Multiple Threat Actors Rapidly Exploit React2Shell: A Case Study of Active Compromise
On December 3, 2025 (local time), a vulnerability allowing unauthenticated remote code execution in React Server Components (RSC) (CVE-2025-55182) was disclosed. JPCERT/CC has received multiple incident reports related to this attack. Among them, there was a case in which this vulnerability was exploited by multiple threat actors within a short period of time, resulting in multiple incidents occurring simultaneously, including website defacement. This article demonstrates how rapidly and indiscriminately attackers act when an easily exploitable vulnerability is disclosed, together with an attack timeline and an overview of the malware used. We hope this will serve as a reference for understanding how quickly countermeasures must be implemented when such critical vulnerabilities are made public.
Attack Timeline
Table 1 shows the attack timeline identified in the case. (To avoid revealing the identity of the affected organization, some URL paths and identifiers are masked.)
Date and Time (JST) |
Description |
|---|---|
| 2025-12-05 15:52 | Installation of coin miners (sex.sh, xmrig) |
| 2025-12-06 07:28 | Installation of coin miner (sex.sh.1) |
| 2025-12-06 09:53, 10:09, 11:00 | Installation of HISONIC (javax) backdoor |
| 2025-12-06 15:00 | Execution of Global Socket (npm-cli) hourly via cron |
| 2025-12-06 19:31 | Installation of SNOWLIGHT downloader (javas) and CrossC2 (rsyslo) |
| 2025-12-07 12:24 | Installation of coin miner (xmrig) |
| 2025-12-07 16:51 | Cron configuration modified to execute /tmp/kernal (disguised as kernel) every minute |
| 2025-12-07 19:46 | Website defacement (display of warning message) |
| 2025-12-07 22:15 | Incident discovered following a report from a service user |
Only two days after the React2Shell vulnerability was disclosed on December 3, 2025, attacks aimed at installing coin miners were observed. Following this initial activity, various types of malware such as RATs and backdoors were installed and executed by multiple attackers, resulting in a situation where multiple threat actors had compromised a single server.
In addition to the timeline above, suspicious HTTP POST communications believed to target the React2Shell vulnerability were observed in the web server access logs from more than 100 IP addresses during the period from December 5 to 7, 2025. (Because request headers and POST data were not recorded in the access logs, this assessment was based on factors such as the User-Agent, request path, and response size.) This suggests that the server may actually have been targeted by even more attackers.
Initial Website Defacement
In this case, the compromise was discovered after a website user noticed that the website had been defaced by attackers and reported it. On the defaced website, a warning message was displayed in four languages stating that there was a vulnerability identified as CVE-2025-55182 and that patches needed to be applied immediately. Figure 1 shows an example of a defaced web page.
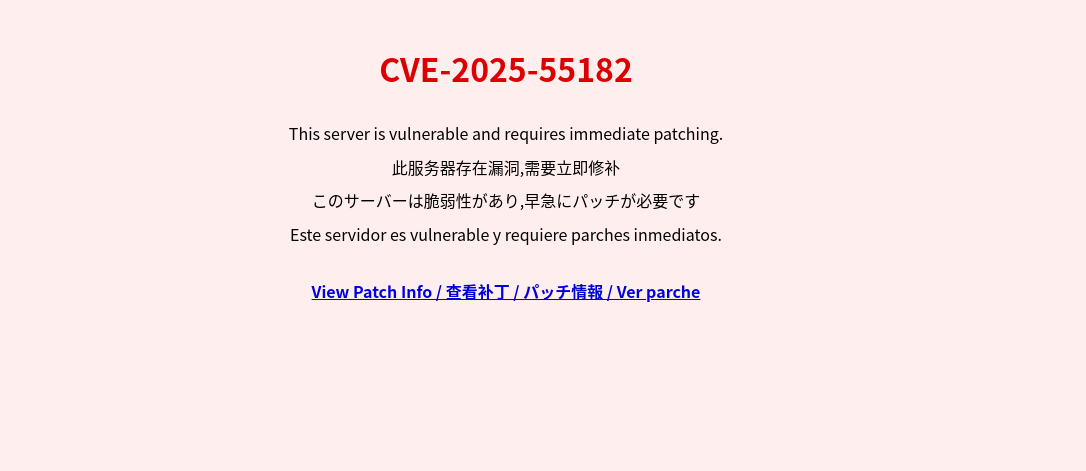
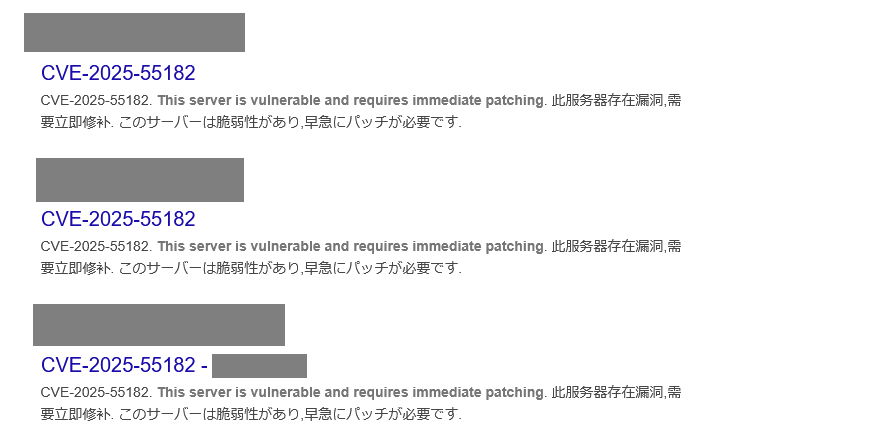
Such defacements were confirmed on multiple websites both in Japan and overseas, all of which contained text urging immediate countermeasures to the vulnerability. Figure 2 shows an example of defaced sites displayed in search engine results.
