JPCERT/CC held JSAC2024 on January 25 and 26, 2024. The purpose of this conference is to raise the knowledge and technical level of security analysts, and we aimed to bring them together in one place where they can share technical knowledge related to incident analysis and response. The conference was held for the seventh time and, unlike last year, returned to a completely offline format. 17 presentations, 3 workshops, and...
-
-
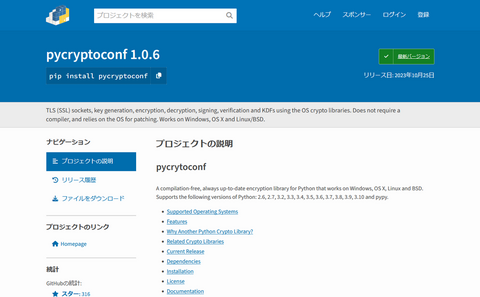
JPCERT/CC has confirmed that Lazarus has released malicious Python packages to PyPI, the official Python package repository (Figure 1). The Python packages confirmed this time are as follows: pycryptoenv pycryptoconf quasarlib swapmempool The package names pycryptoenv and pycryptoconf are similar to pycrypto, which is a Python package used for encryption algorithms in Python. Therefore, the attacker probably prepared the malware-containing malicious packages to target users' typos in installing Python packages....
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of July to September 2023. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here . Suspicious packets sent from routers sold by a Japanese manufacturer Focus on routers sold by a...
-
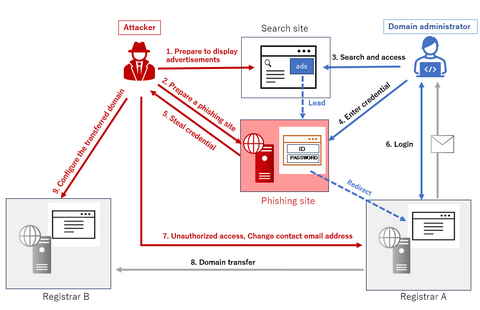
In early July 2023, JPCERT/CC confirmed a case of domain hijacking in which a domain used in Japan was unauthorizedly transferred to another registrar. This blog post describes the attack case. Attack overview Figure 1 shows the attack flow. The attacker first prepared a phishing site, which pretended to be a registrar on search site advertisements. Figure 1: the attack flow An attacker can steal account information and password (hereafter...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of April to June 2023. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Difference of observed packets in Japan and overseas sent from Japan Along with the renewal of the...
-
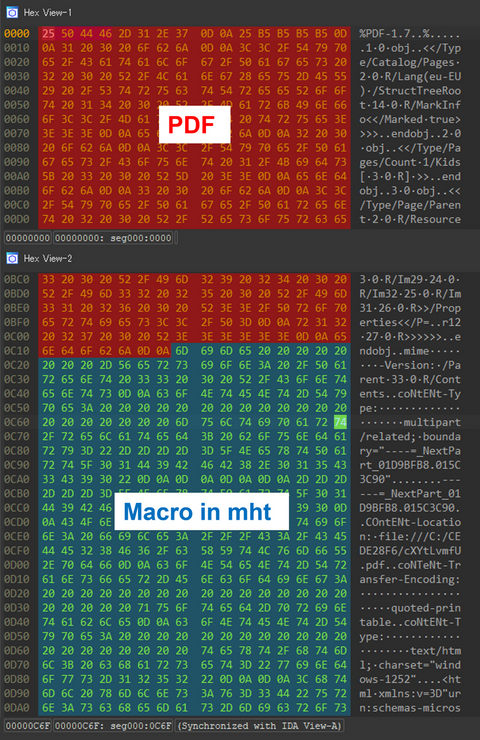
JPCERT/CC has confirmed that a new technique was used in an attack that occurred in July, which bypasses detection by embedding a malicious Word file into a PDF file. This blog article calls the technique “MalDoc in PDF” hereafter and explains the details of and countermeasures against it. Overview of MalDoc in PDF A file created with MalDoc in PDF can be opened in Word even though it has magic...
-
As attacks become more fileless and malware gets more obfuscated, it is getting more difficult to determine whether there is a malicious intent from a file by itself. For this reason, malware detection methods that utilize sandboxes and AI, as well as technologies that detect suspicious behavior after malware infection, such as EDR, have now become common. Even so, malware that antivirus software cannot detect is often found during actual...
-
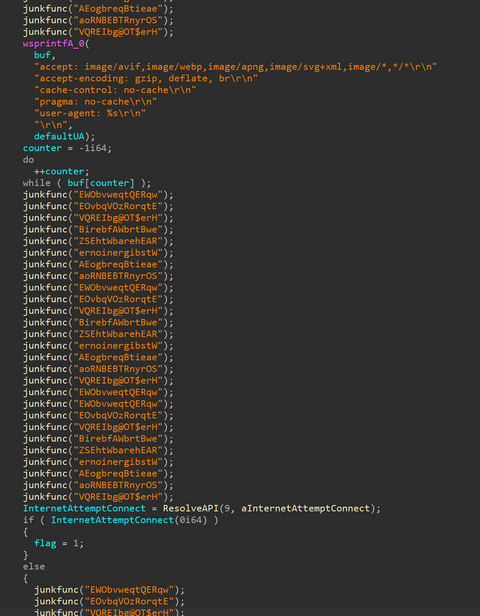
At the end of May 2023, JPCERT/CC confirmed an attack targeting developers of cryptocurrency exchange businesses, and it is considered to be related to the targeted attack group DangerousPassword [1], [2] (a.k.a. CryptoMimic or SnatchCrypto), which has been continuously attacking since June 2019. This attack targeted Windows, macOS, and Linux environments with Python and Node.js installed on the machine. This article explains the attack that JPCERT/CC has confirmed and the...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of January to March 2023. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Observation of suspicious packets sent from a hosting company in Japan From February to March, we observed...
-
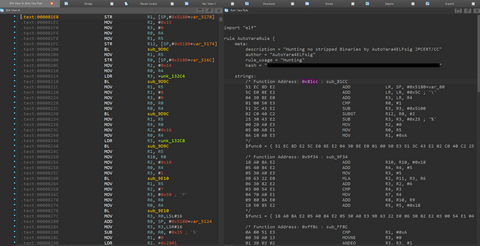
It has been observed that ELF malware removes symbol information during its build. This creates extra work in malware analysis to identify each function name because you do not know them. In addition, in IDA, an analysis tool, existing F.L.I.R.T signatures [1] (hereafter abbreviated as FLIRT signatures in this article) are often not applicable to ELF malware functions, making analysis difficult when right signatures are not found. This blog article...