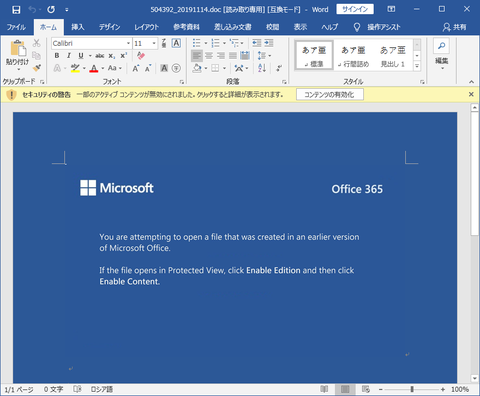
Since October 2019, there has been a growing number of Emotet infection cases in Japan. JPCERT/CC issued a security alert as follows: Alert Regarding Emotet Malware Infectionhttps://www.jpcert.or.jp/english/at/2019/at190044.html The purpose of this entry is to provide instructions on how to check if you are infected with Emotet and what you can do in case of infection (based on the information available as of December 2019). If you are not familiar with...
-
-
Hello, I am Takumi from Global Coordination Division.I joined 2019 FIRST Regional Symposium – Small Island Developing States, which took place in Nadi, Fiji from the 5th through the 7th of November. Today, I am briefly sharing my experience at the event. 2019 FIRST Regional Symposium – Small Island Developing Stateshttps://www.first.org/events/symposium/nadi2019/ 2019 FIRST Regional Symposium – Small Island Developing States Organized by FIRST and supported by the Department of Foreign...
-
In the past articles, we have introduced TSCookie and PLEAD, the malware used by an attack group BlackTech. We have confirmed that this group also uses another type of malware called “IconDown”. According to ESET’s blog[1], it has been confirmed that the malware is distributed through the update function of ASUS WebStorage. This article describes the details of IconDown found in Japanese organisations. IconDown’s behaviour The malware downloads a file...
-
Hi, this is Yuka again from Global Coordination Division. We came back from Singapore after APCERT AGM Conference (held on 29 Sep – 2 Oct 2019), which was a great success. Today I am giving you some updates about the event. APCERT Annual General Meeting Conference 2019https://www.apcert2019.sg/ APCERT AGM Conference 2019 This is literally the biggest and most important event for APCERT community in a year. This time, it was...
-
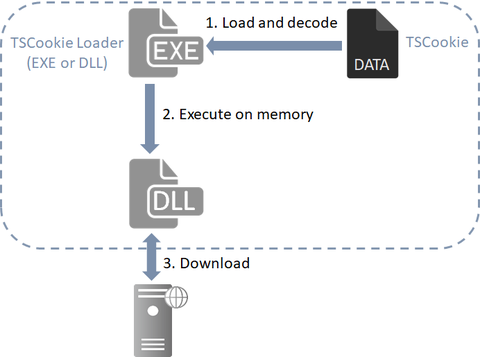
Previously, we explained about malware "TSCookie" and "PLEAD" which are used by an attack group BlackTech. Their activities have been continuously observed in Japan as of now. We have been seeing that a new malware variant is being used after they successfully intruded into a target network. This article explains the details of the variant. TSCookie used after intrusion The malware consists of 2 files (TSCookie Loader and TSCookie) as...
-
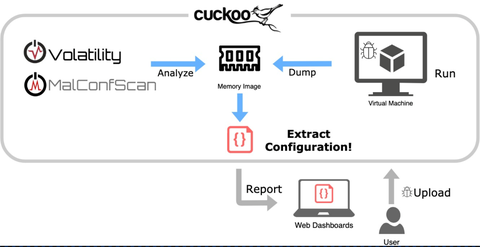
In malware analysis, extracting the configuration is an important step. Malware configuration contains various types of information which provides a lot of clues in incident handling, for example communication details with other hosts and techniques to perpetuates itself. This time, we will introduce a plugin “MalConfScan with Cuckoo” that automatically extracts malware configuration using MalConfScan (See the previous article) and Cuckoo Sandbox (hereafter “Cuckoo”). This plugin is available on GitHub....
-
Every day, new types of malware are discovered. However, many of them are actually variants of existing malware - they share most part of the code and there is a slight difference in configuration such as CC servers. This indicates that malware analysis is almost complete as long as the configuration is extracted from malware. In this article, we would like to introduce details of “MalConfScan”, a tool to extract...
-
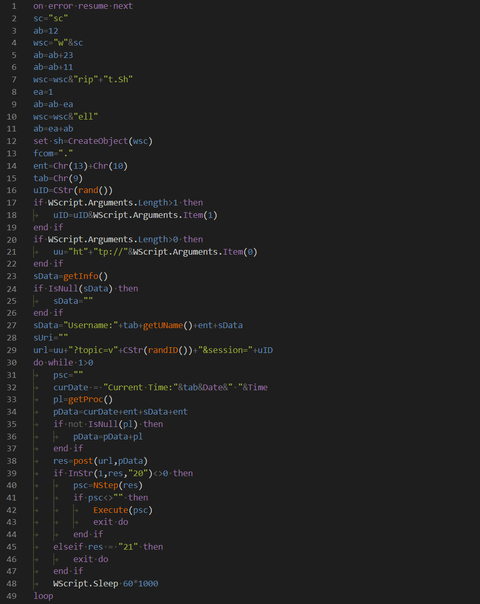
As of June 2019, JPCERT/CC has observed targeted emails to some Japanese organisations. These emails contain a URL to a cloud service and convince recipients to download a zip file which contains a malicious shortcut file. This article will describe the details of the attack method. How the VBScript downloader is launched The zip file downloaded from the URL in the email contains a password-protected decoy document and a shortcut...
-
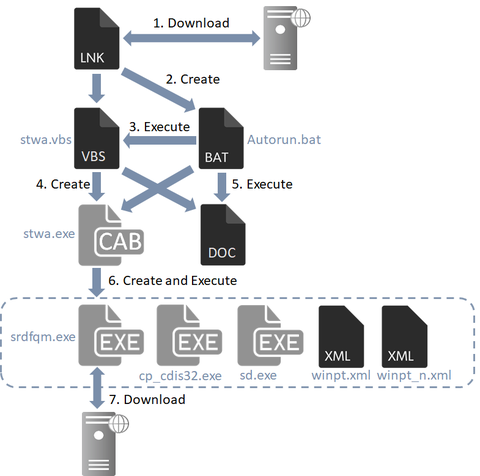
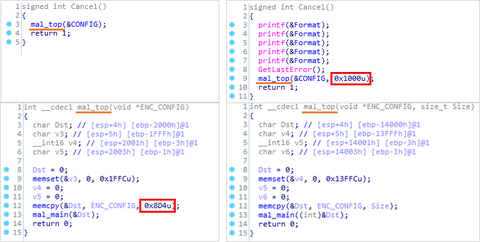
Beginning in April 2019, JPCERT/CC has been observing attacks where targeted emails are distributed to Japanese organisations, aiming to convince recipients to download a malicious shortcut file. These emails contain a link to a shortcut file on a cloud service. When this shortcut file is executed, a downloader launches. This article is to describe the details of the downloader and the behaviour that follows. How the downloader is launched The...
-
Our past article has presented a bug in malware “TSCookie”, which is reportedly used by BlackTech attack group. This article is to update the features of the malware. Even after we published the blog article in October 2018, the adversary had continued using the malware as it was. Just in May 2019, we confirmed that the malware had its bug fixed and was used in some attack cases. Details of...