JPCERT/CC held ICS Security Conference 2023 on February 9, 2023. The purpose of the conference is to share the current status of threats in ICS both in Japan and abroad as well as efforts by ICS security stakeholders. It also aims to help participants improve their ICS security measures and establish best practices. The conference has been held annually since 2009, and this year’s was the 15th conference.This is the...
List of “2023”
-
-
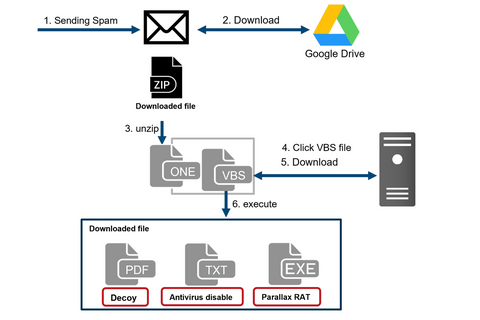
Around February 2023, JPCERT/CC identified an attack that attempted to infect a crypto asset exchanger with the Parallax RAT malware. This attack attempted to infect employees of the crypto asset exchanger with malware by sending spam emails. This article presents the details of this attack.Flow of events leading to Parallax RAT infectionFigure 1 shows the flow of this attack. The identified attack starts with a spam email, which urges the...
-
We continue to introduce the talks at JSAC2023. This third issue covers the workshops on Day 2. Surviving the hurt locker: or How I Learned to Stop Worrying and Love the Bom Speakers: Simon Vestin, Manabu Niseki (LINE) Simon and Manabu explained the SBOM (Software Bill of Materials) and gave a hands-on session on creating a program to generate one. SBOM is a list of software or system components. They...
-
This article reports on JSAC Day 2, following the previous article about Day1. How Do We Fight against Evolving Go Language Malware? Practical Techniques to Increase Analytical Skills Speakers: Tsubasa Kuwabara (FFRI Security Inc.) Slides (English) Tsubasa presented the current situation and problems of Go language malware, which has been increasing in recent years, and explained basic and advanced analysis techniques. He explained that Go malware was easy to write...
-
What is ITU-T X.1060? X.1060 Framework for the creation and operation of a cyber defence centre[1]is a recommendation document approved by ITU-T, the United Nations specialized agency for information and communication technologies. It defines a cyber security framework which can be used as a reference by a wide range of organisations, regardless of their sizes or industries. The document illustrates a blueprint for Cyber Defence Centre (hereafter CDC), an entity...
-
JPCERT/CC held JSAC2023 on January 25 and 26, 2023. The purpose of this conference is to raise the knowledge and technical level of security analysts in Japan, and we aimed to bring them together in one place where they can share technical knowledge related to incident analysis and response. This year was the sixth time the conference was held, and 12 presentations, 2 workshops, and 7 lightning talks were presented...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of October to December 2022. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Changes in Mirai-type packets in Japan (Top 5 source regions) Figure 1 shows a daily graph of...
-
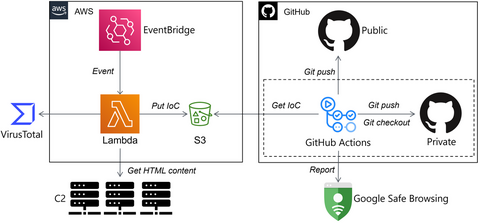
I believe that automating analysis is a challenge that all malware analysts are working on for more efficient daily incident investigations. Cloud-based technologies (CI/CD, serverless, IaC, etc.) are great solutions that can automate MAOps efficiently. In this article, I introduce how JPCERT/CC automates malware analysis on the cloud, based on the following case studies. Malware C2 Monitoring Malware Hunting using Cloud YARA CI/CD system Surface Analysis System on Cloud Memory...