Installed Malware
In this case, a variety of malware and open-source tools were abused. Table 2 lists the malware that was installed (excluding configuration files and similar artifacts).
No. |
File Name |
Description |
|---|---|---|
| 1 | sex.sh | Bash script for downloading xmrig |
| 2 | sex.sh.1 | Bash script for downloading xmrig |
| 3 | miner.sh | Bash script for launching xmrig |
| 4 | xmrig | xmrig coin miner |
| 5 | javax | HISONIC backdoor |
| 6 | javas | Bash script for downloading SNOWLIGHT |
| 7 | rsyslo | CrossC2 RAT |
| 8 | npm-cli | Global Socket tool |
| 9 | kernal | Details unknown because it had been deleted |
Notably, in addition to typical financially motivated coin miners, the following were also observed: a SNOWLIGHT [1] downloader reportedly used by UNC5174, a Golang-based HISONIC backdoor [2] reportedly used by UNC6603, and CrossC2 RAT [3], the Linux version of the Cobalt Strike implementation, which was installed at the same time as SNOWLIGHT. Although the attackers’ actual objectives remain unclear, it is possible that these tools were intended to be exploited as part of a future attack infrastructure.
Additionally, unlike most cases reported by other security vendors, this incident involved the abuse of the open-source tool Global Socket (gsocket) [4]. This tool enables two devices that cannot directly reach each other due to NAT or firewall restrictions to connect via a relay network called the Global Socket Relay Network (GSRN). A key feature is that only devices sharing the same pre-shared key can communicate with each other. Communications are end-to-end encrypted, and GSRN only relays encrypted traffic.
In this case, the attackers specified the following environment variables and options at execution time, using npm-cli.dat as a secret file and abusing the tool as a backdoor that allowed remote operation via bash over port 53, which is primarily used for DNS communication.
GS_PORT='53' SHELL=/bin/bash TERM=xterm-256color GS_ARGS="-k /home/***/.config/dbus/npm-cli.dat -liqD"
Conclusion
In this React2Shell case, the vulnerability was rapidly incorporated into attack tools after disclosure, and within just a few days it was observed being abused by many threat actors. Attackers exploit vulnerabilities at extremely high speed, and when critical vulnerabilities are disclosed, it is essential to promptly assess the scope of impact and apply patches and other countermeasures.
Furthermore, when addressing vulnerabilities that are known to be actively exploited, it is necessary to verify whether compromise has already occurred in addition to applying patches. As demonstrated in this case, there may be more serious compromises beyond visible website defacement, and so it is recommended to carefully investigate whether there are any other affected components.
Details such as the C2 of the malware covered in this article are provided in the Appendix for reference.
Kota Kino, Yuki Yano (This article was machine-translated and manually reviewed.)
References
[1] SNOWLIGHT Windows malware used by UNC5174
https://sect.iij.ad.jp/blog/2025/11/unc5174-windows-snowlight-in-2025/
[2] Multiple Threat Actors Exploit React2Shell (CVE-2025-55182)
https://cloud.google.com/blog/topics/threat-intelligence/threat-actors-exploit-react2shell-cve-2025-55182
[3] CrossC2 Expanding Cobalt Strike Beacon to Cross-Platform Attacks
https://blogs.jpcert.or.jp/en/2025/08/crossc2.html
[4] Global Socket
https://github.com/hackerschoice/gsocket
Appendix A: C2
No. |
Destination |
Purpose |
|---|---|---|
| 1 | 45.143.131[.]123:59999 | SNOWLIGHT download source / C2 server |
| 2 | 154.89.152[.]240:443 | CrossC2 C2 server |
Appendix B: Malware Hashes
No. |
Hash (SHA-256) |
File Name |
|---|---|---|
| 1 | 5bae25736a09de5f4a0f9761d2b7bfa81ca8dba39de2a724473c9d021a65daa9 | sex.sh |
| 2 | ba43e447e63611d365300bf2e8e43ccb02ea112778d0d555ef9a9ccf6169808b | sex.sh |
| 3 | ac3e12fa0aa4d6e4eed322e81ecf708a8c9bea29247ae6b26cc39d3b3a6c2fb8 | miner.sh |
| 4 | a536d755313ce550a510137211eca6171f636fb316026e9df8523c496c8fcd12 | xmrig |
| 5 | 0c748b9e8bc6b5b4fe989df67655f3301d28ef81617b9cbe8e0f6a19d4f9b657 | xmrig |
| 6 | 1a1edbea47162b1aa844252fcd4fb97f2a67faec1993e7819efc6a04b7c15552 | javax |
| 7 | 0d07a974993221305ca7af139b73d9de1dcd992f553215e4f041e830a2d82729 | javas |
| 8 | 5baa52387daedea5e3e00adf96ecacb4a2cdc98100664f29ac86e8e4a423baaf | 54ad0ee3tcp |
| 9 | c1a9cfc62626118bd9f54e401fd52ecd2d766a5e8a69dbc7db909ea5c987fcc0 | 54ad0ee3tcp |
| 10 | 4a74676bd00250d9b905b95c75c067369e3911cdf3141f947de517f58fc9f85c | rsyslo |
| 11 | cb5f62bf7b591e69bd38e6bf8e40e8d307d154b2935703422d44f02e403d2e78 | npm-cli |

