Continuing from the previous report, this second installment introduce...
-
-
JPCERT/CC hosted JSAC2026 from January 21 to 23, 2026. JSAC is an annual conference dedicated to advancing the capabilities of security analysts by fostering the exchange of technical knowledge and operational insights related to incident analysis and response. Now in its ninth year, the event incorporated a new training program, expanding the program to three days. Across two days, the conference featured 17 presentations, three workshops, and six lightning talks....
-
On December 3, 2025 (local time), a vulnerability allowing unauthenticated remote code execution in React Server Components (RSC) (CVE-2025-55182) was disclosed. JPCERT/CC has received multiple incident reports related to this attack. Among them, there was a case in which this vulnerability was exploited by multiple threat actors within a short period of time, resulting in multiple incidents occurring simultaneously, including website defacement. This article demonstrates how rapidly and indiscriminately attackers...
-
In recent years, fileless malware and obfuscation techniques have made it increasingly difficult to detect suspicious activity by scanning files alone. To counter these threats, security researchers and malware analysts actively create and publish detection rules such as Sigma and YARA. However, many existing endpoint security tools rely on unique detection engines, instead of directly using Sigma or YARA. To address this problem, JPCERT/CC released the open-source threat hunting tool...
-
In JPCERT/CC Eyes, we previously reported on attacks conducted by Atta...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports do not include. This article covers the monitoring results for the period April to June 2025. Fluctuations in packets from Iran, potentially linked to Israel-Iran military conflict Between June 13 and around June 25, 2025, military conflict occurred between Israel and Iran. During this period, fluctuations were observed...
-
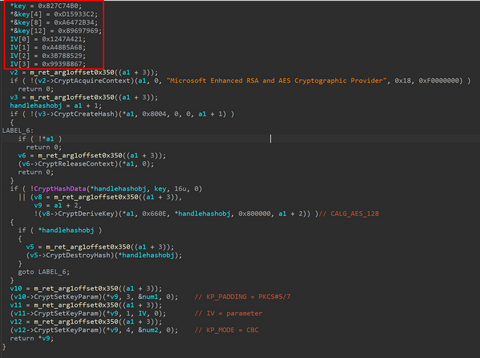
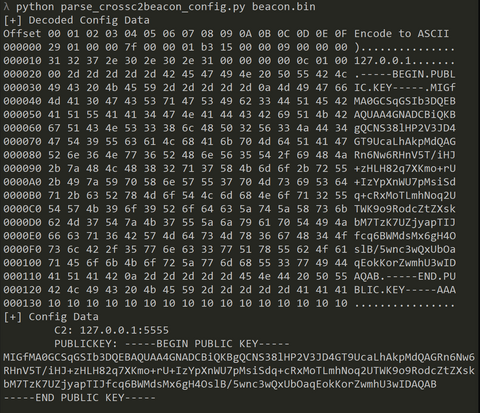
From September to December 2024, JPCERT/CC has confirmed incidents involving CrossC2, the extension tool to create Cobalt Strike Beacon for Linux OS. The attacker employed CrossC2 as well as other tools such as PsExec, Plink, and Cobalt Strike in attempts to penetrate AD. Further investigation revealed that the attacker used custom malware (hereafter referred to as "ReadNimeLoader") as a loader for Cobalt Strike. Information submitted to VirusTotal suggests that this...
-
JPCERT/CC Eyes previously introduced the malware SPAWNCHIMERA and Dslo...
-
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports do not include. This article covers the monitoring results for the period January to March 2025. Trends of Fiscal Year 2024 in Japan At JPCERT/CC, we analyze the data collected from TSUBAME on a daily basis. This time, we would like to focus on incident cases related to...
-
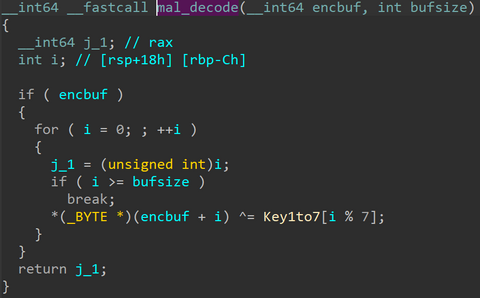
In a previous article of JPCERT/CC Eyes, we reported on SPAWNCHIMERA malware, which infects the target after exploiting the vulnerability in Ivanti Connect Secure. However, this is not the only malware observed in recent attacks. This time, we focus on another malware DslogdRAT and a web shell that were installed by exploiting a zero-day vulnerability at that time, CVE-2025-0282, during attacks against organizations in Japan around December 2024. Functionality of...