JPCERT/CC released a new version of LogonTracer, a tool to support event log analysis. https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.4.0 This article introduces some of the new features of the tool. Dark mode Dark mode has been added to LogonTracer in this update, which appears on the menu bar. Figure 1 shows the LogonTracer screen when the dark mode is on. Figure 1: LogonTracer (dark mode) Please note that each colour represents the following item...
List of “2020”
-
-
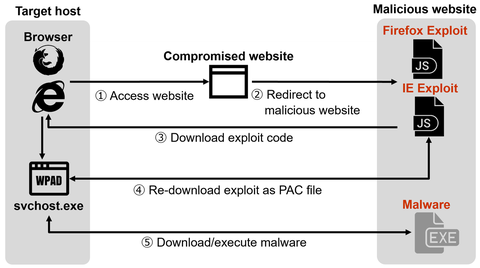
On 8 January 2020, Mozilla released an advisory regarding a vulnerability in Firefox. On 17 January, Microsoft reported that 0-day attacks exploiting a vulnerability in Internet Explorer (IE) had been seen in the wild. JPCERT/CC confirmed attacks exploiting both vulnerabilities at once and issued a security alert. This article explains the details of these attacks. Attack overview In this attack, victims are redirected to an attack site through a compromised...
-
In September 2019, JPCERT/CC published a security alert regarding vulnerabilities in multiple SSL-VPN products. Among the vulnerabilities pointed out in the alert, JPCERT/CC has been notified of cases leveraging CVE-2019-11510 and CVE-2019-11539 in Pulse Connect Secure in attacks against Japanese organisations. This activity seems to continue up until now according to some media reports. As many companies encourage employees to “work from home” in the current situation, use of VPN...
-
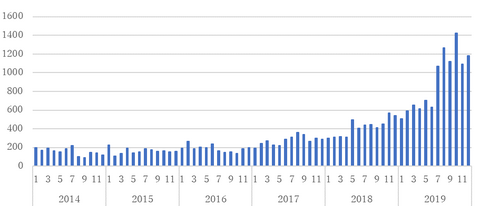
JPCERT/CC receives approximately 19,000 incident reports every year. In 2019, about 56 % of all the reported incidents were categorised as phishing. This time, based on the reported phishing cases, we would like to share the changes in the number of reported cases and trends. For the purpose of this article, the term “phishing site” refers to a website that is disguised as that of an existing brand in an...
-
Following the previous article, we continue with the summary of the second half of the ICS Security Conference 2020 program. The Trend in Standardization of ICS Security System -The Introduction and Updates of IEC 62443- By Junya Fujita (Center for Technology Innovation, Control Platform Research Development, Hitachi, Ltd) Slides (Japanese only) In this presentation, the overview of and the updates on IEC 62443, which is the standard in ICS security,...
-
On February 14, 2020, JPCERT/CC held ICS Security Conference 2020 at Asakusabashi Hulic Hall. This conference aims at improving security measures and best practices of ICS through sharing threat trend against ICS in Japan and the world as well as the latest security activities conducted in related industries and enterprises. 307 people participated in the event this year. This blog entry and the next one introduce the summary of the...
-
In the past blog articles, we have introduced TSCookie, PLEAD and IconDown, which are used by BlackTech. It has been identified that this group also uses several other types of malware. While the malware we have already described infects Windows OS, we have also confirmed that there are TSCookie and PLEAD variants that infect Linux OS. This article describes TSCookie for Linux, used by BlackTech. Difference between TSCookie for Windows...
-
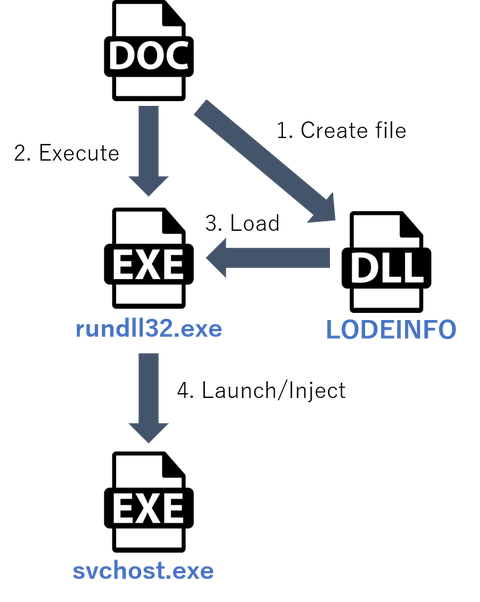
JPCERT/CC has been observing a new type of spear-phishing emails targeting Japanese organisations since December 2019. The emails have a malicious Word file attachment leading to malware “LODEINFO”, which is newly observed. This article introduces the details of this malware. How LODEINFO is launched Figure 1 describes the flow of events from executing a Word file until LODEINFO is launched. Figure 1:Flow of events until LODEINFO runs By enabling the...
-
Following the JSAC Part 1, we continue with the summary of the second ...
-
JPCERT/CC organised Japan Security Analyst Conference 2020 (JSAC2020) on 17 January, 2020 in Ochanomizu, Tokyo. This conference targets front-line security analysts who deal with cyber incidents on a daily basis, with an aim to create a venue for sharing technical information which helps them better handle ever-evolving cyber attacks. This is the third event running annually since 2018, and 301 participants attended this year. In this event, we invited 8...