Malware Gh0stTimes Used by BlackTech
An attack group BlackTech has been actively conducting attacks against Japanese organisations since 2018. Although it is not as prominent as before, JPCERT/CC is still seeing some cases as of now. This article introduces the details of the malware Gh0stTimes, which is used by this group.
Gh0stTimes overview
Gh0stTimes is customised based on Gh0st RAT and has been used in some attack cases since 2020. Figure 1 shows the comparison of Gh0stTimes and Gh0st RAT code.
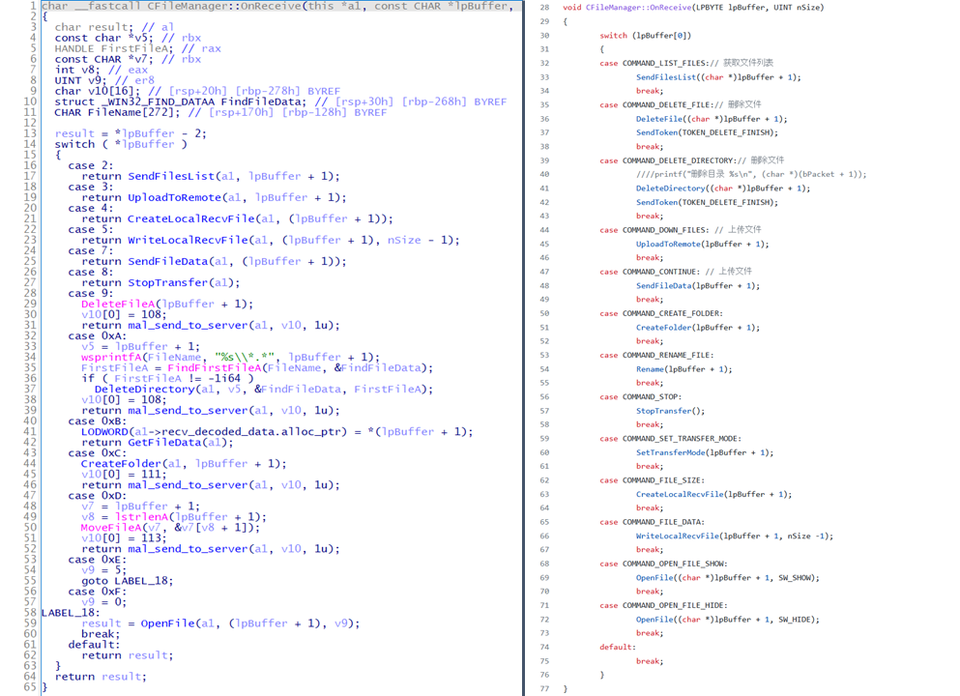
(Left: Gh0stTimes / Right: Gh0st RAT)
Both sets of code are functions for file operation, and they are almost identical. Many of the Gh0st RAT functions are upgraded in Gh0stTimes, but some parts of the code are just kept as is. The next sections explain the features of Gh0stTimes.
- Communication protocol
- Commands
- Dummy code
- C2 server control panel
Communication protocol
Just like Gh0st RAT, Gh0stTimes communicates with C2 servers with its custom protocol, but the packet format is different. Figure 2 shows the flow of communication.
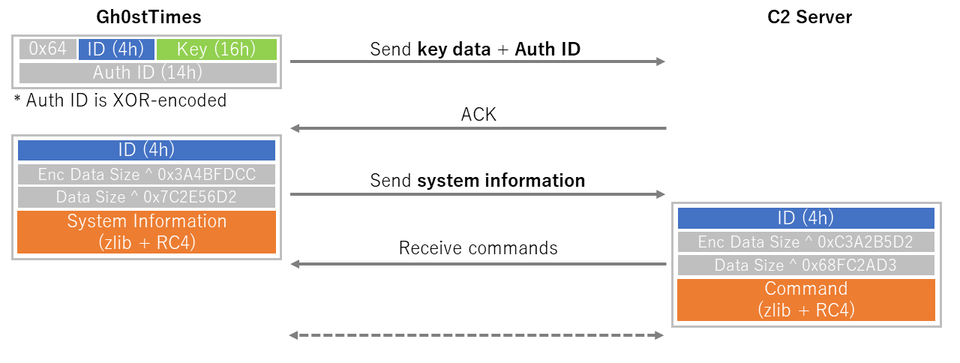
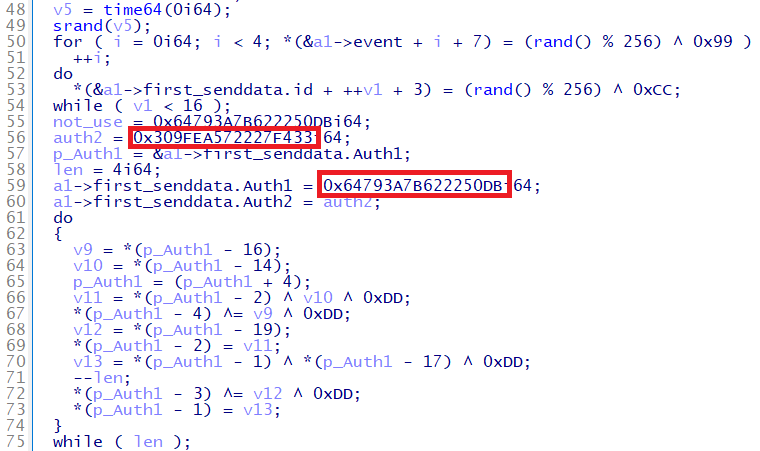
At the beginning of its communication with a C2 server, Gh0stTimes sends an authentication ID and data (The "Key" in Figure 2) to generate an encryption key for the following communication. The C2 server checks the authentication ID and only accepts the communication with certain IDs. Figure 3 shows an example of the specific authentication IDs.
