let us know which topic you would like us to introduce or discuss further. Thank you for reading.
Keisuke Shikano (Translated by Takumi Nakano)

