JPCERT/CC released the latest version (v1.6) of LogonTracer, a tool to support event log analysis. Previously, LogonTracer could not investigate multiple incidents simultaneously, but this update adds support for managing multiple logs. In addition, Sigma can now be used to investigate the presence of suspicious logs in the event log. This article introduces these updates. For other updated items, please refer to the following release: https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.6.0 Log Management Feature When...
-
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of April to June 2022. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Observation trends of packets from scanners in Japan TSUBAME observes packets from a variety of sources. It...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of April to June 2022. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Changes in Mirai-type packets in Japan The top 5 ports for the number of packets with Mirai-type...
-
Around May 2022, JPCERT/CC confirmed an attack activity against Japanese organizations that exploited F5 BIG-IP vulnerability (CVE-2022-1388). The targeted organizations have confirmed that data in BIG-IP has been compromised. We consider that this attack is related to the activities by BlackTech attack group. This blog article describes the attack activities that exploit this BIG-IP vulnerability. Attack code that exploits the BIG-IP vulnerability Below is a part of the attack code...
-
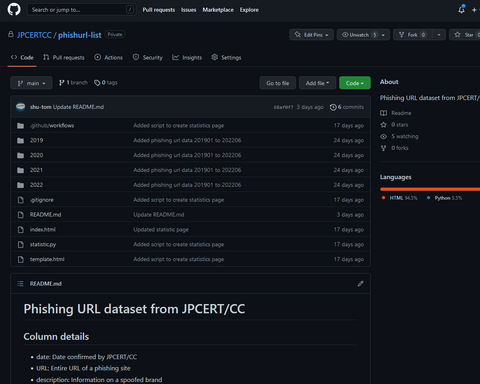
JPCERT/CC releases a URL dataset of phishing sites confirmed from January 2019 to June 2022, as we received many requests for more specific information after publishing a blog article on trends of phishing sites and compromised domains in 2021. The list is available in the following GitHub repository. Phishing URL dataset from JPCERT/CC https://github.com/JPCERTCC/phishurl-list/ Each column contains the following: date: Date confirmed by JPCERT/CC URL: Entire URL of a phishing...
-
Hello. I am Noriko Totsuka from Early Warning Group. The Early Warning Group publishes security information such as security alerts and early warning information, as well as JVN Advisories. As a vulnerability coordinator, I am in charge of a series of coordination tasks, from coordinating with developers of target products, including taking countermeasures based on the vulnerability-related information reported to JPCERT/CC by vulnerability finders such as security researchers, to the...
-
JPCERT/CC is continuously investigating the activities by Lazarus. In ...
-
Some types of malware use DGA, obfuscate destination information, or c...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of October to December 2021. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Looking back on 2021 Figure 1 shows a comparison and transition of the total number of IP...
-
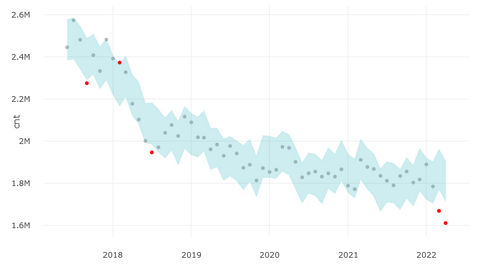
JPCERT/CC Cyber Metrics Group utilizes various kinds of data in order to understand what is happening on the Internet and call for appropriate cybersecurity measures based on the analysis. For example, we operate TSUBAME [1], an Internet threat monitoring system, and Mejiro [2] , an Internet risk visualization service. In this article, we used data from Shodan Trends to check how the recent situation in Ukraine looks on the Internet....





.png)