Many people may think of EventLogs when one mentions Windows OS logs. When investigating incidents such as malware infections, it is common to analyze the Windows OS EventLogs to find traces that may help uncover the incident. However, since the EventLog is not designed to detect suspicious behavior on Windows OS, you may not always find the information you are looking for when investigating an incident. Therefore, it is necessary...
List of “Forensic”
-
-
JPCERT/CC released the latest version (v1.6) of LogonTracer, a tool to support event log analysis. Previously, LogonTracer could not investigate multiple incidents simultaneously, but this update adds support for managing multiple logs. In addition, Sigma can now be used to investigate the presence of suspicious logs in the event log. This article introduces these updates. For other updated items, please refer to the following release: https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.6.0 Log Management Feature When...
-
Volatility 3 had long been a beta version, but finally its v.1.0.0 was released in February 2021. Since Volatility 2 is no longer supported [1], analysts who used Volatility 2 for memory image forensics should be using Volatility 3 already. In this blog post, I introduce a tip for Volatility 3: how to use Volatility 3 offline. This instruction focuses on analyzing Windows OS memory image. What is the problem...
-
JPCERT/CC has released LogonTracer v1.5, the latest version of the event log analysis tool. While this tool was initially focused on post-incident investigation, we have received many requests for updates for the purpose of real-time log analysis. This time, we made some updates to enable such functions. This article will introduce the details of the update. Further information can be found at the following page: https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.5.0 Support for Elasticsearch LogonTracer...
-
JPCERT/CC released a new version of LogonTracer, a tool to support event log analysis. https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.4.0 This article introduces some of the new features of the tool. Dark mode Dark mode has been added to LogonTracer in this update, which appears on the menu bar. Figure 1 shows the LogonTracer screen when the dark mode is on. Figure 1: LogonTracer (dark mode) Please note that each colour represents the following item...
-
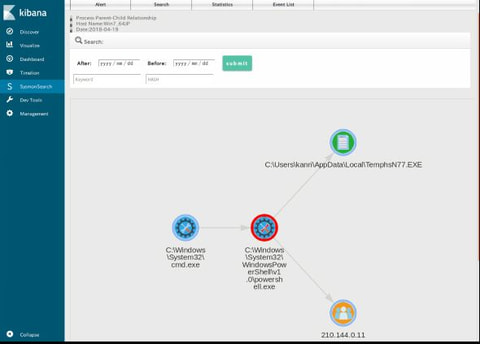
In a past article in September 2018, we introduced a Sysmon log analysis tool "SysmonSearch" and its functions. Today, we will demonstrate how this tool can be used for incident investigation by showing some examples. To install SysmonSearch, please see the following page: JPCERTCC GitHub · SysmonSearch Wiki https://github.com/JPCERTCC/SysmonSearch/wiki The case study was conducted in the following environment: Sysmon 7.0.1 ElasticSearch 6.2.2 Kibana 6.2.2 Winlogbeat 6.2.2 Browser: Firefox Example of...
-
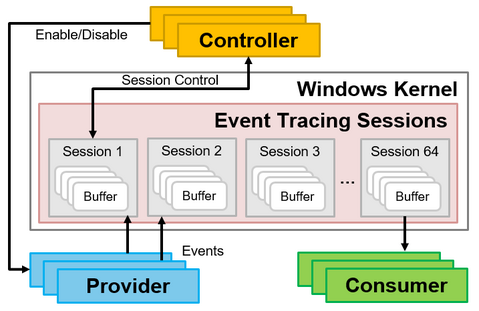
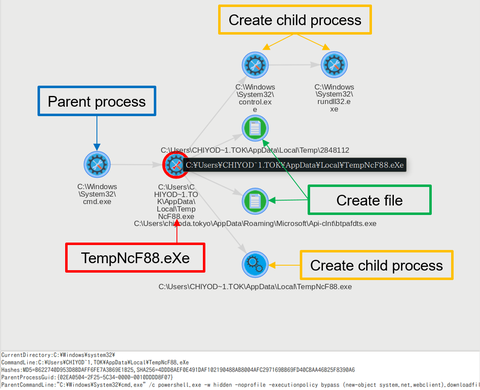
In recent sophisticated cyber attacks, it is common to observe lateral movement, where a malware- infected device is used as a stepping stone and further compromise other devices in the network. In order to investigate the compromised devices, it is necessary to retain detailed logs of the applications that run on the device on a daily basis. One of the well-known tools for this purpose is Sysmon [1] from Microsoft,...
-
In the recent article, we introduced the concept and the use of "LogonTracer", a tool to support Windows event log analysis. This article presents how unauthorised logon attempts can be identified using this tool. Please refer to the Wiki for LogonTracer installation. Points for Investigation LogonTracer serves as a tool to support the log analysis rather than to detect unauthorised logon itself. For an effective investigation using this tool, we...
-
In June 2017, JPCERT/CC released a report “Detecting Lateral Movement through Tracking Event Logs” on tools and commands that are likely used by attackers in lateral movement, and traces that are left on Windows OS as a result of such tool/command execution. After the release, we received a lot of feedback on the report, and until now we had been working on the revision based on the comments. Today, we...
-
Hello again, this is Shusei Tomonaga from the Analysis Center. Event log analysis is a key element in security incident investigation. If a network is managed by Active Directory (hereafter, AD), can be identified by analysing AD event logs. For such investigation, it is quite difficult to conduct detailed analysis in AD event viewer; it is rather common to export the logs to text format or import them into SIEM/log...