On December 3, 2025 (local time), a vulnerability allowing unauthenticated remote code execution in React Server Components (RSC) (CVE-2025-55182) was disclosed. JPCERT/CC has received multiple incident reports related to this attack. Among them, there was a case in which this vulnerability was exploited by multiple threat actors within a short period of time, resulting in multiple incidents occurring simultaneously, including website defacement. This article demonstrates how rapidly and indiscriminately attackers...
List of “Incident”
-
-
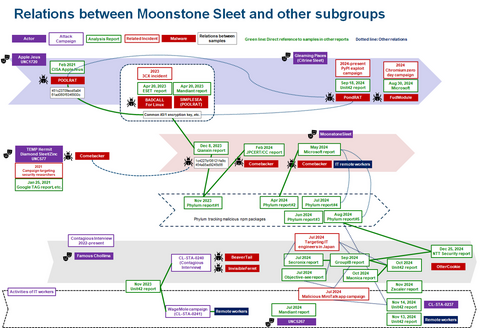
In JPCERT/CC Eyes, we previously reported on attacks conducted by Atta...
-
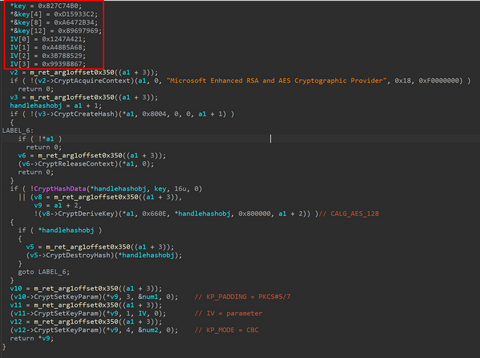
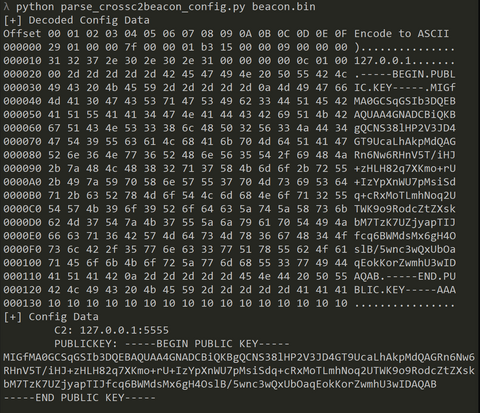
From September to December 2024, JPCERT/CC has confirmed incidents involving CrossC2, the extension tool to create Cobalt Strike Beacon for Linux OS. The attacker employed CrossC2 as well as other tools such as PsExec, Plink, and Cobalt Strike in attempts to penetrate AD. Further investigation revealed that the attacker used custom malware (hereafter referred to as "ReadNimeLoader") as a loader for Cobalt Strike. Information submitted to VirusTotal suggests that this...
-
JPCERT/CC Eyes previously introduced the malware SPAWNCHIMERA and Dslo...
-
*Please note that this article is a translation of the Japanese versio...
-
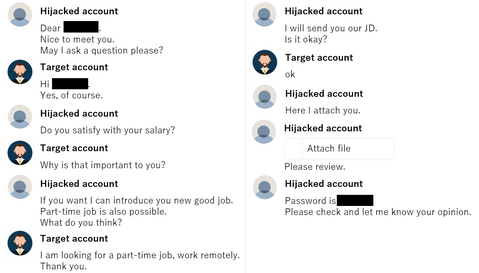
There have recently been reports of unauthorized access in Japan, usin...
-
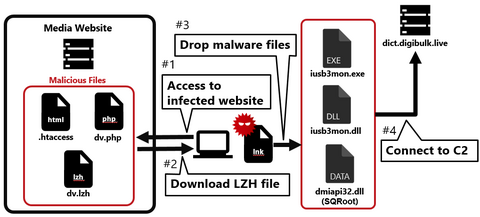
Continuing from the previous article, Part 2 covers another case of a watering hole attack. This time, we will look at the case of a media-related website exploited in 2023. Flow of the attack Figure 1 shows the flow of the watering hole attack. When someone accesses the tampered website, an LZH file is downloaded, and when they execute the LNK file in the LZH file, their PC becomes infected...
-
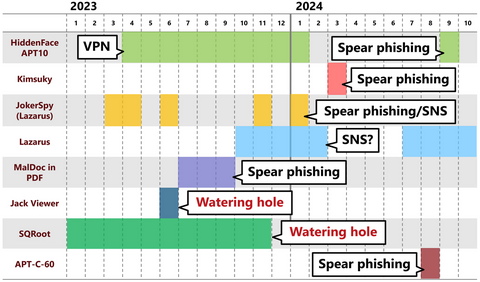
Nowadays, many people probably recognize exploit of vulnerabilities in publicly exposed assets such as VPN and firewalls as the attack vector. In fact, many security incidents reported to JPCERT/CC also involve such devices. This is because vulnerabilities in VPN devices are exploited not only by APT groups but also by many other groups such as ransomware actors and cyber crime actors, and the number of incidents is high accordingly. As...
-
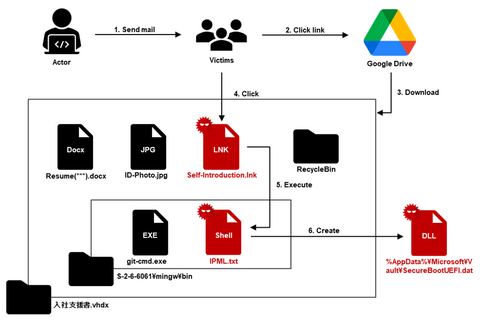
JPCERT/CC has confirmed an attack against an organization in Japan in ...
-
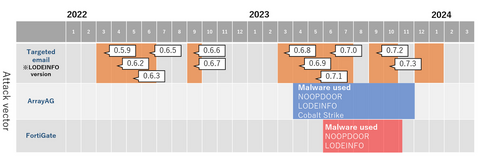
JPCERT/CC has been observing attack activities by MirrorFace LODEINFO ...