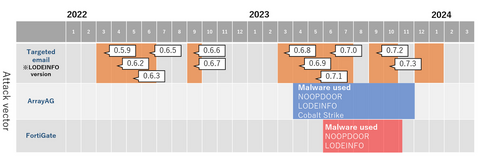
JPCERT/CC has been observing attack activities by MirrorFace LODEINFO ...
List of “LODEINFO”
-
-
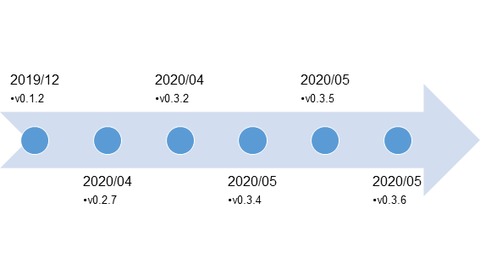
The functions and evolution of malware LODEINFO have been described in our past articles in February 2020 and June 2020. Yet in 2021, JPCERT/CC continues to observe activities related to this malware. Its functions have been expanding with some new commands implemented or actually used in attacks. This article introduces the details of the updated functions and recent attack trends. LODEINFO versions At the time of the last blog update,...
-
We introduced malware LODEINFO in a past blog entry. Attacks using the malware have been continuously seen, in particular with malicious file names including those related to COVID-19. It is also confirmed that LODEINFO has been updated frequently, and several functions have been added or changed in the latest version. This article will introduce trends seen in the series of attacks and updates to the malware. LODEINFO distribution Cases that...
-
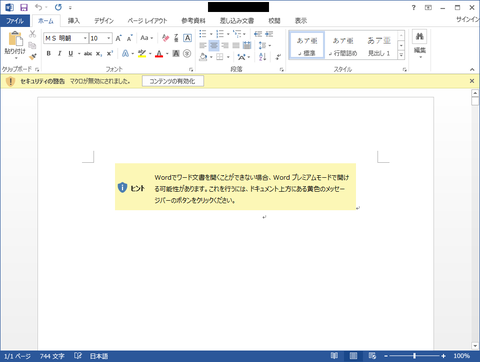
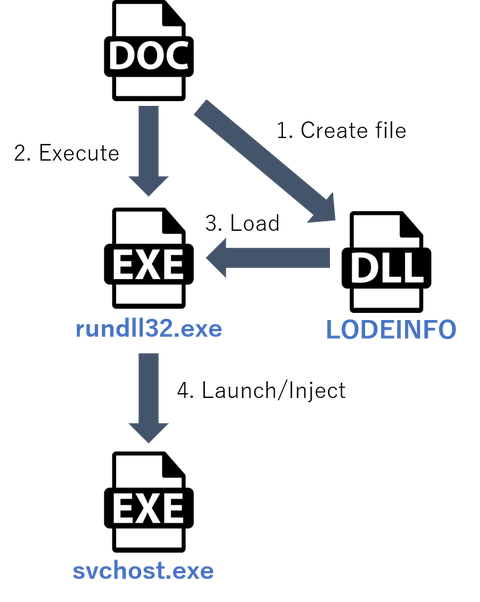
JPCERT/CC has been observing a new type of spear-phishing emails targeting Japanese organisations since December 2019. The emails have a malicious Word file attachment leading to malware “LODEINFO”, which is newly observed. This article introduces the details of this malware. How LODEINFO is launched Figure 1 describes the flow of events from executing a Word file until LODEINFO is launched. Figure 1:Flow of events until LODEINFO runs By enabling the...