JPCERT/CC held the ICS Security Conference on 12 February (Japanese website). This annual conference started in 2009 in the hope of developing security measures and the best practices for ICS. Since then, the conference has been facilitating the exchange of up-to-date knowledge on both domestic and worldwide threats against ICS and the latest security practices in the related industries. In its 13 years of history, this year was the first...
-
-
The attack group Lazarus (also known as Hidden Cobra) conducts various attack operations. This article introduces malware (VSingle and ValeforBeta) and tools used in attacks against Japanese organisations. VSingle overview VSingle is a HTTP bot which executes arbitrary code from a remote network. It also downloads and executes plugins. Once launched, this malware runs Explorer and executes its main code through DLL injection. (Some samples do not perform DLL injection.)...
-
This blog post focuses on the 1st track of JSAC2021, following the previous reports on the 2nd and 3rd track.Opening Talk: Looking Back on the Incidents in 2020Speaker: Takayoshi Shiigi (JPCERT/CC)Slides (English)VideoTakayoshi opened the JSAC2021 with an overview of incidents that JPCERT/CC confirmed in 2020, focusing on targeted attack and widespread attack.Targeted attack in 2020 is characterised by leveraging cloud services for malware operation in multiple stages of attacks from...
-
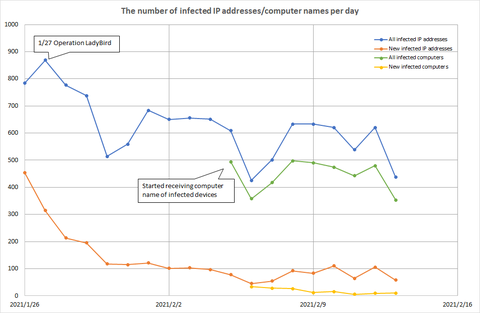
Since October 2019, many cases of Emotet infection were reported. JPCERT/CC has published a security alert and a blog article detailing the detection and security measures, as well as providing notification and support for affected users. Europol announced that Emotet infrastructure was disrupted thanks to the joint operation together with some foreign authorities in January 2021 and information regarding affected users is to be distributed via the CERT network. In...
-
This blog post focuses on the 2nd track of JSAC2021, following the previous report on the 3rd track.Workshop: Malware Analysis at Scale - Defeating EMOTET by Ghidra -Speaker: Shota Nakajima (Cyber Defense Institute), Hiroaki Hara (Trend Micro)Slides (Japanese)VideoShota and Hiroaki presented how malware analysis can be easily done using Ghidra, an open source reverse engineering tool, and the participants tried automating the analysis of Emotet during the hands-on training.Ghidra provides...
-
JPCERT/CC held Japan Security Analyst Conference 2021 (JSAC2021) on 28 January 2021. It was the first JSAC held online in consideration of the participants’ health and safety in the current COVID-19 pandemic.The conference is aimed at providing opportunities for them to get together and exchange their technical knowledge on incident response and analysis. This is JPCERT/CC’s 4th time holding this annual conference, and 11 presenters were selected from 22 candidates.To...
-
The functions and evolution of malware LODEINFO have been described in our past articles in February 2020 and June 2020. Yet in 2021, JPCERT/CC continues to observe activities related to this malware. Its functions have been expanding with some new commands implemented or actually used in attacks. This article introduces the details of the updated functions and recent attack trends. LODEINFO versions At the time of the last blog update,...
-
Lazarus (also known as Hidden Cobra) is known to use various kinds of malware in its attack operations, and we have introduced some of them in our past articles. In this article, we present two more; Torisma and LCPDot. Torisma overview Torisma downloads and executes modules from external servers, and its infection spreads via malicious Word files [1]. Torisma samples that JPCERT/CC has analysed are DLL files and executed as...
-
It is widely known that attackers use Windows commands and tools that are commonly known and used after intruding their target network. Lazarus attack group, a.k.a. Hidden Cobra, also uses such tools to collect information and spread the infection. This blog post describes the tools they use. Lateral movement These three tools are used for lateral movement. AdFind collects the information of clients and users from Active Directory. It has...
-
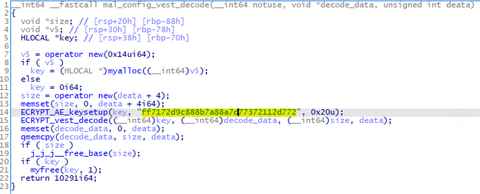
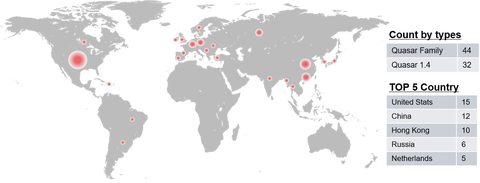
Quasar [1] is an open source RAT (Remote Administration Tool) with a variety of functions. This is easy to use and therefore exploited by several APT actors. JPCERT/CC has confirmed that a group called APT10 used this tool in some targeted attacks against Japanese organisations. As Quasar’s source code is publicly available, there are many variants of this RAT seen in the wild (referred to as “Quasar Family” hereafter). Some...