Today on December 4, 2020, announcements regarding new CNAs (CVE Numbering Authority) were made from The MITRE Corporation and 2 vendors in Japan.The MITRE CorporationLINE Added as CVE Numbering Authority (CNA)Mitsubishi Electric Added as CVE Numbering Authority (CNA)LINE CorporationLINE becomes a CVE Numbering Authority (CNA)Mitsubishi Electric CorporationInitiatives Regarding Product Security|MITSUBISHI ELECTRIC Global websiteFollowing the announcements, I will speak on CVE (Common Vulnerabilities and Exposures) and our activities related to it.CNAs'...
-
-
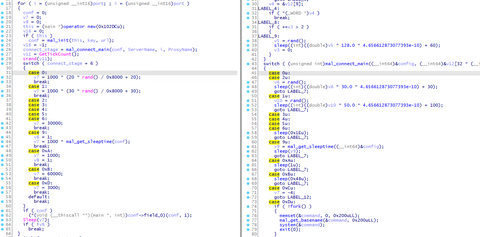
In a past article, we introduced Linux malware ELF_TSCookie, which is used by an attack group BlackTech. This group also uses other kinds of malware that affects Linux OS. PLEAD module for Windows which we introduced before has its Linux version (ELF_PLEAD) as well. This article describe the details of ELF_PLEAD in comparison to PLEAD module. Comparison between PLEAD Module and ELF_PLEAD ELF_PLEAD and PLEAD module share many parts of...
-
JPCERT/CC has released LogonTracer v1.5, the latest version of the event log analysis tool. While this tool was initially focused on post-incident investigation, we have received many requests for updates for the purpose of real-time log analysis. This time, we made some updates to enable such functions. This article will introduce the details of the update. Further information can be found at the following page: https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.5.0 Support for Elasticsearch LogonTracer...
-
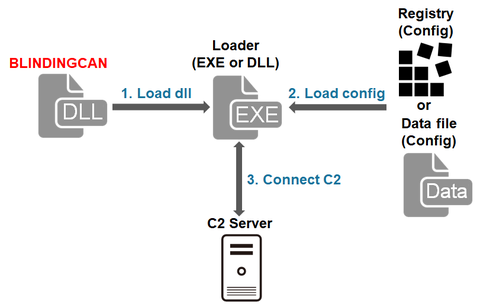
In the previous article, we introduced one type of malware that Lazarus (also known as Hidden Cobra) uses after network intrusion. It is confirmed that this attack group uses multiple types of malware including BLINDINGCAN, which CISA recently introduced in its report [1]. This article summarises the result of our analysis on BLINDINGCAN. BLINDINGCAN overview The malware runs when a loader loads a DLL file. Figure 1 shows the flow...
-
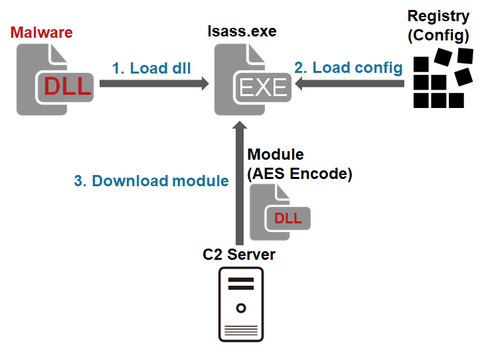
JPCERT/CC has observed attack activity by Lazarus (also known as Hidden Cobra) targeting Japanese organisations. Different types of malware are used during and after the intrusion. This article introduces one of the types of malware used after the intrusion. Malware Overview This malware downloads and executes modules. It is saved as a .drv file in a folder such as C:¥Windows¥System32¥ and run as a service. It is obfuscated by using...
-
The Volatility Foundation released Volatility 3 Public Beta, a new version of Volatility Framework in October 2019. The version not only offers compatibility with Python 3 but also has a lot of functional updates from Volatility 2. (Please see Volatility 3's official page for more details.) Particularly, creating plugins is much easier with Volatility 3 compared to the previous version. Volatility 3’s official release is planned for August 2020, and...
-
We introduced malware LODEINFO in a past blog entry. Attacks using the malware have been continuously seen, in particular with malicious file names including those related to COVID-19. It is also confirmed that LODEINFO has been updated frequently, and several functions have been added or changed in the latest version. This article will introduce trends seen in the series of attacks and updates to the malware. LODEINFO distribution Cases that...
-
Many events in the world have been postponed or cancelled due to COVID-19 pandemic, and cyber security conferences are not the exception. While I hope events will soon be organised as in the past, I would like to introduce three cyber security conferences I recommend you to join when the current situation gets back to normal. Let me tell you first that, since I am a malware analyst, the conferences...
-
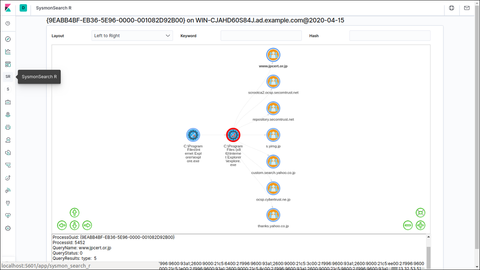
SysmonSearch is a tool developed by JPCERT/CC to analyse event logs generated on Sysmon (a Microsoft tool). https://github.com/JPCERTCC/SysmonSearch SysmonSearch is now compatible with Elastic Stack 7.x. Please note that the new version no longer supports Elastic Stack 6.x versions. This article introduces the new version of SysmonSearch, changes from the previous versions and new functions. Elastic Stack updates Kibana There was a change in Kibana plug-in due to the updates...
-
JPCERT/CC released a new version of LogonTracer, a tool to support event log analysis. https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.4.0 This article introduces some of the new features of the tool. Dark mode Dark mode has been added to LogonTracer in this update, which appears on the menu bar. Figure 1 shows the LogonTracer screen when the dark mode is on. Figure 1: LogonTracer (dark mode) Please note that each colour represents the following item...