After the successful authentication, the communication that follows is encrypted with the key provided at the beginning of the communication. The next round of communication includes the information of infected hosts, such as hostname, username and processor name (Figure 4).
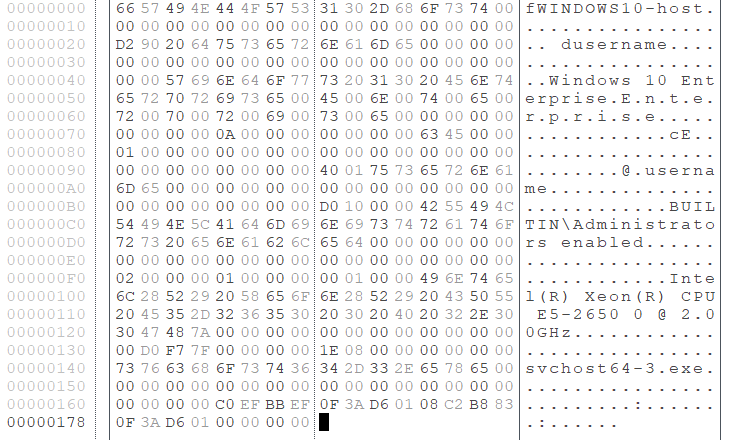
After sending the information of infected hosts, commands are exchanged. See Appendix A for the format of data exchanged. When exchanging commands, the data is RC4-encrypted and then zlib-compressed. Gh0stTimes uses its custom RC4 algorithm, which has XOR 0xAC process over the encrypted data.
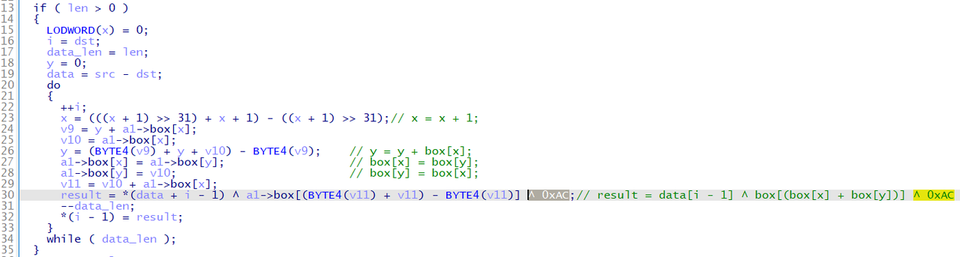
The following is Python code to decode data exchanged.
