BLINDINGCAN - Malware Used by Lazarus -
In the previous article, we introduced one type of malware that Lazarus (also known as Hidden Cobra) uses after network intrusion. It is confirmed that this attack group uses multiple types of malware including BLINDINGCAN, which CISA recently introduced in its report [1].
This article summarises the result of our analysis on BLINDINGCAN.
BLINDINGCAN overview
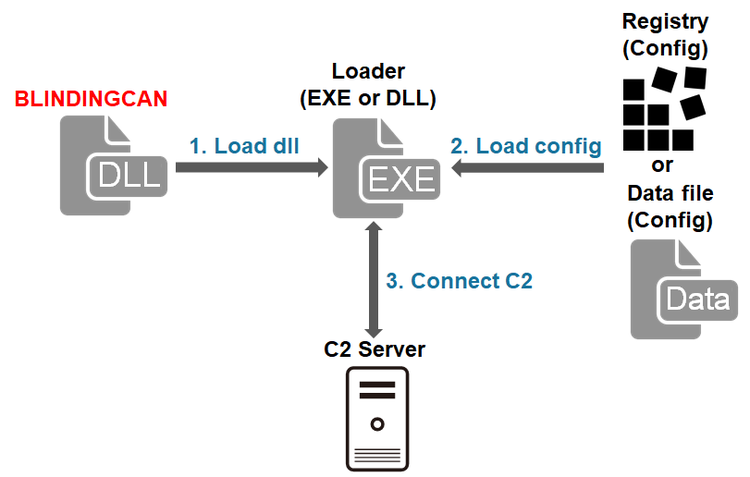
The malware runs when a loader loads a DLL file. Figure 1 shows the flow of events until BLINDINGCAN runs. JPCERT/CC has confirmed that the DLL file is encoded in some samples (which requires decoding by the loader before execution).
BLINDINGCAN shares some features with the aforementioned malware including its function and communication encoding algorithm. The following sections will explain its configuration and communication protocol.
Configuration
The configuration of BLINDINGCAN(size: 0xA84) is stored in one of the following locations:
- Hardcoded in the malware itself
- Stored in a registry entry
- Saved as a file
In case it is saved as a file, it is stored in the same folder where BLINDINGCAN is located. We have confirmed that the following directory is used if the configuration is stored in a registry entry.
Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion Value: "SM_Dev16[numeric string]"
The configuration is encrypted using either XOR encoding, AES or RC4. The encryption key is either fixed or generated based on the environment of the infected device. JPCERT/CC has confirmed the following patterns of encryption keys:
- [File name][Export function name][Service name]
- [CPUID][Computer name][Processor name][Physical memory size]
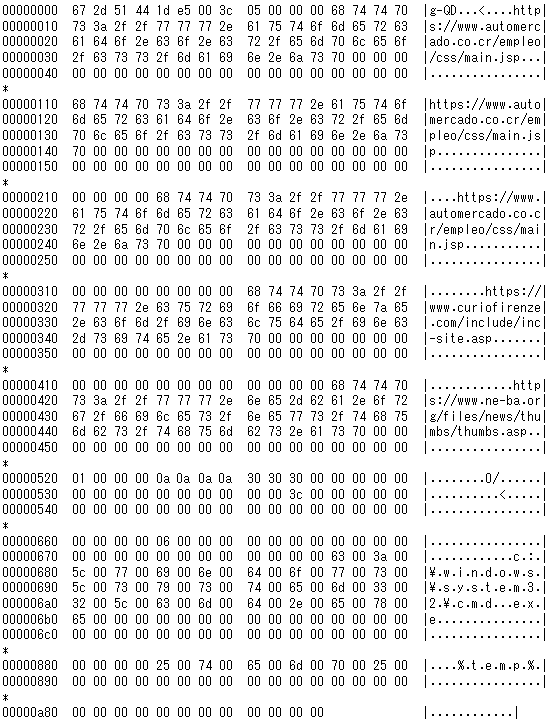
Figure 2 shows an example of decoded configuration. This includes proxy information as well as C&C server information. (Please see Appendix A for details.)
