ELF_PLEAD - Linux Malware Used by BlackTech
In a past article, we introduced Linux malware ELF_TSCookie, which is used by an attack group BlackTech. This group also uses other kinds of malware that affects Linux OS. PLEAD module for Windows which we introduced before has its Linux version (ELF_PLEAD) as well. This article describe the details of ELF_PLEAD in comparison to PLEAD module.
Comparison between PLEAD Module and ELF_PLEAD
ELF_PLEAD and PLEAD module share many parts of the code, and most of the functions including communication are similar. Figure 1 shows the comparison of the main functions of PLEAD module and ELF_PLEAD.
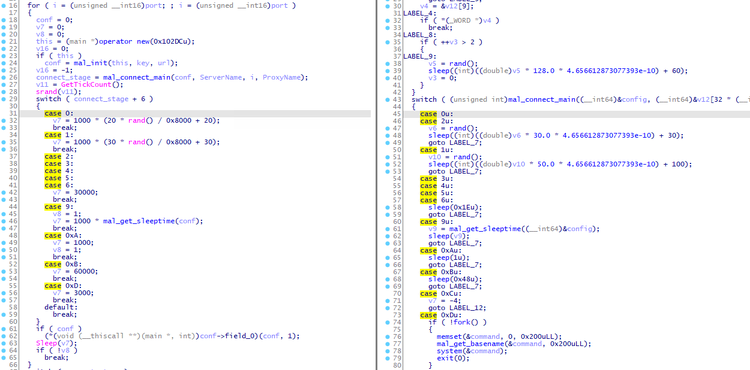
(Left: PLEAD module / Right: ELF_PLEAD)
It is clear from the flow of processing that the two types of malware are quite similar. The next sections will describe the features of ELF_PLEAD from the following perspectives:
- Configuration
- Communication protocol
- Commands
Configuration
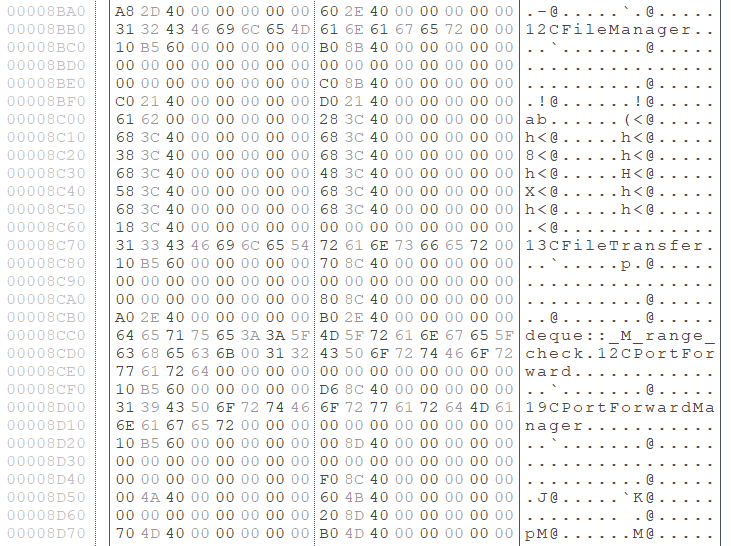
ELF_PLEAD possesses its configuration with the size of 0x1AA. Figure 2 is an example of configuration. It contains information such as C&C servers and an encryption key. (Please see Appendix A for the details of configuration.)

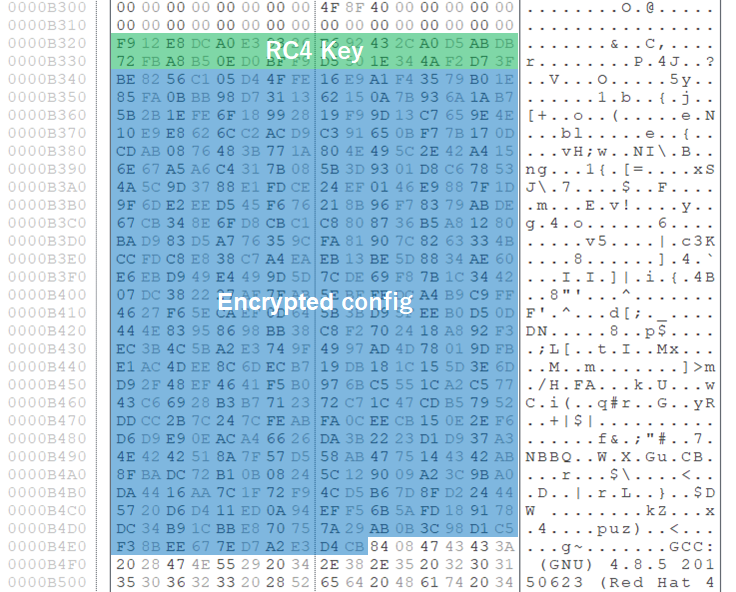
The configuration is RC4-encrypted, and the 32-byte string right before the encrypted configuration is the encryption key itself. Figure 3 is an example of encrypted configuration and its key.