import zlib # Load keydata for first packet with open(args[1], "rb") as fb: keydata = fb.read() # Load encoded packet data with open(args[2], "rb") as fb: data = fb.read() comp_data = custom_rc4(data[12:], keydata[5:21]) dec_data = zlib.decompress(comp_data) def custom_rc4(data, keydata): key = [] key_1 = [0x98, 0x19, 0x3C, 0x56, 0xD9, 0xBB, 0xC7, 0x86, 0xFF, 0x3E] key_2 = [0] * 16 key_3 = [0xAC, 0xBB, 0x30, 0x5E, 0xCC, 0xDD, 0x19, 0x23, 0xFC, 0xBD] keybox = [7, 0, 2, 3, 9, 10, 4, 13, 14, 8, 1, 11, 5, 6, 12, 15] i = 0 for i in range(16): key_2[i] = keydata[keybox[i]] key = key_1 + key_2 + key_3 x = 0 box = list(range(256)) for i in range(256): x = (x + box[i] + key[i % len(key)]) % 256 box[i], box[x] = box[x], box[i] x = 0 y = 0 out = [] for char in data: x = (x + 1) % 256 y = (y + box[x]) % 256 box[x], box[y] = box[y], box[x] out.append((char ^ box[(box[x] + box[y]) % 256] ^ 0xAC).to_bytes(1, byteorder='little')) return b''.join(out)
Commands
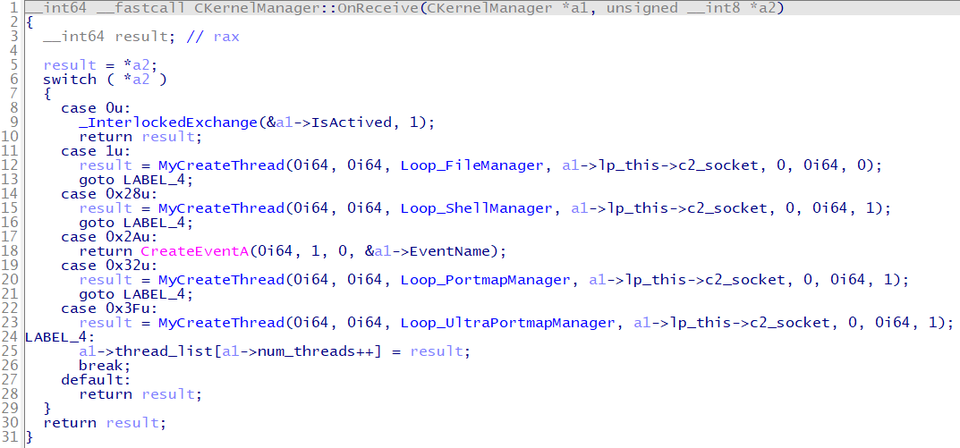
Gh0stTimes is equipped with the following 5 types of commands:
- FileManager (command number 0x1): File operation
- ShellManager (command number 0x28): Remote shell execution
- PortmapManager (command number 0x32): C2 server redirect function
- UltraPortmapManager (command number 0x3F): Proxy function
- No name (command number 0): End communication
ShellManager and FileManager are the same as Gh0st RAT's original functions. FileManager has multiple functions to operate files on infected hosts. (See Appendix B for details.)
PortmapManager and UltraPortmapManager are unique to Gh0stTimes, which indicates that its relay function has been enhanced compared to Gh0st RAT.
Dummy code
Some types of malware that BlackTech use contains dummy code, which may make analysis difficult. Gh0stTimes has such code (Figure 7), but it does not have much impact to the analysis.
C2 server control panel
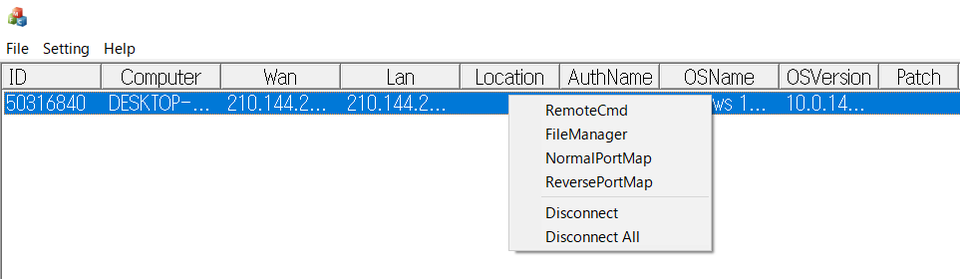
In the course of analysis, we found Gh0stTimes control panel. Figure 8 shows its GUI when the control panel is running. This one was named as "Times v1.2".