Obfuscation
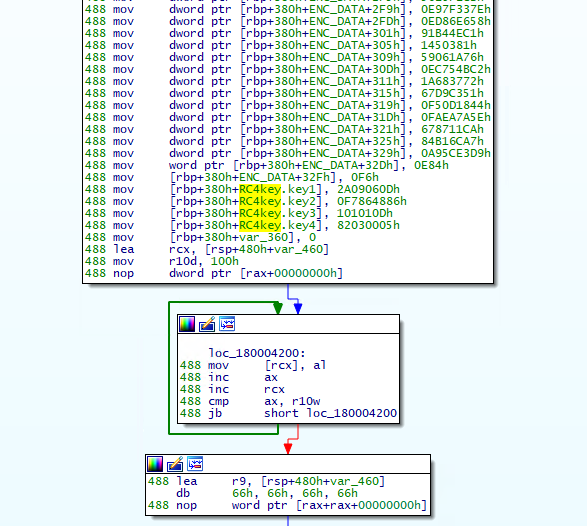
Some part of code in BLINDINGCAN is obfuscated using RC4. Figure 3 is an example of obfuscated code. The RC4 encryption key is hardcoded in the sample itself.
Communication with C&C server
Below is an example HTTP POST request data that BLINDINGCAN sends in the beginning.
POST /[PATH] HTTP/1.1 Connection: Keep-Alive Cache-Control: no-cache Content-Type: application/x-www-form-urlencoded Accept: */* User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) Chrome/28.0.1500.95 Safari/537.36 Host: [Server] Content-Length: [Length] id=d3Ztd3lod2t0Tqf42ux9uv3FGH+Y3oAc2w==&bbs=HA==&tbl=hzE4dlKcRq3gokgAGeMQug== &bbs_form=4GQAAA==
The format of the data is as follows. (All the values except for the RC4 key is RC4-encrypted and Base64-encoded.) The param2 in the first HTTP POST request is the encoded value of a string "T1B7D95256A2001E".
id=[RC4 key][param1:param2:param3]&[param1]=[Random value (between 1000 and 10000)]&[param2]=["T1B7D95256A2001E"]&[param3]=[Random binary data]
The parameters in the POST data (param1, param2, param3) are randomly selected from the below:
boardid,bbsNo,strBoardID,userid,bbs,filename,code,pid,seqNo,ReportID,v,PageNumber,num,view,read,action,page,mode,idx,cateId,bbsId,pType,pcode,index,tbl,idx_num,act,bbs_id,bbs_form,bid,bbscate,menu,tcode,b_code,bname,tb,borad01,borad02,borad03,mid,newsid,table,Board_seq,bc_idx,seq,ArticleID,B_Notice,nowPage,webid,boardDiv,sub_idxa
The RC4 encryption used here is different from the regular one. It has a process to shift the key stream for C00h times. The following is the RC4 encryption process written in Python. It does not apply to param3, which uses the regular RC4.
def custom_rc4(data, key):
x = 0
box = list(range(256))
for i in range(256):
x = (x + int(box[i]) + int(key[i % len(key)])) % 256
box[i], box[x] = box[x], box[i]
x = 0
for i in range(0xC00):
i = i + 1
x = (x + int(box[i % 256])) % 256
wow_x = x
box[i % 256], box[x] = box[x], box[i % 256]
wow_y = i % 256
x = wow_y
y = wow_x
out = []
for char in data:
x = (x + 1) % 256
y = (y + box[x]) % 256
box[x], box[y] = box[y], box[x]
out.append(chr(char ^ box[(box[x] + box[y]) % 256]))
return ''.join(out)
Figure 4 is the flow of communication from the beginning of its communication with a C&C server until receiving commands.
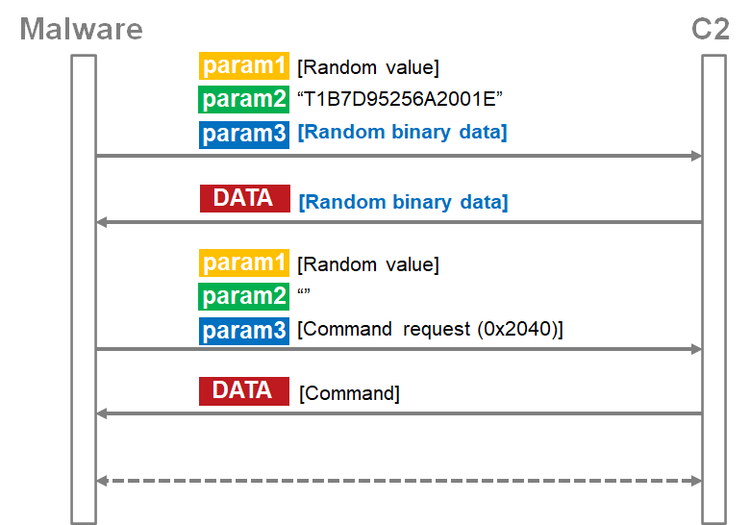
If a Base64-encoded value of param3 ([Random binary data] in Figure 4) is received from the server as a response to the first request, the malware sends another request.
