This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of July to September 2024. Packets from TP-LINK routers other than AX3000 JPCERT/CC analyzes the data collected by TSUBAME every day. In the previous article , we discussed scans from IP addresses that appear to be...
-
-
JPCERT/CC has confirmed an attack against an organization in Japan in ...
-
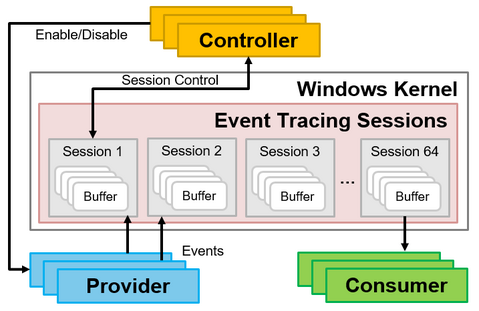
Many people may think of EventLogs when one mentions Windows OS logs. When investigating incidents such as malware infections, it is common to analyze the Windows OS EventLogs to find traces that may help uncover the incident. However, since the EventLog is not designed to detect suspicious behavior on Windows OS, you may not always find the information you are looking for when investigating an incident. Therefore, it is necessary...
-
The difficult part of the initial response to a human-operated ransomware attack is identifying the attack vector. You may already know from recent security incident trends that the vulnerabilities of VPN devices are likely to be exploited, but it often takes much time to investigate because multiple penetration routes are often considered when an incident occurs. Therefore, in order to ensure a smooth initial response, it is important to investigate...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of April to June 2024. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Activities to scan Telnet from TP-LINK routers JPCERT/CC analyzes the data collected by TSUBAME every day. Since...
-
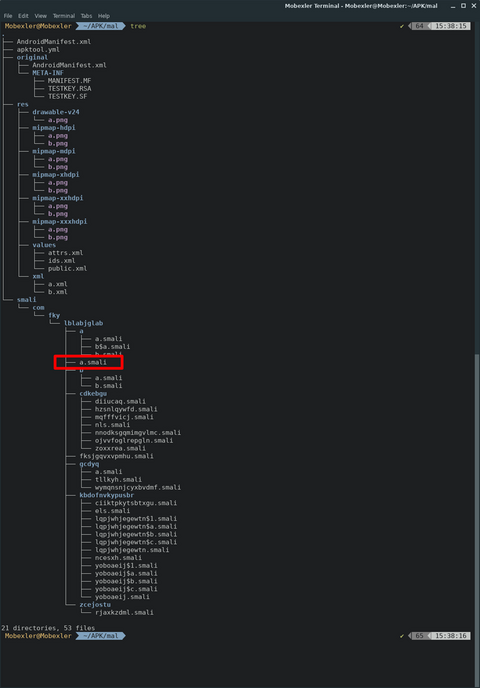
When dynamically analyzing Android malware, it is currently difficult to follow its code using debuggers unlike Windows malware. Although there is a technique [1] to hook a method dynamically by Frida [2], obtaining the in-progress state of the method is still difficult, and since Frida is not a tool dedicated to Android, only limited information can be obtained. In this article, I introduce smali gadget injection technique as a more...
-
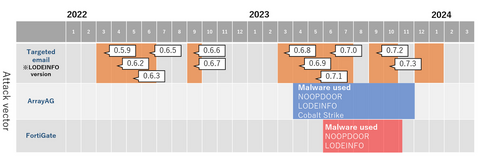
JPCERT/CC has been observing attack activities by MirrorFace LODEINFO ...
-
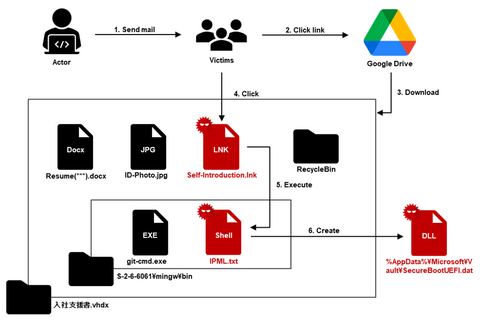
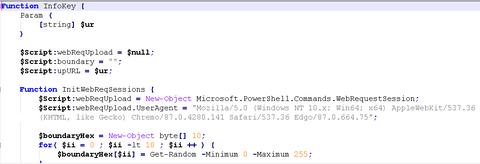
JPCERT/CC has confirmed attack activities targeting Japanese organizations by an attack group called Kimsuky in March 2024. This article introduces the attack methods of the group confirmed by JPCERT/CC. Attack overview In the attack we identified, the attacker sent a targeted attack email impersonating a security and diplomatic organization. A zip file containing the following files with double file extensions was attached to the email. (File names are omitted.) (1)...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of January to March 2024. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Impacts in Japan from Observations in FY2023 JPCERT/CC analyzes the data collected by TSUBAME on a daily...
-
JPCERT/CC held the annual ICS Security Conference 2024 on 7 February 2024. The conference aims to share the current status of threats to ICS both in Japan and overseas and the efforts of stakeholders in the field, as well as to help participants improve their ICS security measures and establish best practices. The conference started in 2009 and is now in its 16th year. This was the 4th time the...