Hello all, this is Yohei Tanaka from Analysis Center. In this article, I will introduce how recent malware tries to trick users with fake thumbnail previews – I hope this information prevents you from encountering troubles. The majority of malware distributed via email nowadays are executable files (.exe) or compressed executable files, rather than document files that attempt to leverage software vulnerabilities. We at JPCERT/CC have seen cases where users...
-
-
JPCERT/CC has successfully hosted the seventh Control System Security Conference on February 12, 2015 at Kokuyo Hall in Tokyo. The event brought together more than 250 attendees, including a cross-section of engineers/managers of ICS vendors and asset owners. The conference has been held annually since 2009 in order to raise awareness on ICS security issues and share the insights and ideas on ICS security. The program for this year has...
-
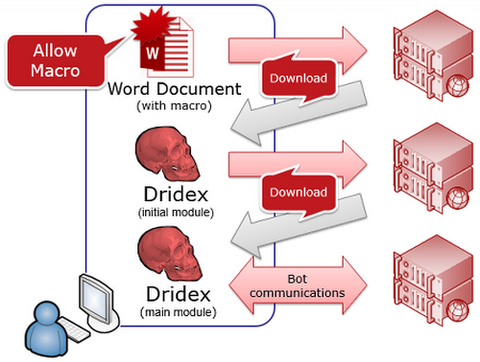
NOTE: This article, originally published on 13 February, 2015, was updated as of 12 May, 2015 (See below). Hello all, this is You Nakatsuru (“TSURU”) from Analysis Center again. Today, I would like to describe a new UAC bypass method that has been used by the Dridex malware since December, 2014. Introduction Dridex is a banking trojan, which is a bot that communicates with a CC server through HTTP. Most...
-
This is Shusei Tomonaga at Analysis Center. PlugX, a Remote Access Tool (RAT) often seen in many APT cases, has been in the wild for some years. Various sectors in Japan have been suffering from this type of attack from 2012, and Analysis Center has been working to catch up on the evolution of the PlugX family since then. In this blog post, I will write about a recent PlugX...
-
Happy New Year 2015 to everyone! I am Toru Yamauchi, Research Director of JPCERT/CC. JPCERT/CC has been contributing to the CSIRT community in Africa in order to enhance the global cybersecurity activity. In the rapid ICT development in Africa, it is getting more important for them to accelerate human development in cybersecurity area and to establish regional cooperation especially among National CSIRTs. I would like to introduce our recent on-site...
-
Happy holidays to all, this is Tetsuya from Watch and Warning Group. Today, I would like to share a recent, remarkable trend discovered through TSUBAME sensors. In TSUBAME, we have observed a significant increase in packets destined to 8080/TCP since December 5th, 2014. When accessing source IP addresses using a web browser, the admin login screen for NAS devices provided by QNAP was seen in many cases for IP addresses...
-
Hello and Happy Holiday Season to everybody. Taki again, and today I will write about some experiences in product (software, hardware) vulnerability coordination this year. - Introduction - A lot happened this year and I do not have the time to go through everything, but would like to go over some of the major issues that we handled and for those that are not familiar, provide a very brief overview...
-
Hello, this is Osamu from Global Coordination Division. It’s been 2 years since I posted the last article here. Today, I am going to share our experience at the event organized in Thailand last month. In late October, ThaiCERT, a member of ETDA (Electronic Transactions Development Agency), and JPCERT/CC organized an event “Malware Analysis Competition 2014 (MAC 2014)” in Bangkok, Thailand. The event consisted of 3 parts: Basic Malware Analysis...
-
Hello, this is Taki and today I would like to write about my trip to Colombo, Sri Lanka from September 30th through October 2nd. I went with Tetsuya to conduct TSUBAME trainings at Sri Lanka CERT|CC and TechCERT, and to give a presentation at Cyber Security Week 2014 - 7th Annual National Conference on Cyber Security. TSUBAME Training for Sri Lanka CERT|CC and TechCERT Unlike our previous TSUBAME trainings in...
-
Hello. This is Masaki from Vulnerability Analysis Team. JPCERT/CC has been active in doing research, developing coding standards and conducting seminars in secure coding since 2007. In the course of our activities, we've collaborated with CSIRTs in Asia-Pacific region such as ThaiCERT, PHCERT, ID-SIRTII/CC, Academic-CERT in Indonesia, VNCERT and CERT-In in providing secure coding training to software developers in each region. Last month, Hiroshi (my teammate and senior vulnerability analyst),...