JPCERT/CC is continuously investigating the activities by Lazarus. In ...
List of “Malware”
-
-
Some types of malware use DGA, obfuscate destination information, or c...
-
To conceal malware’s features, attackers sometimes encode the malware and decode it only when they execute it. In such cases, the encoded malware is loaded and executed by a program called loader. In this way, an attacker can split the malware into a loader and encoded malware. Minimizing the loader’s features and hiding important features of the malware make detection on infected hosts more difficult. Among such loaders, this article...
-
Malware targeting Windows OS (PE format) has a variety of obfuscation and packing techniques in place so that they complicate the code analysis processes. On the other hand, there are only a few types of packing techniques for Linux-targeting malware (ELF format), and it is mainly UPX-based. This blog article explains the details of Anti-UPX Unpacking technique, which is often applied to Linux-targeting malware. Malware with Anti-UPX Unpacking Technique The...
-
Since around 2018, JPCERT/CC has observed an increasing number of mali...
-
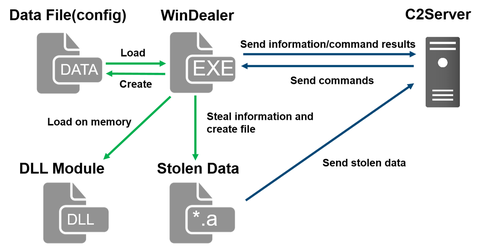
During JSAC2021 on 28 January 2021, there was a presentation about an attack group LuoYu, which targets Korean and Japanese organisations since 2014 [1][2]. Recently, JPCERT/CC came across malware WinDealer used by this group. This article introduces some findings of our analysis.Malware WinDealer overviewWinDealer steals information of an infected PC and sends it to a C2 server as described in Figure 1.Figure 1: Malware WinDealer behaviour overviewOnce launched, the malware...
-
An attack group BlackTech has been actively conducting attacks against Japanese organisations since 2018. Although it is not as prominent as before, JPCERT/CC is still seeing some cases as of now. This article introduces the details of the malware Gh0stTimes, which is used by this group. Gh0stTimes overview Gh0stTimes is customised based on Gh0st RAT and has been used in some attack cases since 2020. Figure 1 shows the comparison...
-
The functions and evolution of malware LODEINFO have been described in our past articles in February 2020 and June 2020. Yet in 2021, JPCERT/CC continues to observe activities related to this malware. Its functions have been expanding with some new commands implemented or actually used in attacks. This article introduces the details of the updated functions and recent attack trends. LODEINFO versions At the time of the last blog update,...
-
Lazarus (also known as Hidden Cobra) is known to use various kinds of malware in its attack operations, and we have introduced some of them in our past articles. In this article, we present two more; Torisma and LCPDot. Torisma overview Torisma downloads and executes modules from external servers, and its infection spreads via malicious Word files [1]. Torisma samples that JPCERT/CC has analysed are DLL files and executed as...
-
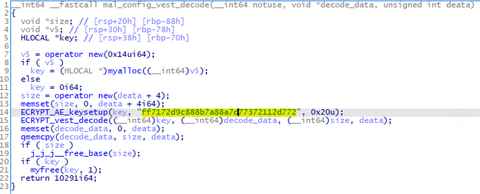
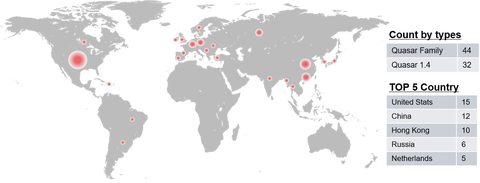
Quasar [1] is an open source RAT (Remote Administration Tool) with a variety of functions. This is easy to use and therefore exploited by several APT actors. JPCERT/CC has confirmed that a group called APT10 used this tool in some targeted attacks against Japanese organisations. As Quasar’s source code is publicly available, there are many variants of this RAT seen in the wild (referred to as “Quasar Family” hereafter). Some...