A shortcut file, also referred to as a shell link, is a system to launch applications or to allow linking among applications such as OLE. As we introduced in a previous blog post “Asruex: Malware Infecting through Shortcut Files”, shortcut flies are often used as a means to spread malware infection. Generally, shortcut files contain various types of information including the dates and environment that the shortcut file was created....
List of “Malware”
-
-
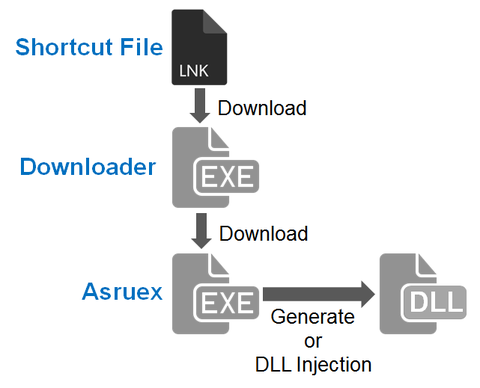
JPCERT/CC has been observing malicious shortcut files that are sent as email attachments to a limited range of organisations since around October 2015. When this shortcut file is opened, the host will be infected with malware called “Asruex”. The malware has a remote controlling function, and attackers sending these emails seem to attempt intruding into the targets’ network using the malware. According to a blog article by Microsoft, the malware...
-
Hello all, this is Shusei Tomonaga again. Generally speaking, malware analysis begins with classifying whether it is known malware or not. In order to make comparison with the enormous number of known malware samples in the database in a speedy manner, hash values are used, derived by performing hash functions to the malware sample. Among the different hash functions, traditional ones such as MD5 and SHA1 derive totally different hash...
-
From the latter half of 2015 to 2016, there have been an increasing number of cyber attacks worldwide using Adwind, a Remote Access Tool [1]. JPCERT/CC also received incident reports about emails with this malware in its attachment. Adwind is malware written in Java language, and it operates in Windows and other OS as well. It has a variety of functions: to download and execute arbitrary files, send infected machine...
-
Hello again, this is You ‘Tsuru’ Nakatsuru from Analysis Center. It has been just about two years since I delivered a talk “Fight Against Citadel in Japan” at CODE BLUE 2013 (an international security conference in Tokyo) about the situation on banking trojans observed in Japan at that time and detailed analysis results on Citadel (See my blog entry here). For the presentation material and audio archive, please see Reference...
-
Hello, this is You ‘Tsuru’ Nakatsuru at Analysis Center. As introduced in the previous blog post, my colleagues presented on the attacks arising in Japan at CODE BLUE 2015, entitled “Revealing the Attack Operations Targeting Japan”. In this entry, I will introduce the details of an IDAPython script “emdivi_string_decryptor.py”, which JPCERT/CC developed to analyse Emdivi, a remote control malware. The script was also introduced in our presentation at CODE BLUE...
-
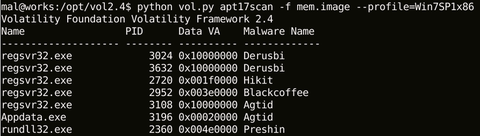
Hello again – this is Shusei Tomonaga from Analysis Center. This blog entry is to introduce “apt17scan.py” created by JPCERT/CC to detect certain malware used in targeted attacks, and to extract its configuration information. It is a plugin for the Volatility Framework (hereinafter “Volatility”), a memory forensics tool. My colleague Yuu Nakamura and I had the honour to introduce this at CODE BLUE 2015, an international conference for information security...
-
Hi, it’s Shusei Tomonaga again from the Analysis Center. PoisonIvy, a Remote Access Tool/Trojan (RAT) often used in targeted attacks, had been widely seen until around 2013. Since then, the number of cases using PoisonIvy in such attacks decreased, and there was no special variant with expanded features seen in the wild. However, recently, we have observed cases where PoisonIvy with expanded features in its communication function were used for...
-
Hello all, this is Yohei Tanaka from Analysis Center. In this article, I will introduce how recent malware tries to trick users with fake thumbnail previews – I hope this information prevents you from encountering troubles. The majority of malware distributed via email nowadays are executable files (.exe) or compressed executable files, rather than document files that attempt to leverage software vulnerabilities. We at JPCERT/CC have seen cases where users...
-
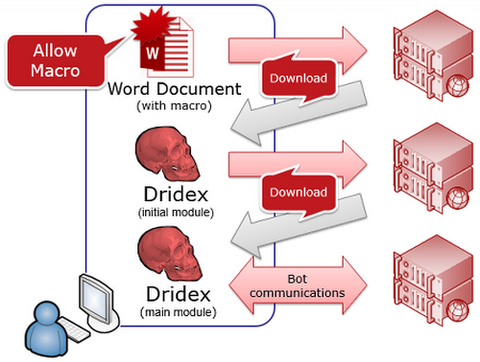
NOTE: This article, originally published on 13 February, 2015, was updated as of 12 May, 2015 (See below). Hello all, this is You Nakatsuru (“TSURU”) from Analysis Center again. Today, I would like to describe a new UAC bypass method that has been used by the Dridex malware since December, 2014. Introduction Dridex is a banking trojan, which is a bot that communicates with a CC server through HTTP. Most...