The next data is sent with empty param2 and a command request (Command request (0x2040) in Figure 4) in param3. (Please see Appendix B for the details of param3 format.) The data in param3 is XOR-encoded, RC4-encrypted and then Base64-encoded.
After that BLINDINGCAN receives a command from a C&C server. (The format of the response data is the same as param3. Please see Appendix B). The response data is also XOR-encoded, RC4-encrypted and Base64-encoded. The only difference is that the "+" sign is replaced by a space.
Commands
BLINDINGCAN performs multiple functions including the following. (Please see Appendix C for details.)
- Operation on files (create a list, delete, move, modify timestamp, copy)
- Operation on processes (create a list, execute, kill)
- Upload/download files
- Obtain disk information
- Obtain a list of services
- Execute arbitrary shell command
In closing
We have introduced two kinds of malware used by Lazarus so far. However, they are known to use other types of malware as well. We will provide an update if we observe any new kind of malware.
The C&C server information of the samples mentioned in the article are listed in Appendix D. Please make sure that none of your device is communicating with these hosts.
Shusei Tomonaga
(Translated by Yukako Uchida)
Reference
[1] CISA: Malware Analysis Report (AR20-232A)
https://us-cert.cisa.gov/ncas/analysis-reports/ar20-232a
Appendix A: Configuration
| Offset | Description | Remarks |
| 0x000 | Number of C&C servers | Up to 5 |
| 0x004 | C&C server 1 | |
| 0x108 | C&C server 2 | |
| 0x20C | C&C server 3 | |
| 0x310 | C&C server 4 | |
| 0x414 | C&C server 5 | |
| 0x518 | Flag for proxy | |
| 0x51C | Proxy IP address | |
| 0x520 | Proxy port number | |
| 0x522 | Flag for C&C reply | |
| 0x526 | Flag for drive information | |
| 0x52A | Flag for session information | |
| 0x52E | Save configuration | |
| 0x532 | Communication interval | |
| 0x534 | Start time | |
| 0x53C | seed | Used when generating random data to send |
| 0x59C | File name | File obtained by the command "0x2039" |
| 0x5FC | Unknown | |
| 0x65C | Unknown | |
| 0x660 | Not assigned | |
| 0x674 | Execute process name | Contains "c:¥windows¥system32¥cmd.exe" |
| 0x87C | Temp folder | Command execution result is stored |
Appendix B: Contents of data exchanged
| Offset | Length | Contents |
| 0x00 | 2 | Not assigned |
| 0x02 | 2 | Command |
| 0x04 | 4 | Not assigned |
| 0x08 | 4 | Parameter length |
| 0x0C | - | Parameter (Base64 + RC4) |
Appendix C: Commands
| Value | Contents |
| 0x2009 | Get system information |
| 0x2010 | Get drive information |
| 0x2011 | Get directory list |
| 0x2012 | Execute command (Regular output) |
| 0x2013 | Upload file (compressed in zlib) |
| 0x2014 | Download file |
| 0x2015 | Execute process |
| 0x2016 | Execute process (CreateProcessAsUser) |
| 0x2019 | Get process list |
| 0x2020 | Kill process |
| 0x2021 | Delete file (sdelete) |
| 0x2022 | Check connection |
| 0x2023 | Change current directory |
| 0x2027 | Modify file creation time |
| 0x2028 | Change communication interval with C&C server |
| 0x2029 | End session with C&C server |
| 0x2030 | Uninstall |
| 0x2031 | Get configuration |
| 0x2032 | Overwrite configuration |
| 0x2033 | Get directory information |
| 0x2034 | Get drive available space |
| 0x2037 | - |
| 0x2038 | Sleep |
| 0x2039 | Get file name |
| 0x2046 | Write file |
| 0x2048 | Copy file |
| 0x2049 | Move file |
| 0x2050 | Delete file |
Appendix D: C&C server
- https://www.automercado.co.cr/empleo/css/main.jsp
- https://www.curiofirenze.com/include/inc-site.asp
- https://www.ne-ba.org/files/news/thumbs/thumbs.asp
- https://www.sanlorenzoyacht.com/newsl/include/inc-map.asp
Appendix E: Sample hash value
- 8db272ea1100996a8a0ed0da304610964dc8ca576aa114391d1be9d4c5dab02e
- 58027c80c6502327863ddca28c31d352e5707f5903340b9e6ccc0997fcb9631d