Communication protocol
While PLEAD module uses HTTP protocol to communicate with its C&C servers, ELF_PLEAD uses its custom protocol. Besides the difference, the data format and the method for exchanging the encryption key are almost the same. Figure 4 describes the flow of communication that ELF_PLEAD performs.
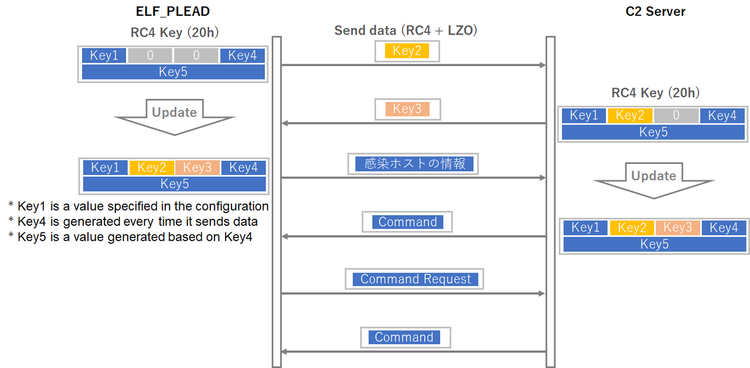
ELF_PLEAD exchanges a part of RC4 key at the time of first communication. After that, a RC4 key generated by the exchange will be used for the communication that follows. The data sent is RC4-encrypted and then LZO-compressed. (Please see Appendix B for the details of communication protocol.)
Commands
ELF_PLEAD is equipped with 5 command groups as follows. (Please see Appendix C for the details of command functions. The command number may vary in some samples.)
- CFileManager (group number 0): commands for operation on files
- CFileTransfer (group number 1): commands for sending/receiving files
- CRemoteShell (group number 2): commands for remote shell
- CPortForwardManager (group number 3): commands for proxy mode
- No name (group number 0xFF): commands for malware control
It is clear that the functions are almost the same as PLEAD module.
In closing
It has been confirmed that BlackTech uses different kinds of malware including TSCookie, PLEAD and KIVARS, which target Linux OS as well as Windows OS. If such malware is found in your Windows environment, it is recommended to check your Linux environment as well.
Shusei Tomonaga
(Translated by Yukako Uchida)
Appendix A: ELF_PLEAD Configuration
| Offset | Description | Remarks |
| 0x000 | RC4 Key | Used for encrypting communication |
| 0x004 | ID | |
| 0x024 | Port number 1 | |
| 0x026 | Port number 2 | |
| 0x028 | Port number 3 | |
| 0x02A | C&C server 1 | |
| 0x0AA | C&C server 2 | |
| 0x12A | C&C server 3 |
- Configuration format may vary in some samples.
Appendix B: Contents of data exchanged
| Offset | Length | Contents |
| 0x00 | 4 | RC4 Key (Key4) |
| 0x04 | 4 | Hash value |
| 0x08 | 4 | RC4 key (Key1) |
| 0x0C | 2 | Length of data sent |
| 0x0E | 2 | Length of data at offset 0x10 before compression |
| 0x10 | - | Encrypted data (RC4 +LZO) (See Table A-2 for details.) |
| Offset | Length | Contents |
| 0x00 | 2 | 0xFF |
| 0x02 | 4 | RC4 key (Key2) |
| 0x06 | - | Random data (at least 128 bytes) |
| Offset | Length | Contents |
| 0x00 | 4 | RC4 key (Key4) |
| 0x04 | 4 | Hash value |
| 0x08 | 4 | RC4 key (Key1) |
| 0x0C | 2 | Length of data sent |
| 0x0E | 2 | Length of data at offset 0x10 before compression |
| 0x10 | - | Encrypted data (RC4 +LZO) (See Table A-4 for details.) |
| Offset | Length | Contents |
| 0x00 | 2 | 0x01FF |
| 0x02 | 4 | RC4 key (Key3) |
Appendix C: ELF_PLEAD commands
| Value | Contents |
| 4 | Send random data |
| 5 | Reconnect |
| 6 | Restart |
| 7 | End |
| 8 | End |
| 9 | Change socket |
| 11 | Change C2 server |
| Value | Contents |
| 32 | Send list of files |
| 37 | Send file size, mode, timestamp |
| 39 | Change file name |
| 41 | Delete file/directory |
| 43 | Upload file |
| 45 | Execute file |
| 49 | Create directory |
| 51 | Move file |
| 53 | Delete directory |
| Value | Contents |
| 64 | Send file/directory information |
| 67 | Create directory |
| 70 | Download file |
| 71 | Send file information |
| 75 | Upload file |
| Value | Contents |
| 80 | Launch remote shell |
| Value | Contents |
| 96 | Set up proxy |
| 100 | Connect proxy |
| 102 | Send proxy data |
| 104 | - |
| 106 | - |
| 108 | End proxy |
Appendix D: C&C server
- mx.msdtc.tw
Appendix E: Malware hash value
- 5b5f8c4611510c11d413cb2bef70867e584f003210968f97e0c54e6d37ba8d8d
- ca0e83440b77eca4d2eda6efd9530b49ffb477f87f36637b5e43f2e428898766