This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of October to December 2023. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here . Packets observed from products under development JPCERT/CC analyzes the data collected by TSUBAME on a daily...
List of “Tags”
-
-
JPCERT/CC releases a URL dataset of phishing sites confirmed from January 2019 to June 2022, as we received many requests for more specific information after publishing a blog article on trends of phishing sites and compromised domains in 2021. The list is available in the following GitHub repository. Phishing URL dataset from JPCERT/CC https://github.com/JPCERTCC/phishurl-list/ Each column contains the following: date: Date confirmed by JPCERT/CC URL: Entire URL of a phishing...
-
Hello. I am Noriko Totsuka from Early Warning Group. The Early Warning Group publishes security information such as security alerts and early warning information, as well as JVN Advisories. As a vulnerability coordinator, I am in charge of a series of coordination tasks, from coordinating with developers of target products, including taking countermeasures based on the vulnerability-related information reported to JPCERT/CC by vulnerability finders such as security researchers, to the...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of October to December 2021. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Looking back on 2021 Figure 1 shows a comparison and transition of the total number of IP...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of January to March 2022. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Scan packets to GRE increased Table 1 shows the top 5 packets sent from IP addresses in...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports do not cover. This article covers the monitoring results for the period of July to September 2021. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Scan packets from Russia increased From Russia, there were accesses to a variety of ports, including port...
-
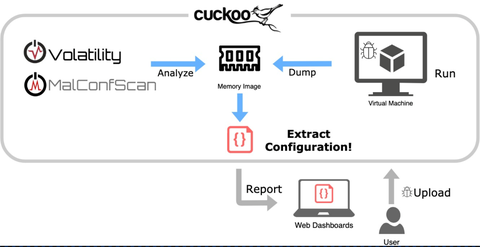
In malware analysis, extracting the configuration is an important step. Malware configuration contains various types of information which provides a lot of clues in incident handling, for example communication details with other hosts and techniques to perpetuates itself. This time, we will introduce a plugin “MalConfScan with Cuckoo” that automatically extracts malware configuration using MalConfScan (See the previous article) and Cuckoo Sandbox (hereafter “Cuckoo”). This plugin is available on GitHub....
-
Nice to see you! My name is Jimmy, Hajime Komaba, working at Enterprise Support Group of JPCERT/CC, a department which takes care of Nippon CSIRT Association (NCA), a community of various enterprise and organizational CSIRTs in Japan) and Council of Anti-Phishing Japan (APC). It’s been quite a while ago, but last November, I was given an opportunity to travel to the Republic of Congo with my colleague, Koichiro (Sparky) Komiyama....
-
You may well have heard of the May cyber attack in Japan against the Japan Pension Service – a high-profile case seen in the first half of this year, where 1.25 million cases of personal data was exposed. According to the Japan Pension Service, the data leaked included names and ID numbers, and for some cases, dates of birth and home addresses. The official reports(1) say that the massive leak...



.png)