This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of October to December 2024. Observation of reflection packets from Websites of organizations in Japan At JPCERT/CC, we analyze the data collected from TSUBAME on a daily basis. We sometimes observe packets from websites responding to...
-
-
Continuing from the previous blog article, this entry introduces the presentations on the 2nd day of JSAC2025. Observation of phishing criminal groups related to illegal money transfers and Mizuho Bank’s countermeasures -Fighting against phishing site malware ‘KeepSpy’- Speaker: Tsukasa Takeuchi, Takuya Endo, Hiroyuki Yako (Mizuho Financial Group) Slides(English) Tsukasa, Takuya, and Hiroyuki presented Mizuho’s efforts to address phishing attacks, including the analysis of exploited malware and the criminal groups behind...
-
On January 21 and 22, 2025, JPCERT/CC held its annual technical conference JSAC, aiming at enhancing the skills and knowledge of security analysts. The conference brought experts in the field of cyber security together to share technical insights related to incident analysis and response. The event marked its 8th year, and it was held as an offline-only event like the previous year. Over the two-day event, there were 18 presentations,...
-
In January 2025, Ivanti published an advisory[1] regarding the vulnera...
-
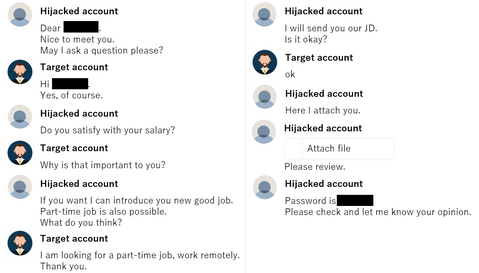
There have recently been reports of unauthorized access in Japan, usin...
-
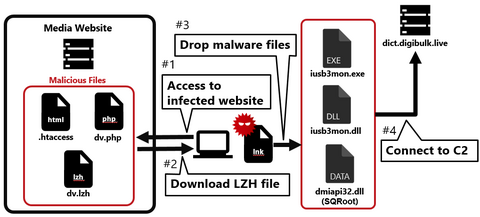
Continuing from the previous article, Part 2 covers another case of a watering hole attack. This time, we will look at the case of a media-related website exploited in 2023. Flow of the attack Figure 1 shows the flow of the watering hole attack. When someone accesses the tampered website, an LZH file is downloaded, and when they execute the LNK file in the LZH file, their PC becomes infected...
-
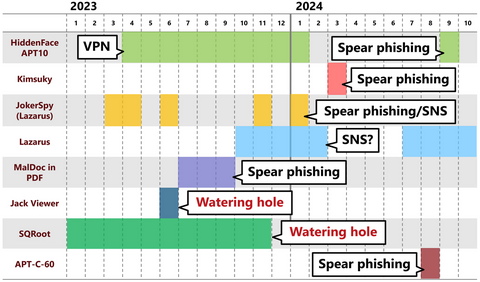
Nowadays, many people probably recognize exploit of vulnerabilities in publicly exposed assets such as VPN and firewalls as the attack vector. In fact, many security incidents reported to JPCERT/CC also involve such devices. This is because vulnerabilities in VPN devices are exploited not only by APT groups but also by many other groups such as ransomware actors and cyber crime actors, and the number of incidents is high accordingly. As...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of July to September 2024. Packets from TP-LINK routers other than AX3000 JPCERT/CC analyzes the data collected by TSUBAME every day. In the previous article , we discussed scans from IP addresses that appear to be...
-
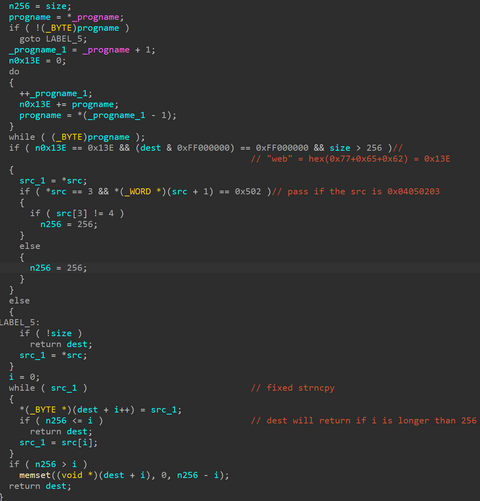
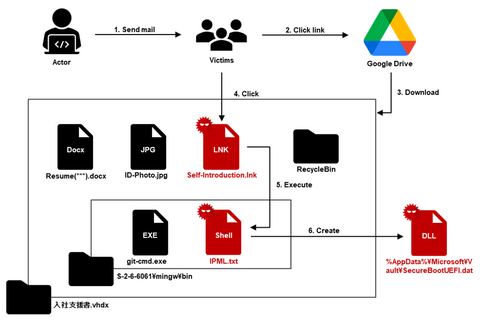
JPCERT/CC has confirmed an attack against an organization in Japan in ...
-
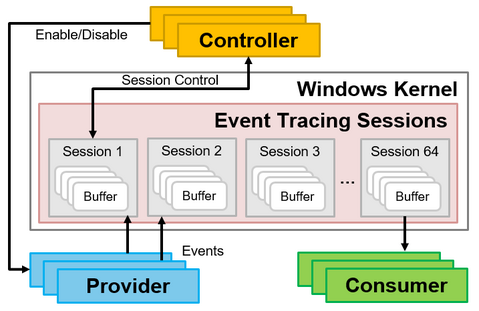
Many people may think of EventLogs when one mentions Windows OS logs. When investigating incidents such as malware infections, it is common to analyze the Windows OS EventLogs to find traces that may help uncover the incident. However, since the EventLog is not designed to detect suspicious behavior on Windows OS, you may not always find the information you are looking for when investigating an incident. Therefore, it is necessary...