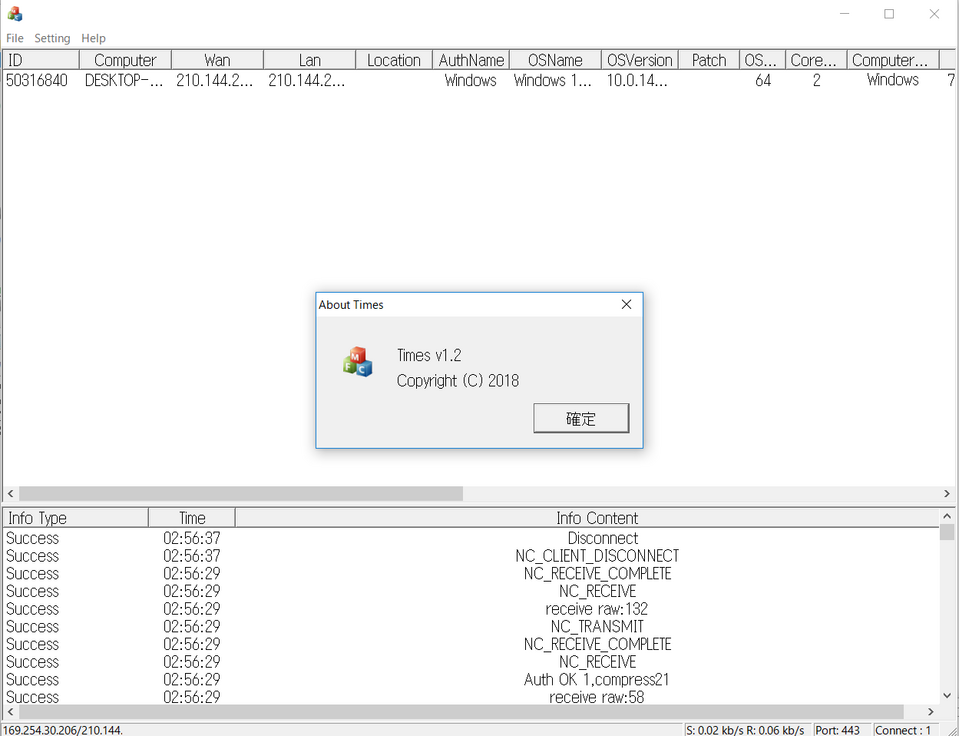
Figure 9 shows the commands that can be executed on the control panel.
In closing
As BlackTech has been actively carrying out attacks, we will continue our analysis and monitoring. A list of IoC is available in Appendix C. Please make sure that none of your devices is communicating with them.
We have identified that servers infected with Gh0stTimes are also affected by other types of malware (downloader, backdoor, ELF Bifrose) and attack tools listed below. Please be aware that these tools are possibly used by BlackTech.
- https://github.com/Yang0615777/PocList
- https://github.com/liuxu54898/CVE-2021-3019
- https://github.com/knownsec/pocsuite3
- Citrix exploit tool
- MikroTik exploit tool
- Exploit for CVE-2021-28482
- Exploit for CVE-2021-1472/CVE-2021-1473
- Exploit for CVE-2021-28149/CVE-2021-28152
- Exploit for CVE-2021-21975/CVE-2021-21983
- Exploit for CVE-2018-2628
- Exploit for CVE-2021-2135
Acknowledgement
We would like to acknowledge the support and information shared by @r3dbU7z regarding this attack group.
Shusei Tomonaga
(Translated by Yukako Uchida)
Appendix A: Data exchanged
| Offset | Length | Contents |
| 0x00 | 4 | ID |
| 0x04 | 4 | Data length xor 0x3A4BFDCC |
| 0x08 | 4 | Data length after 0x0C before compression xor 0x7C2E56D2 |
| 0x0C | - | Encrypted data (zlib + RC4) |
| Offset | Length | Contents |
| 0x00 | 4 | ID |
| 0x04 | 4 | Data length xor 0xC3A2B5D2 |
| 0x08 | 4 | Data length after 0x0C before compression xor 0x68FC2AD3 |
| 0x0C | - | Encrypted data (zlib + RC4) |
Appendix B: Commands
| Value | Contents |
| 2 | SendFilesList |
| 3 | UploadToRemote |
| 4 | CreateLocalRecvFile |
| 5 | WriteLocalRecvFile |
| 7 | SendFileData |
| 8 | StopTransfer |
| 9 | DeleteFile |
| 10 | DeleteDirectory |
| 11 | GetFileData |
| 12 | CreateFolder |
| 13 | MoveFile |
| 14 | OpenFile(SW_SHOW) |
| 15 | OpenFile(SW_HIDE) |
Appendix C: C2 servers
- tftpupdate.ftpserver.biz
- 108.61.163.36
- update.centosupdates.com
- 107.191.61.40
- osscach2023.hicloud.tw
- 103.85.24.122
- 106.186.121.154
Appendix D: Malware hash value
- 01581f0b1818db4f2cdd9542fd8d663896dc043efb6a80a92aadfac59ddb7684
- 18a696b09d0b7e41ad8ab6a05b84a3022f427382290ce58f079dec7b07e86165
- 15b8dddbfa37317ccdfbc340764cd0f43b1fb8915b1817b5666c4816ccb98e7c
- 849ec6055f0c18eff76170912d8500d3da7be1435a9117d67f2134138c7e70c3
- f19ab3fcbc555a059d953196b6d1b04818a59e2dc5075cf1357cee84c9d6260b
- 836b873ab9807fbdd8855d960250084c89af0c4a6ecb75991542a7deb60bd119
- a69a2b2a6f5a68c466880f4c634bad137cb9ae39c2c3e30c0bc44c2f07a01e8a
- bd02ca03355e0ee423ba0e31384d21b4afbd8973dc888480bd4376310fe6af71